Major news sites in France including Le Monde and Le Figaro went down yesterday in the fallout of a DDoS attack. Many of the biggest French news sites were hit by a DDoS attack on a Portland, Oregon cloud computing company – Cedexis. The attack caused the sites to go dark. Dr Malcolm Murphy, technology director at Infoblox said “This is the latest in a run of cyber attacks in France – only a week ago newly elected French President Macron’s emails were leaked by hackers. This latest attack highlights the importance of organisations prioritising cyber defences at a time when commonly deployed cyberattacks are being used to disrupt both political processes and organisations.” Bloomberg reported that Le Monde and Le Figaro were two of the websites that crashed. “At approximately 2 p.m. GMT (7 a.m. Pacific time), the Cedexis infrastructure came under a unique and sophisticated distributed denial of service (DDOS) attack,” Cedexis said in a written statement. “This attack caused a partial but widespread outage that affected many of our customers. Our customers are our number one priority and at this time, the attack is being mitigated, and services are being restored.” DDoS attacks have grown in prevalence as more and more unsecure Internet of Things (IoT) devices have entered the market. Murphy suggested that “DDoS attacks in particular are growing in both frequency and sophistication. Whilst there is no easy solution to securing DNS, there are a few steps that an organisation’s IT team can take to help mitigate and respond to DNS-based DDoS attacks.” “Organisations who don’t know their query load will never know when they’re under attack. By using statistical support, administrators can help analyse their data for attack indicators. Whilst it may not always be clear what an attack looks like, anomalies will be more easily identifiable. IT teams should also continually scrutinise internet-facing infrastructure for single points of failure by going beyond external authoritative name servers, and checking on the switch and router interactions, firewalls, and connections to the internet.” Source: http://www.information-age.com/major-french-news-sites-victim-ddos-attack-123466206/
Category Archives: Security Websies
Another IoT botnet has been found feasting on vulnerable IP cameras
Children, please welcome Persirai to the class Researchers have discovered yet another IoT botnet.…
Read the original post:
Another IoT botnet has been found feasting on vulnerable IP cameras
FCC blames DDoS for weekend web lockout
Not down to people trying to file comments on issues rhyming with wetsuit balloty, it insists Vid Problems faced by consumers hoping to submit comments to the Federal Communications Commission over the weekend were caused by a denial of service attack, the US government agency admits.…
Bondnet botnet goes after vulnerable Windows servers
A botnet consisting of some 2,000 compromised servers has been mining cryptocurrency for its master for several months now, “earning” him around $1,000 per day. GuardiCore researchers first spotted it in December 2016, and have been mapping it out and following its evolution since then. The’ve dubbed it Bondnet, after the handle its herder uses online (“Bond007.01”). Compromised Windows servers serve different functions Bondnet’s main reason of being is the mining of cryptocurrencies: primarily Monero, … More ?
See more here:
Bondnet botnet goes after vulnerable Windows servers
DDoS attacks could cost enterprises over $2.5 million in revenue
A new report from information services specialist Neustar looks at the frequency and cost of DDoS attacks and what is being done to counter the threat. In terms of revenue loss, three percent of organizations report average revenue loss of at least $250,000 per hour, with 51 percent taking at least three hours to detect an attack and 40 percent taking at least three hours to respond, that means an attack could cost over $2.5 million. Attacks are getting larger too, with 45 percent of DDoS attacks delivered at more than 10 gigabits per second (Gbps), and 15 percent of attacks being at least 50 Gbps, almost double the number reported last year. In total 849 out of 1,010 organizations surveyed were attacked, with no particular industry spared, an increase of 15 percent since 2016. 86 percent of those attacked were also hit more than once. Also customers are often the first to spot a problem, with 40 percent of respondents reporting receiving attack alerts from customers, up from 29 percent in 2016. “Distributed Denial of Service (DDoS) attacks are the zeitgeist of today’s Internet,” says Barrett Lyon, pioneer of the DDoS defense industry and head of research and development at Neustar Security Solutions. “The question organizations must ask now is how they are prepared to manage these highly disruptive events. Are they prepared for the bad day where their customers call and ask why the website is down?” Ransomware now often goes hand in hand with DDoS too, the number of instances of this increased 53 percent since 2016. 51 percent of attacks involved some sort of loss or theft with a 38 percent increase year on year in thefts of customer data, financial and intellectual property. Whilst almost all organizations surveyed have some form of DDoS protection in place, 90 percent say they are investing more than they did a year ago and 36 percent think they should be investing more still. Source: https://betanews.com/2017/05/04/ddos-attack-cost/
Read More:
DDoS attacks could cost enterprises over $2.5 million in revenue
DDoS attack size doubles, but 40% are still reported by customers
