Two new reports reveal that DDoS attacks are not only getting bigger- now logged between 250 and 325 Gbps, but that these attacks often target the same organisation more than once. The business challenge presented by DDoS attacks hit the spotlight once again this morning, after a research analytics firm revealed that 35 per cent more firms were hit by attacks during 2013 than in 2012 – and with 28 per cent of logged attacks seen last years lasting two days or more. The most revealing takeout from the Neustar analysis – the firm’s second annual report, entitled `DDoS Attacks & Impact Report – 2014: The Danger Deepens’ – is that once attacked, there is an estimated 69 percent chance of a repeat attack. And whilst 31 per cent of these companies were DDoS-attacked once, over 48 percent said they had been targeted between two to 10 times. Neustar’s figures confirm Arbor Networks’ report – released last week – which saw a record 325 Gbps attack hit a French organisation earlier this year, with a massive spike logged by the research division of the DDoS remediation firm on the first quarter of this year. Arbor says that it 72 attacks larger than 100 Gbps in size and volume, as well as 50 percent more attacks in the first quarter of 2014 than the entirety of 2013. Back at Neustar, the research company claims that 32 percent companies hit by a DDoS attack last year estimated the events had cost them more than £240,000 per day during the outage. Additionally, the reports notes larger DDoS attacks are becoming more frequent with a 200 percent increase in attacks affecting bandwidth of between 1 and 20 Gbps. For its research, Neustar took in response from 331 companies in the UK, across a range of public and private sector organisations. The company says its results show that DDoS attacks disrupt multiple business units – with public-facing areas like call centres, customer service and marketing operations absorbing more than 40 per cent of DDoS-attack related costs. This high cost may because these business functions are key revenue earners in most commercial companies, SCMagazineUK.com notes, but the report also cautions that DDoS attacks are now being used as smokescreens for other attacks – an attack vector that security researcher Brian Krebs has reported on several times over the last 12 months. Rodney Joffe, Neustar’s senior VP and technology fellow, said that organisations must remain constantly vigilant and abreast of the latest threats. “As an example, Neustar’s UltraDNS network suffered an attack just last week peaking at over 250 Gbps – a massive attack by industry standards. Even with proper mitigations in place, the attack caused an upstream ripple. It is a constantly changing threat landscape,”he noted. According to Mark Teolis, general manager with DOSarrest, a DDoS remediation specialist, the key problem with the latest generation of attacks is not just the volume and bandwidth used, but their general sophistication, with Layer 7 attacks now being seen in the mainstream. Layer 7 is the highest of the seven IP layers defined under the OSI (Open System Interconnection) model and represents the application layer – the location on the computing resource where data both originates and returns. Speaking with SCMagazineUK.com last week at the Infosecurity Europe show, Teolis said his firm’s latest software has been enhanced to deal with these latest Layer 7 attacks, by combining IDS (intrusion detection systems), load balancing, WAF (web application firewall) and DDoS mitigation under a single IT umbrella. Using an IDS, he explained, allows security professionals to pinpoint sophisticated layer 7 attacks, as well as provide cloud based WAF services. “Using these approaches – coupled with spreading the load across multiple cloud resources – significantly mitigates the effects of even the highest volume DDoS attack,” he said. Keith Bird, UK managing director with Check Point, told SCMagazineUK.com that DDoS attacks have been used as a hacktivist weapon for several years – and, as this research illustrates, now the net is widening to businesses at large. “We are seeing smokescreen-type attacks, and also more complex, multi-vector attacks on Web sites that combine DDoS with account tampering and fraud attempts,” he said adding, that, whilst these are difficult to defend against, firms should consider contingency and remediation plans in the event of such attacks. Source: http://www.scmagazineuk.com/ddos-attacks-half-of-targeted-firms-get-hit-again/article/345878/
See original article:
DDoS attacks: half of targeted firms get hit again


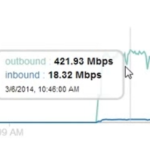 A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/
A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/