magnoliareporter.com experienced some technical issues on Friday. Our website is hosted by a service known as TownNews.com , which hosts and provides technical assistance to thousands of media-oriented websites across the country. TownNews.com was hit by a directed denial of service (DDoS) attack on Friday afternoon. This mainly manifested itself by making it difficult for us — and hundreds of other websites — to access our servers and make changes. People may have had difficulty accessing our website during that time. We do not think that our thousands of daily visitors have anything to worry about as TownNews.com technology responded immediately. That said, it is probably a good thing that we are not president of the United States. To us, hackers present a clear and present danger to the security of the United States, which has our permission to deal with them with extreme prejudice. North Korea is bent out of shape over the pending deployment by South Korea of the U.S.-made Terminal High Altitude Defense System, or THAAD. THAAD launchers and fire control systems are made in East Camden. North Korea’s military said in a statement that, “There will be physical response measures from us as soon as the location and time that the invasionary tool for U.S. world supremacy, THAAD, will be brought into South Korea are confirmed. It is the unwavering will of our army to deal a ruthless retaliatory strike and turn (the South) into a sea of fire and a pile of ashes the moment we have an order to carry it out.” Ohhhhhhh. We’re scared. Seriously, how many submarines, cruisers, aircraft carriers, bombers and drones are circling offshore North Korea, ready to unleash hell at any given moment? And that’s just the U.S. military. That sea of fire and pile of ashes looks a lot like future downtown Pyougyang to us. The Magnolia School District website is having a makeover. We’ll let you know when the site is up and running. Looking for more widely spread drought conditions when the new report comes out later this week. We’re expecting more abnormally dry conditions in South Arkansas. Patrick Posey died Saturday at his home near Benton, LA. Posey and his wife, Susan, performed much of the mural restoration work around the square a few years ago. Some fool vandalized highway signs in the Walkerville area on during the weekend, but the hate speech written on them was cleaned up. Our new online poll asks for your opinion about the state of race relations in Columbia County – whether they are better, worse or about the same as a decade ago. Another question might be what each of us, as individuals, is doing to make things better. Five years ago, we reported that Walkerville Cumberland Presbyterian Church was dedicating a new manse. A year ago, we reported that Betsy Production was drilling an oil well on the SAU campus. Vice President Aaron Burr shot and mortally wounded former Treasury Secretary Alexander Hamilton in a duel on this date in 1804. Author E.B. White was born on this date in 1899. George Gershwin died on this date in 1937. Source: http://www.magnoliareporter.com/news_and_business/mike_mcneills_diary/article_733b45f8-4720-11e6-9e2d-97f7f136ad46.html
Taken from:
Mike McNeill’s Diary for Monday, July 11, 2016: Fighting off the DDoS

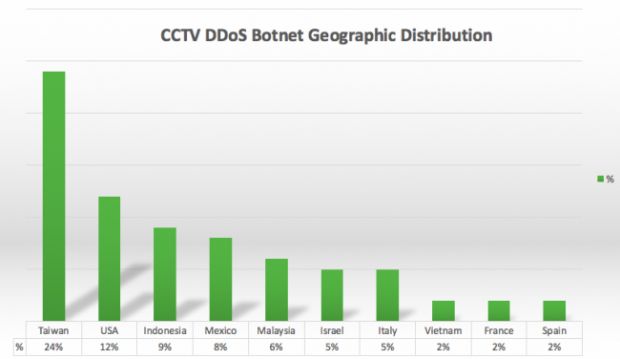
 All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A
All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A