If your customers notice something’s wrong before your own security specialists do, you’ve failed on multiple levels When Benjamin Franklin said, “Time is money,” he gave the world an aphorism that would be quoted frequently by businesspeople for more than 200 years. For all his wit and insight, of course, Franklin could never have foreseen the many scenarios for which his pithy observation would come to apply. It turns out that among the most relevant applications of the quote in today’s digitally driven world is in the realm of cybersecurity. Why? Because for organizations that suffer a cyberattack, a slow response can prove very costly. In an early 2017 survey of more than 1,000 IT and business decision makers, nearly two-thirds of the respondents said they could lose $100,000 per hour or more if a distributed denial of service (DDoS) attack were to disrupt their peak business periods. On the bright side, 8 in 10 of the organizations responding to the Neustar-sponsored survey said they’ve learned about new DDoS attacks from their internal security and IT teams – at least sometimes. Less encouraging is the fact that 40% also said they have, at times, received their first notification of attacks from their customers. If your customers notice something’s wrong before your own security specialists do, you’ve failed on multiple levels. The ideal DDoS defense is to recognize an emerging threat and neutralize it before it even gains a foothold – and certainly before your customers experience any negative impacts. If customers start complaining about an inability to access your websites or other services, you’ve already started to lose money before you’re even aware of the problem. Beyond causing staggering monetary losses for many corporations, successful DDoS attacks can alienate customers and shake their confidence in the victim’s ability to secure its own systems. By extension, customer then worry about the security of their own interactions with the company, and about the safety of any customer data the company may hold. The resulting customer churn and reduced loyalty can result in additional financial consequences. In this regard, another Franklin quote sadly holds true: “It takes many good deeds to build a good reputation, and only one bad one to lose it.” Fortunately, there are many security tools and services available to organizations that decide to be proactive in their DDoS defenses. As is often the case when it comes to cybersecurity, the most effective defenses will leverage a layered approach. The first-level of defense for DDoS attacks ideally will be provided by the network or Internet service provider, which is often the first to see – and block – suspicious network activity. For those attacks that still manage to get through, companies need their own DDoS identification and mitigation solutions. Some of those solutions may be on-premises appliances and other controls, while others may be provided by cloud-based or managed security services providers. Such “security-as-a-service” offerings are rapidly gaining in popularity, especially if an attack’s scale exceeds the capabilities of the on-premises protections. In short, there’s little excuse to be reactive, rather than proactive, when it comes to DDoS defenses. And, yes, Franklin once again provides some sage advice to those who may be too cavalier in their attitudes about DDoS threat. “By failing to prepare, you are preparing to fail.” Source: http://www.csoonline.com/article/3200084/leadership-management/if-you-learn-of-ddos-attacks-from-customers-you-ve-already-failed.html
See the original article here:
If You Learn of DDoS Attacks from Customers, You’ve Already Failed


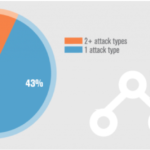 Information security company Verisign just published its Distributed Denial of Trends Report for Q1 2017. This report talks about changes in the frequency, size, and type of DDoS attack that the company has observed over the first few months of this year. The main takeaway is this: The number of DDoS attacks has plunged by 23 percent compared to the previous quarter. That’s good! However, the average peak attack size has increased by almost 26 percent, making them vastly more potent at taking down websites and critical online infrastructure. That’s bad. The report also notes that attacks are sophisticated in nature, and use several different attack types to take down a website. While 43 percent use just one attack vector, 25 percent use two, and six percent use five. This, obviously, makes it much more difficult to mitigate against. Verisign’s report also talks about the largest DDoS attack observed by the company in Q1. This was a multi-vector attack that peaked at 120 Gbps, and with a throughput of 90 Mpps. Per the report: This attack sent a flood of traffic to the targeted network in excess of 60 Gbps for more than 15 hours. The attackers were very persistent in their attempts to disrupt the victim’s network by sending attack traffic on a daily basis for over two weeks. The attack consisted primarily of TCP SYN and TCP RST floods of varying packet sizes and employed one of the signatures associated with the Mirai IoT botnet. The event also included UDP floods and IP fragments which increased the volume of the attack. So, in short. The attackers were using several different attack types, and they were able to sustain the attack over a long period of time. This shows the attacker has resources, either to create or rent a botnet of that size, and to sustain an attack over two weeks. The fact that DDoS attacks have increased in potency is hardly a surprise. They’ve been getting bigger and bigger, as bad actors figure out they can easily rope insecure Internet of Things (IoT) devices into their botnets. The Mirai botnet, for example, which took down Dyn last year, and with it much of the Internet, consisted of hundreds of thousands of insecure IoT products. The main thing you can gleam from the Verisign report is that DDoS attacks are increasingly professional, for lack of a better word. It’s not 2005 anymore. We’ve moved past the halcyon days of teenagers taking down sites with copies of LOIC they’d downloaded off Rapidshare. Now, it’s more potent. More commoditized. And the people operating them aren’t doing it for shits and giggles. Source: https://thenextweb.com/insider/2017/05/24/report-ddos-attacks-are-less-common-but-theyre-bigger/#.tnw_RJHfi1AZ
Information security company Verisign just published its Distributed Denial of Trends Report for Q1 2017. This report talks about changes in the frequency, size, and type of DDoS attack that the company has observed over the first few months of this year. The main takeaway is this: The number of DDoS attacks has plunged by 23 percent compared to the previous quarter. That’s good! However, the average peak attack size has increased by almost 26 percent, making them vastly more potent at taking down websites and critical online infrastructure. That’s bad. The report also notes that attacks are sophisticated in nature, and use several different attack types to take down a website. While 43 percent use just one attack vector, 25 percent use two, and six percent use five. This, obviously, makes it much more difficult to mitigate against. Verisign’s report also talks about the largest DDoS attack observed by the company in Q1. This was a multi-vector attack that peaked at 120 Gbps, and with a throughput of 90 Mpps. Per the report: This attack sent a flood of traffic to the targeted network in excess of 60 Gbps for more than 15 hours. The attackers were very persistent in their attempts to disrupt the victim’s network by sending attack traffic on a daily basis for over two weeks. The attack consisted primarily of TCP SYN and TCP RST floods of varying packet sizes and employed one of the signatures associated with the Mirai IoT botnet. The event also included UDP floods and IP fragments which increased the volume of the attack. So, in short. The attackers were using several different attack types, and they were able to sustain the attack over a long period of time. This shows the attacker has resources, either to create or rent a botnet of that size, and to sustain an attack over two weeks. The fact that DDoS attacks have increased in potency is hardly a surprise. They’ve been getting bigger and bigger, as bad actors figure out they can easily rope insecure Internet of Things (IoT) devices into their botnets. The Mirai botnet, for example, which took down Dyn last year, and with it much of the Internet, consisted of hundreds of thousands of insecure IoT products. The main thing you can gleam from the Verisign report is that DDoS attacks are increasingly professional, for lack of a better word. It’s not 2005 anymore. We’ve moved past the halcyon days of teenagers taking down sites with copies of LOIC they’d downloaded off Rapidshare. Now, it’s more potent. More commoditized. And the people operating them aren’t doing it for shits and giggles. Source: https://thenextweb.com/insider/2017/05/24/report-ddos-attacks-are-less-common-but-theyre-bigger/#.tnw_RJHfi1AZ