While the headline record breaking attack size goes up every year, the long tail of average attack size has also doubled in the past year to reach 50 Gps according to Neustar’s fourth annual Worldwide DDoS Attacks and Cyber Insights Research Report. However, the increased average is partly put down multiple 500 Gbps+ attacks from IoT botnets, one of which exceeded 680 Gbps peak size. The report records that nearly half (45 percent) of DDoS attacks were more than 10 Gbps and 15 percent of attacks were at least 50 Gbps, showing that volumetric attacks are getting larger. And the average cost of DDoS attacks has also gone up, now costing an organisation almost £2 million (£1.9 million) in revenue. Neustar’s report is based on responses from 1,010 CISOs, CSOs, CTOs security directors and managers. Out of 1010 organisations, 849 were attacked – with no particular industry spared. Eighty-six percent (727) of those attacked were hit more than once. Forty percent of respondents reported receiving attack alerts from customers, up from 29 percent in 2016, demonstrating just how unprepared we are when dealing with this threat. An average revenue loss of at least US$250,000 (£190,000) per hour was reported by 43 percent of organisations, with 51 percent taking at least three hours to detect an attack and 40 percent taking at least that amount of time to respond. Instances of ransomware increased 53 percent since 2016. Half of the attacks involved some sort of loss or theft with a 38 percent increase year over year in customer data, financial and intellectual property thefts. Nearly all (99 percent) organisations have some sort of DDoS protection in place, but 90 percent are investing more than they did a year ago. More than a third (36 percent) think they should be investing even more. Showing that the year is off to a fast start, the research is already seeing significant increases in average attack size and variety of attack vectors even though Q1 is generally considered “pre-season” with most attacks traditionally happening in the shopping season in the run up to Christmas. The new hot attack trends for 2017 include Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP). The report explains how CLDAP Reflection attacks come from botnets that target exposed public facing LDAP servers by exploiting UDP’s inherent stateless nature. These attacks originate from port 389 (LDAP’s UDP port), however they are not always concentrated on attacking a specific source port. Although LDAP is more prevalent on internal networks, attackers have been increasingly using this form of attack across the internet and have now increased to what the Neustar describes as a point of significance. The largest CLDAP attack mitigated this year by Neustar Security Operations had a peak size of 20.9 Gbps/2.1 Mpps, targeted 9 different ports, used UDP protocols and lasted 14 minutes. Growth in these attacks is attributed to the near eradication of SSDP attacks, thus attackers looking for quick ramping volumetric menaces have gravitated to CLDAP. Also attackers may launch LDAP-based attacks using brute force to saturate and neutralise authentication systems and security infrastructure components. GRE-based attacks target private connections and are used many times to disrupt a DDoS target’s connection to its protection provider explains the report. GRE tunnels are typically used to connect infrastructures and facilitate contaminated traffic flows into DDoS mitigation clouds. Attackers tend to understand this and thus, these types of attacks are increasingly being seen and mitigated. Neustar points out that typically stopping a GRE flood without completely shutting down legitimate traffic requires surgical rate limiting (specific packet size ranges, source and destinations, etc.) or specific white/black lists. Attackers continue to launch more sophisticated attacks to penetrate organisation’s defences as multi-vector attacks have become the nearly universal experience for Neustar mitigation operations, with DDoS often a distraction for the main attack. “Distributed Denial of Service (DDoS) attacks are the zeitgeist of today’s internet,” said Barrett Lyon, head of research and development at Neustar Security Solutions in a news release. “The question organisations must ask now is how they are prepared to manage these highly disruptive events. Are they prepared for the bad day where their customers call and ask why the website is down?” “We have to have confidence that our website infrastructure can stand up to DDoS attacks and attacks on our DNS infrastructure, which is unfortunately a constant threat,” said Chris Matthews, head of operations at Experian Data Quality in a release. Neustar has expanded its network capacity to 3 Tbps, and is increasing it to 10 Tbps enabling it to absorb more attacks and stop more complex versions of attack combinations. Neustar’s advice to companies in its report is: assess, plan, test, and communicate within the organisation because the attacks are going to keep coming. Invest wisely to right size your DDoS defences. Not all DDoS defences are made equally. Some of the experienced gained by attackers last year was an operational understanding of DDoS defence business models. With long, large attacks come big expenses for targeted organisations and in several extreme cases, removal from protective cover. Attackers are figuring out the economics of DDoS defence and using it to their advantage. This is an important consideration when evaluating security investments. Source: https://www.scmagazineuk.com/ddos-attack-size-doubles-but-40-are-still-reported-by-customers/article/654480/
Read the article:
DDoS attack size doubles, but 40% are still reported by customers
Malware Hunter: Find C&C servers for botnets
Recorded Future and Shodan released Malware Hunter, a specialized crawler for security researchers that explores the Internet to find computers acting as remote access trojan (RAT) command and control centers. What Malware Hunter does Malware Hunter unearths computers hosting RAT controller software that remotely controls malware-infected computers and instructs them to execute malicious activities such as recording audio, video, and keystrokes on a victim’s machine. Using command and control servers, attackers can launch widescale attacks … More ?
