It’s not a matter of if you’re going to be DDoS attacked, it’s a matter of when – many APAC organisations fail to understand the threat and quantify the risk – right-sizing and verifying the solution is a must. When an attack occurs, the mature organisation is prepared to effectively mitigate the attack – protecting themselves (and in turn their clients and partners) from unacceptable financial and reputational impact. Let us look at these three steps, understand, quantify and mitigate, in detail. 1.Understand the threat The threat imposed by DDoS attacks in APAC is more significant than global counterparts. A recent Neustar survey showed that 77 percent of organisations within APAC have been attacked at least once, compared to 73 percent globally. Organisations within the region are also getting attacked more frequently, with 83 percent of those attacked being attacked more than once, and 45 percent having been attacked more than six times. In addition, attack sizes are steadily growing. In 2015, the average attack size identified by Neustar was about 5GB per second. By September 2016, average attack sizes had reached up to 7GB per second – and this was prior to the Mirai driven – IoT fuelled attacks – like those on Krebs, OVH and Dyn. Given this, we should expect a considerable rise in the mean size of volumetric attacks during 2017. We’ve also seen a steady increase in the number of multi-vector attacks – which now equates to about 50 percent of all DDoS attacks. In a multi-vector attack – the criminals are potentially aiming to distract an organisation with the DDoS attack while they go after their main target. They use the DDoS attack to draw away the organisations defensive capacity while they plant ransomware, breach the network or steal valuable data. Within APAC, compared to the global average of 25 percent, network breaches associated with a multi-vector attack is sitting at 33 percent, according to Neustar’s own data. This begs the question, are APAC organisations deficient when it comes to perimeter protection? When dealing with an attack, speed is critical. But surprisingly, within APAC, on average almost half of all organisations take over three hours to detect an attack and an additional three hours to respond. This is significantly higher than the global average of 29 percent and 28 percent respectively. Worryingly, slow detection and response can lead to huge damages financially. Around half of all organisations stand to lose an average of $100,000 per hour of peak downtime during an attack. To exacerbate this, half the attacked organisations were notified of the attack by a third party, inflicting additional potential reputational damage. 2.Quantify the risk If a person goes to insure their car, they’re not going to over or underinsure it. That is, they’re not going to pay a premium associated with a higher value car – if the car gets written-off, they’re only going to get the value of the car, not the extra value associated with the premium. Alternatively, if they are underinsured, they’re not going to get back the full value of the car – they will need to pay an additional amount to replace the car. When looking at a DDoS environment, it is a similar scenario. An organisation will want to make sure it understands the level of risk and apply the right mitigation and the right cost to protect that risk. Paying the cost for a DDoS mitigation that exceeds their requirements is like over insuring the car – you are paying a premium for a service that does not match your level of risk/potential loss. Similarly, implementing a DDoS mitigation that does not cover the risk will likely lead to additional costs, resulting from greater organisational impact and additional emergency response activities. Risk management is critical – rightsizing is a must – organisations need to prepare and implement a sound mitigation plan. To understand the severity of the risk DDoS imposes, organisations must quantify both probability and impact – tangible and intangible – and know the risk appetite and technical environment of the organisation. Once this information is gathered and the severity of the risk is understood, there are three key critical elements of producing a good mitigation plan that must be enacted: detection, response and rehearsal. 3.Mitigate the attack Detection; Timely detection is critical – slow detection greatly increases potential financial and reputational loss, and allows the attackers valuable time to initiate other attack vectors. Fortunately, there are several technologies out there that can be used to monitor both the physical and cloud-based environment. For example, organisations can use Netflow monitoring on border routers to detect a volumetric attack, or provide this data to a third-party for analysis and detection. Organisations can also look at using appliances to conduct automatic detection and response, again managed internally or by a third-party. In a cloud environment, there are plenty of cloud monitoring tools out there that allow companies to identify degradation and performance, CPU utilisation and latency, giving them an indication of when an attack occurs. Response; There are many DDoS mitigation solutions available, allowing organisations to match the