Security researchers have found yet another exploit on the Amazon cloud computing platform through the Elasticsearch distributed search engine tool. According to analysis, hackers are able to gain access to the search engine to deploy a battalion of botnets on Amazon cloud. The vulnerability should be a cause of alarm and, therefore, merits the attention of enterprises because it could manipulate Amazon cloud platforms in an attempt to launch distributed denial of service attacks against hundreds of thousands of websites. Amazon cloud users can a representational state transfer API to search various documents through Elasticsearch, an open-source search engine server built based on Java. It is more popular among cloud environments for its distributed architecture that enables multiple nodes. Researchers found security issues on the versions 1.1.x of Elasticsearch because its API scripting lacks a mechanism to authenticate access and a sandbox security infrastructure. Therefore, anyone, including hackers, can penetrate Elasticsearch just so easy. After that, attackers could carry out several malicious activities using Elasticsearch’s scripting capability such as carrying out arbitrary code on the server. As of now there is no patch coming from the developers of Elasticsearch. Nonetheless, versions 1.2.0 and up are safe from being exploited by hackers. New offshoots of Mayday Trojan for Linux has been spotted over the past week and the malware already launched DDoS attacks against targets DNS amplification. A Mayday variant was reported to be running on an Amazon server that has been compromised through the Elasticsearch exploit, though there are other platforms that could have been potentially manipulated. However, the Mayday variant did not resort to DNS amplification on the compromised EC2 instances. Instead it was used to launch attacks by flooding several websites with UDP traffic. As a result, many regional banking institutions in the United States and electronics companies in Japan had to transfer their IP addresses to DDoS mitigation service vendors. The Amazon EC2-run virtual machines were also reported to have been attacked by hackers through a CVE-2014-3120 exploit in the 1.1.x versions of Elasticsearch. Researchers observed that many commercial enterprises still use those versions. According also to security researchers, attackers have changed proof-of-concept exploit code for CVE-2014-3120 to install a Web shell developed based on Perl. A Web shell is a script that enables hackers to deploy Linux shell commands backdoor through the Web. The script was then further manipulated to download a fresh variant of the Mayday DDoS botnet. Amazon has already notified its customers about the issue. Source: http://www.techwalls.com/amazon-cloud-infested-ddos-botnets/
See more here:
Amazon cloud infested with DDoS botnets


 Hacker collective Anonymous has announced that it has taken down over a thousand of crucial Israeli websites in a huge new coordinated cyber-attack called #OpSaveGaza on 11 July and 17 July, in support of the people of Palestine. Some of the websites, such as the Tel Aviv Police Department’s online presence, are still offline two days after the distributed denial of service (DDoS) attacks, and numerous Israeli government homepages have been replaced by graphics, slogans, and auto-playing audio files made by AnonGhost, the team of hackers who coordinated the attack. The official Israeli government jobs website has had its homepage replaced by a graphic titled “Akincilar”, which is Turkish for the Ottoman Empire’s troops. Akincilar: A graphic and message protesting against the treatment of Palestinians is still replacing the homepage of certain Israeli government websites A message written in English and Turkish – presumably by Turkish hackers – and accompanied by pictures of Palestinians suffering says: “The Jerusalem cause is Muslims’ fight of honour” and says that people who fight for Palestine are “on the side of Allah”. Another Israeli government website now bears an AnonGhost graphic and lists the usernames of 38 hackers. An audio file that auto-plays when the page loads plays music and a synthesized newsreader clip, together with a message beseeching human rights organisations, hackers and activists to attack Israeli websites to become the “cyber shield, the voice for the forgotten people”. AnonGhost’s #OpSaveGaza message has been displayed on many Israeli websites Many of the websites have since been restored. The hackers have also leaked lists of Israeli government email addresses obtained by hacking websites of the Ministry of Immigrant Absorption, the Ministry of Justice, the Ministry of Culture and Sport, the Ministry of Housing and Construction and much more. Israeli websites belonging to restaurants, local businesses, associations, societies, academic foundations and even a symphony orchestra were also attacked, as well as a subdomain belonging to MSN Israel. A message on the main Pastebin page and some of the hacked websites reads : “The act of launching rockets from Gaza sector to Israhell is an acceptable and normal reaction against those pigs, it’s called Resistance and not terrorism. “Israhell never existed its only Palestine, it’s our home. If you are a Hacker, Activist, a Human Right Organisation then hack israel websites and expose to the world their crimes, show to the world how much blood is on their hands, blood of innocent children and women.” Anonymous has previously run another campaign in April targeting Israeli websites, although on a smaller scale. About 500 websites went offline during the OpIsrael campaign and the hackers released the phone numbers and email addresses of some Israeli officials. Source: http://www.ibtimes.co.uk/opsavegaza-anonymous-takes-down-1000-israeli-government-business-websites-1457269
Hacker collective Anonymous has announced that it has taken down over a thousand of crucial Israeli websites in a huge new coordinated cyber-attack called #OpSaveGaza on 11 July and 17 July, in support of the people of Palestine. Some of the websites, such as the Tel Aviv Police Department’s online presence, are still offline two days after the distributed denial of service (DDoS) attacks, and numerous Israeli government homepages have been replaced by graphics, slogans, and auto-playing audio files made by AnonGhost, the team of hackers who coordinated the attack. The official Israeli government jobs website has had its homepage replaced by a graphic titled “Akincilar”, which is Turkish for the Ottoman Empire’s troops. Akincilar: A graphic and message protesting against the treatment of Palestinians is still replacing the homepage of certain Israeli government websites A message written in English and Turkish – presumably by Turkish hackers – and accompanied by pictures of Palestinians suffering says: “The Jerusalem cause is Muslims’ fight of honour” and says that people who fight for Palestine are “on the side of Allah”. Another Israeli government website now bears an AnonGhost graphic and lists the usernames of 38 hackers. An audio file that auto-plays when the page loads plays music and a synthesized newsreader clip, together with a message beseeching human rights organisations, hackers and activists to attack Israeli websites to become the “cyber shield, the voice for the forgotten people”. AnonGhost’s #OpSaveGaza message has been displayed on many Israeli websites Many of the websites have since been restored. The hackers have also leaked lists of Israeli government email addresses obtained by hacking websites of the Ministry of Immigrant Absorption, the Ministry of Justice, the Ministry of Culture and Sport, the Ministry of Housing and Construction and much more. Israeli websites belonging to restaurants, local businesses, associations, societies, academic foundations and even a symphony orchestra were also attacked, as well as a subdomain belonging to MSN Israel. A message on the main Pastebin page and some of the hacked websites reads : “The act of launching rockets from Gaza sector to Israhell is an acceptable and normal reaction against those pigs, it’s called Resistance and not terrorism. “Israhell never existed its only Palestine, it’s our home. If you are a Hacker, Activist, a Human Right Organisation then hack israel websites and expose to the world their crimes, show to the world how much blood is on their hands, blood of innocent children and women.” Anonymous has previously run another campaign in April targeting Israeli websites, although on a smaller scale. About 500 websites went offline during the OpIsrael campaign and the hackers released the phone numbers and email addresses of some Israeli officials. Source: http://www.ibtimes.co.uk/opsavegaza-anonymous-takes-down-1000-israeli-government-business-websites-1457269 
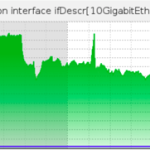 DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.
DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.