Read more here:
Malware Hunter: Find C&C servers for botnets
DDoS attacks: $100,000 per hour is at risk during peak revenue generation periods
Neustar and Harris Interactive conducted global, independent research of 1,010 directors, managers, CISOs, CSOs, CTOs, and other c-suite executives to find out how DDoS attacks affect their organizations and what measures are in place to counter these threats. The respondents span many industries, including technology, financial services, retail, healthcare and energy. “DDoS attacks are the zeitgeist of today’s Internet,” said Barrett Lyon, pioneer of the DDoS defense industry and Head of Research and Development at … More ?
Continue Reading:
DDoS attacks: $100,000 per hour is at risk during peak revenue generation periods

The average DDoS attack cost for businesses rises to over $2.5m
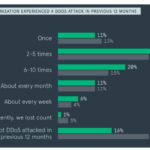 Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
See the article here:
The average DDoS attack cost for businesses rises to over $2.5m
Discovery of 8,800 servers sends warning to Asian cybercriminals
In one of the more curious cybercrime announcements of recent times, Interpol’s Asian centre says it has “identified” 8,800 servers used as command & control (C2) for all sorts of bad things including DDoS attacks and distributing ransomware and spam. You read that correctly. Interpol hasn’t disrupted these servers, merely passed information on their whereabouts and malevolent purpose to police forces in eight countries, including Malaysia, Myanmar, Philippines, Singapore, Thailand and Vietnam. The operation isolated the C2 by working back from 270 websites infected with malware, assisted by intelligence and know-how from a number of cybersecurity companies. Added Interpol: Among them were several government websites which may have contained personal data of their citizens. Individual criminals were also identified in Nigeria and Indonesia, which hints that arrests might be forthcoming. It sounds like a modest achievement until you remember that Asia is a favoured geography for malware hosting infrastructure (including servers used to attack other parts of the globe) but, historically, underwhelming levels of cross-border co-operation. If action at national level in the countries affected eventually sees the servers disappear forever, it’s not something to be sniffed at. The bigger picture is that Interpol’s Global Complex for Innovation (IGCI), opened in Singapore in 2015, is signalling that it’s up and running and able to make a difference – however emblematic. Cybercrime can be mitigated by technology, of course, but few doubt importance of going after it at the roots, both the servers and the people who run and profit from them. It’s a massive challenge because these people can base themselves anywhere in the world, and introducing legal hazard into their lives requires the sort of co-operation police forces and governments aren’t used to. Founded as long ago as 1923 as the International Criminal Police Commission (ICPC), Interpol is turning out to be a useful tool in the battle against cybercrime. Cybersecurity companies like it because its regional centres act as an independent broker that allows them to put aside commercial considerations. Police forces value it because it means they can have a relationship with one centre instead of possibly dozens of national operations. But its biggest significance is it gets the private and public sectors to work together, the former with intel and the latter with legal authority. Recent Interpol cybercrime operations have included disrupting the Avalanche botnet late last year, and the takedown of the Simda botnet two years ago. Between times were the arrests of individuals accused of being behind the infamous DD4BC DDoS extortion racket, and a global operation across Interpol’s divisions to rid the world of the one-million strong Dorkbot botnet. Only days ago, Europol’s European Cybercrime Centre (EC3) announced it had coordinated an operation between UK and Spanish police that saw the arrest of five people accused of distributing Remote Access Trojans (RATs) and keyloggers. We should interpret the identification of 8,800 C2 servers as good PR for Interpol but also, to quote Interpol’s chief superintendent Chan, “a blueprint for future operations”. Source: https://nakedsecurity.sophos.com/2017/04/27/discovery-of-8800-c2-servers-sends-warning-to-asian-cybercriminals/
View article:
Discovery of 8,800 servers sends warning to Asian cybercriminals
