Days after Feedly and Evernote were briefly forced offline by hackers demanding a ransom payment, a code-hosting service was run out of business by a similar scheme. CodeSpaces.com closed its doors this week, following a security breach that began with a distributed denial-of-service (DDoS) attack, and ended 12 hours later after an attempt to extort money from the company. No stranger to DDoS attacks, Code Spaces thought it could handle the situation, but the situation quickly spiraled out of control. On Tuesday, an unauthorized person—not believed to be employed by the site—gained access to Code Spaces’s Amazon EC2 control panel. When the team fought back, the hacker deleted “most of our data, backups, machine configurations and offsite backups,” the company said. “Code Spaces will not be able to operate beyond this point,” an online notice said, citing the price of resolving the issue, as well as the expected cost of refunding paying customers. This week’s attack “will put Code Spaces in [an] irreversible position both financially and in terms of ongoing credibility.” “All that we have to say at this point is how sorry we are to both customers and to the people who make a living at Code Spaces for the chain of events that lead us here,” the company said. Users can expect more details once Code Spaces sorts out its customers’ needs. Those who have stored data on the site can email support@codespaces.com with an account URL, and if you’re lucky, some remaining crumbs will be returned. For more, watch PCMag Live in the video below, which the Code Spaces dilemma. It’s been a banner month for DDoS attacks: Evernote suffered a blow last week, but was back on its feet within a few hours. Feedly wasn’t so lucky, however. The RSS service was hit twice in two days, though the company promised user data remained safe. Similarly, Ancestry.com just recovered today from a three-day bout of DDoS, in which the site was overloaded with traffic and crashed. No user information was compromised. Source: http://www.pcmag.com/article2/0,2817,2459765,00.asp
Read More:
DDoS Attack Puts Code Spaces Out of Business


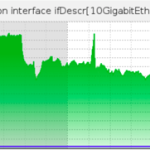 DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.
DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.