Small businesses face a range of cyber threats daily and are often more vulnerable than the larger organisations. Small businesses that see themselves as too small to be targeted by cyber criminals are putting themselves at direct risk. In fact, small businesses are at an equal, if not greater risk of being victims of cyber crime – two thirds of small UK firms were attacked by hackers between 2014-2016, according to a report from the Federation of Small Businesses. Cyber crime can cause massive damage to a young business’s reputation, result in loss of assets and incur expenses to fix the damage caused. These attacks could mean the difference between cutting a profit or going bust. Legal action could also be taken if businesses are found to have failed to put proper safeguards in place. When new data protection laws are introduced in 2018 under GDPR, complacent businesses risk fines of up to £17 million or 4% of annual turnover (whichever is higher) if they suffer a data breach. So what can small businesses do to protect themselves and the sensitive data of their customers? These are 7 nightmare cyber security threats and how to secure against them. Threat 1: internal attacks This shouldn’t come as a surprise to readers, but internal attacks are one of the largest cyber security threats facing small businesses today. Rogue employees, especially those with access to networks, sensitive data or admin accounts, are capable of causing real damage. Some theories even suggest that the notorious 2014’s Sony Pictures hack – typically linked to North Korea – was actually an insider attack. To reduce the risk of insider threats, businesses must identify privileged accounts – accounts with the ability to significantly affect or access internal systems. Next, terminate those that are no longer in use or are connected with employees no longer working in the business. Businesses can also implement tools to track the activity of privileged accounts. This allows for a swift response if malicious activity from an account is detected before the damage can be dealt. Threat 2: phishing and spear phishing Despite constant warnings from the cyber security industry, people still fall victim to phishing every day. As cyber crime has become well-funded and increasingly sophisticated, phishing remains one of the most effective methods used by criminals to introduce malware into businesses. Spear phishing is a targeted form of phishing in which phishing emails are designed to appear to originate from someone the recipient knows and trusts – like senior management or a valued client. To target victims deemed ‘high value’ — i.e. those with access to privileged accounts — cyber criminals may even study their social media to gain valuable insights which can then be used to make their phishing emails appear highly authentic. If an employee is tricked by a malicious link in a phishing email, they might unleash a ransomware attack on their small business. Once access is gained, ransomware quickly locks down business computers as it spreads across a network. Until a ransom is paid, businesses will be unable to access critical files and services. To mitigate the risk posed by phishing – and ransomware – organisations must ensure staff are aware of the dangers and know how to spot a phishing email. Businesses must also ensure they have secure backups of their critical data. Because ransomware locks down files permanently (unless businesses want to cough up the ransom) backups are a crucial safeguard to recover from the hack. But as ransomware attacks are on the rise, prevention remains better than treatment. Education is the best way of ensuring protection for small businesses. Threat 3: a dangerous lack of cyber security knowledge Entire cyber security strategies, policies and technologies are worthless if employees lack cyber security awareness. Without any kind of drive to ensure employees possess a basic level of cyber security knowledge, any measure or policy implemented will be undermined. A well-targeted spear phishing email could convince an employee to yield their password and user information. An IT team can’t be looking over everyone’s shoulders at once. Because of this, education and training are essential to reduce the risk of cyber crime. Some employees may not know (or care enough) to protect themselves online, and this can put businesses at risk. Hold training sessions to help employees manage passwords (hint: two-factor authentication for business accounts) and identify phishing attempts. Then provide support to ensure employees have the resources they need to be secure. Some small businesses will also consider up-skilling members of their IT teams in incident handling, often through popular GCIH training from security vendor GIAC. Incident handling professionals are able to manage security incidents as they happen, and speed the process of recovery if hacks do occur. Ultimately, even a basic level of knowledge and awareness could mean the difference between being hacked or avoiding the risk altogether. Threat 4: DDoS attacks Distributed Denial of Service (DDoS) attacks have overwhelmed some of the largest websites in the world, including Reddit, Twitter, and Netflix. DDoS attacks, which ambush businesses with massive amounts of web traffic, slow websites to a crawl and, more often than not, force crucial services offline. If a small businesses relies on a website or other online service to function, the outages caused by DDoS attacks will be catastrophic. Most DDoS attacks last between 6-24 hours and cause an estimated £30,000 per hour, according to data from Incapsula, a DDoS prevention firm. Whilst businesses can’t stop a website or service being targeted in a DDoS attack, they can work to absorb some of the increased traffic, giving them more time to form a response or filter out the spam data. Ensuring there is extra bandwidth available, creating a DDoS response plan in the event of an attack or using a DDoS mitigation service are all great steps towards reducing the impact of an attack. But that’s just scratching the surface of DDoS mitigation – here are more ways to prevent a DDoS attack. Threat 5: malware Malware is a blanket term that encompasses any software that gets installed on a machine to perform unwanted tasks for the benefit of a third party. Ransomware is a type of malware, but others exist, including spyware, adware, bots and Trojans. To prevent malware from taking hold, businesses should invest in solid anti-virus technology. Plus, operating systems, firewalls and firmware, and previously mentioned anti-virus software must be kept up-to-date. If services are outdated or not updated regularly, businesses are at a serious risk. Just look at the damage caused when malware infected the UK’s National Health Service through an exploit within an outdated version of Windows XP. And that was just one of the high profile targets affected by the global WannaCry ransomware attack. Threat 6: SQL Injection Almost every business relies on websites to operate and many depend entirely on the service they provide online. However, poorly secured websites could be wide open to data theft by cyber criminals. Of the many attacks that can be staged against a website, SQL injection is amongst the most dangerous and even the largest companies fall victim to it. SQL injection refers to vulnerabilities that allow hackers to steal or tamper with the database sitting behind a web application. This is achieved by sending malicious SQL commands to the database server, typically by inputting code into forms – like login or registration pages. It takes a few well-calculated steps to protect against SQL injection. As a precaution, businesses should assume all user-submitted data is malicious, get rid of database functionality that isn’t needed and consider using a web application firewall. For a closer look at SQL injection, take a look at this documentation from Cisco. Properly preventing SQL injection is primarily a responsibility for a web development or security team, but the change has to be driven from the top. Still not convinced? Take a look at this video from Computerphile to see how effective and dangerous SQL injection can be. Threat 7: BYOD Businesses are vulnerable to data theft, especially if employees are using unsecure mobile devices to share or access company data. As more small businesses make use of bring your own device (BYOD) technology, corporate networks could be at risk from unsecured devices carrying malicious applications which could bypass security and access the network from within the company. The solution is nailing down a defined BYOD policy. A comprehensive BYOD policy educates employees on device expectations and allow companies to better monitor email and documents that are being downloaded to company-owned devices. Ensure employee-owned devices can access the business network through a VPN which connects remote BYOD users with the organisation via an encrypted channel. A VPN is crucial if employees are using public WiFi networks to access business data. Public Wi-Fi is notoriously unsecure and provides little protection against criminals that might be watching the transfer of sensitive data. If an attacker does capture encrypted VPN traffic they will only see incomprehensible characters going from you to a VPN server – meaning no sensitive data is leaked. Source: http://www.information-age.com/7-nightmare-cyber-security-threats-smes-secure-123466495/
See more here:
7 nightmare cyber security threats to SMEs and how to secure against them


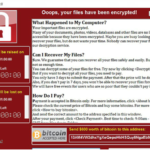 What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/
What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/