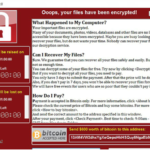
 What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/
What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/
Read More:
WannaCry FAQ