solution to their requirements. In selecting a mitigation solution, it is important to review a complete range of options, and align the selected solution to the organisation’s risk exposure and technology infrastructure. For example an organisation operating in the cloud with a moderate risk exposure, might opt for a cloud based solution, pay-on-occurrence model. While a financial services company, operating its own infrastructure and exposed to substantial financial and reputational risk, would look for a hybrid solution, providing the best time to mitigate, low latency and near immediate failover to cloud mitigation for large volumetric attacks. Rehearsing; Once a DDoS mitigation service is selected and implemented, the detection and mitigation plan must be document and verified through testing. The frequency of testing a mitigation plan should be dependent on the level of risk. If in a high-risk environment, a business might want to rehearse monthly or quarterly. In a lower-risk environment, the organisation might stretch it out to yearly or biannually. By understanding the threat, quantifying the risk to the organisation and implementing a right-sized mitigation solution organisations can effectively and efficiently mitigate the risk of DDoS attacks. A well implemented and tested plan will protect an organisation from both financial and reputational damage, discouraging attackers, leading the wolf from your door, leaving them hunting for a softer target. Source: http://www.cso.com.au/article/617417/identifying-three-steps-ddos-mitigation/
Read the original post:
Identifying the three steps of DDoS mitigation


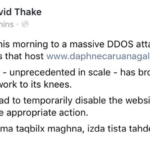 The servers hosting Daphne Caruana Galizia’s personal blog have suffered a DDoS attack. A DDos (denial of service) attack occurs when many systems flood the bandwidth of a targeted system, in an attempt to make the online service unavailable. Mrs Caruana Galizia does not yet know who is behind the attack, but did say it is highly likely to be a person of Maltese nationality.. Prior to the DDoS attack on the servers, she said, a fake Gmail account was setup – similar to her personal email address. The person who created the account, then emailed two persons working for the company who handle software support for the website, and tried to acquire information required to hack the site through them. This, however, did not work and the software support personnel realised that it was not Mrs Caruana Galizia’s email address, and also the use of broken English in the email. This, she said, is what led her to believe that the person behind the attack is Maltese. The police were contacted aftewr the DDOS attack occurred later, and an investigation is ongoing. The fake Gmail address used a proxy server, and thus far no culprit has been identified, she said. She explained that aside from the crime involving the DDoS attack, impersonation is also a crime. Vanilla Communications, a server hosting company owned by David Thake, hosts Daphne Caruana Galizia’s personal blog – a service that she pays for each month, she said. In a Facebook post, Mr Thake said that the servers hosting her website suffered a DDoS attack which he called “unprecedented in scale.” Mr Thake, in his post, said the attack brought the network to its knees. Source: http://www.independent.com.mt/articles/2017-03-21/local-news/Servers-hosting-Daphne-Caruana-Galizia-s-website-suffer-unprecedented-DDOS-attack-6736171884
The servers hosting Daphne Caruana Galizia’s personal blog have suffered a DDoS attack. A DDos (denial of service) attack occurs when many systems flood the bandwidth of a targeted system, in an attempt to make the online service unavailable. Mrs Caruana Galizia does not yet know who is behind the attack, but did say it is highly likely to be a person of Maltese nationality.. Prior to the DDoS attack on the servers, she said, a fake Gmail account was setup – similar to her personal email address. The person who created the account, then emailed two persons working for the company who handle software support for the website, and tried to acquire information required to hack the site through them. This, however, did not work and the software support personnel realised that it was not Mrs Caruana Galizia’s email address, and also the use of broken English in the email. This, she said, is what led her to believe that the person behind the attack is Maltese. The police were contacted aftewr the DDOS attack occurred later, and an investigation is ongoing. The fake Gmail address used a proxy server, and thus far no culprit has been identified, she said. She explained that aside from the crime involving the DDoS attack, impersonation is also a crime. Vanilla Communications, a server hosting company owned by David Thake, hosts Daphne Caruana Galizia’s personal blog – a service that she pays for each month, she said. In a Facebook post, Mr Thake said that the servers hosting her website suffered a DDoS attack which he called “unprecedented in scale.” Mr Thake, in his post, said the attack brought the network to its knees. Source: http://www.independent.com.mt/articles/2017-03-21/local-news/Servers-hosting-Daphne-Caruana-Galizia-s-website-suffer-unprecedented-DDOS-attack-6736171884