Cybercriminals had a very good year in 2016 — and we all paid the price. These digital bandits became more ambitious and more creative and that resulted in a year marked by “extraordinary attacks,” according to the 2017 Internet Security Threat Report from Symantec. “Cyber crime hit the big time in 2016, with higher-profile victims and bigger-than-ever financial rewards,” the report concluded. The bad guys made a lot of money last year,” said Kevin Haley, director of Symantec Security Response. “They keep getting better and more efficient at what they do; they managed to fool us in new and different ways.” Some of the damage done last year: Data breaches that exposed 1.1 billion identities, up from 564 million in 2015 More ransomware attacks with higher extortion demands Some of the biggest distributed denial of service (DDoS) attacks on record, causing “unprecedented levels of disruption” to internet traffic. Cyber thieves have traditionally made their money by stealing a little bit from a lot of people. They’ve focused on raiding individual bank accounts or snagging credit card numbers. But that’s starting to change, as criminal gangs are going after the banks themselves, the reported noted. “It takes a lot of sophistication and a lot of patience — you really need to understand what you’re doing — but if you can break into the bank, you can steal millions of dollars at once,” Haley told NBC News. “It’s like those big heist movies we see. Cybercriminals are now pulling off these big heists with specialists, sophisticated tools and some great imagination in what they do.” Email Is Back as the Favorite Way to Attack Malicious email is now “the weapon of choice” for a wide range of cyber attacks by both criminals and state-sponsored cyber espionage groups. Symantec found that one in 131 emails was malicious last year, up dramatically from 2015, and the highest rate in five years. Email attacks are back because they work, the report noted: “It’s a proven attack channel. It doesn’t rely on vulnerabilities, but instead uses simple deception to lure victims into opening attachments, following links, or disclosing their credentials.” Remember: It was a simple spear-phishing attack — a spoofed email with instructions to reset an email password — that was used to attack the Democrats in the run-up to the 2016 presidential election. “People are comfortable with email. They read it,” Haley said. “Even when people are suspicious, the bad guys know how to fool us.” Most malicious email is disguised as a notification — most commonly an invoice or delivery notice from a well-known company. In many cases, the malicious attachment is a simple Word document. Most people don’t think of a Word file as dangerous or malicious. And for the most part, they’re not. But these clever crooks have a “social engineering” trick to get you to do what they want. The information on the malicious document is deliberately unreadable, which is unsettling. A note tells the intended target to click a button that will make it possible to read the message. Do that, and you’ve turned on the macros that allow the malware to download onto your computer. Just like that, they’ve got you. Ransomware: Everyone Is at Risk Ransomware attacks have grown more prevalent and destructive, which is why Symantec called them “the most dangerous cyber crime threat facing consumers and businesses in 2016.” The number of ransomware infections detected by Symantec grew by 36 percent last year, skyrocketing from 340,000 in 2015 to 463,000 in 2016. And it’s expected to remain a major global threat this year. This devious malware locks up computers, encrypts the data and demands payment for the unique decryption key. In the blink of an eye, entire computer systems can become useless. Ransomware is most often hidden in innocuous-looking email, such as a bogus delivery notice or invoice. For-hire spam botnets make it easy for the crooks to send hundreds of thousands of malicious emails a day for very little cost. It’s a lucrative crime. The average ransomware demand shot up from $294 in 2015 to $1,077 last year. Research by Symantec’s Norton Cyber Security Insight team found that 34 percent of the victims worldwide pay the ransom. In the U.S. that jumps to 64 percent. This willingness to pay could explain why America remains their prime target, with more than one-third of all ransomware attacks. New Targets: The Cloud, Internet of Things and Mobile Devices From security cameras and baby monitors to thermostats and door locks, our households are now filled with devices connected to the internet. Weak security makes the Internet of Things (IoT) an easy target for all sorts of malicious activity. Most of these devices have simple and common default passwords, such as “admin” or “123456,” that can’t be changed or are rarely changed. Last year, cybercriminals harnessed the power of these connected devices to do some serious damage. Tens of thousands of infected IoT devices, such as security cameras and routers, became a powerful botnet that launched high-profile (DDoS) attacks that successfully shut down websites. The DDoS attack in October against Dyn, a cloud-based hosting service, disrupted many of the world’s leading websites, including Netflix, Twitter and PayPal. Cloud attacks have become a reality and Symantec predicts they will increase this year. “A growing reliance on cloud services should be an area of concern for enterprises, as they present a security blind spot,” the report cautioned. Symantec said it saw a two-fold increase in attempted attacks on IoT devices over the course of last year. Cyber criminals are also targeting mobile devices. Most of the attacks are focused on the Android operating system, which has the largest share of the mobile market. Attacks on iOS devices remain relatively rare. Improvements in Android’s security architecture have made it increasingly difficult to infect mobile phones or to capitalize on successful infections, the report noted. But the volume of malicious Android apps continues to increase, growing by 105 percent last year. The 2017 Internet Security Threat report can be downloaded from Symantec’s website. Want to fight back? Norton has a list of tips on how to protect yourself and your devices on its website. Source: http://www.nbcnews.com/tech/tech-news/cybercriminals-breached-over-billion-accounts-last-year-n753131
Visit site:
Cybercriminals Breached Over a Billion Accounts Last Year


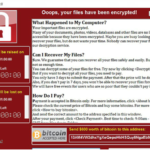 What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/
What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/ 
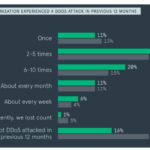 Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/