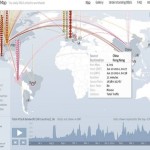
 Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/
Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/
Read more here:
Hong Kong Voting Site Suffers DDoS Attack Before Civil Referendum

