Just because your business doesn’t have a website, that doesn’t mean it can’t be a victim of a DDoS (distributed denial of service) attack. This sentence might not make much sense at this point, but keep reading. Security firm Kaspersky Lab and researchers B2B International looked at what cyber-crooks go for when attacking businesses and enterprises, and here’s what they came up with: Last year, 16 per cent of companies (globally), were victims of a DDoS attack. Among enterprises, the percentage jumps up to 24. For most, external activities, such as websites, were targeted. Among half, websites had been hit, logins and portals were attacked in 38 per cent of cases, while communications services were attacked 37 per cent of times. Transactional systems had been affected in 25 per cent of cases. But also, in 25 per cent of cases, file servers had been hit, and 15 per cent said their operational systems were targeted. Another 15 per cent said a DDoS attack hit their ISP network connectivity. “It’s important to take a DDoS attack seriously. It’s a relatively easy crime to perpetrate, but the effect on business continuity can be far-reaching. Our study found that alongside the well-publicised impact of an attack, such as website downtime, reputational damage and unhappy customers, DDoS hits can reach deep into a company’s internal systems. It doesn’t matter how small the company is, or whether or not it has a website; if you’re online, you’re a potential target. Unprotected operational systems are just as vulnerable to a DDoS attack as the external website, and any disruption can stop a business in its tracks,” said Evgeny Vigovsky, Head of Kaspersky DDoS Protection, Kaspersky Lab. Source: http://www.itproportal.com/2016/02/29/you-dont-need-a-website-to-get-hit-by-ddos/
See the original article here:
You don’t need a website to get hit by DDoS


 Every day hackers attack Norway´s largest news site, VG. But not without risk. VG has both helped the police put hackers behind bars and alerted mothers about what their adventurous sons are up to. VG.no is one of the most successful news sites in the world. Every week 4 million Norwegians – out of a population of 5 million – visit the site for the latest news. But that also makes VG.no a target for hackers. “Whenever there is a new security hole discovered, someone want to try it on VG,” says Audun Ytterdal, head of IT operations in VG. During the Schibsted Tech Polska Winter Event 2016 he presented “War stories from the ops trenches”, describing how the media house protects itself from a continuous flow of DDoS attacks. Under attack every day VG is well prepared for hacker attacks – and is able to deal with lots of traffic without going down. According to Ytterdal the site can handle up to 30 GB per second. “Usually we see around 10.000 http-hits per second. But during the attacks we can experience up to 100.000 http-hits per second,” he explains. Called the hacker´s mum In the presentation he explains some of the technical measures taken to secure the news site from attack. But he also tells entertaining stories about how the IT staff used their technical skills to identify the hackers. And not always the hackers have everything planned out! Take for instance the young hacker who managed to take over the front page of the business site E24.no with photos of himself in a balaclava taken in his mum´s bathroom. However smart he had been breaking into the site, he had forgotten to remove the location info added to the image file when he took the photo with his mobile phone. “So we could see where he lived – and we called his mum informing her that her son was up to activities she may not approve of,” laughs Audun Ytterdal. Sent hackers to jail In another case the hackers bragged about their achievement on Twitter. That gave the IT operations department the opportunity to contact them directly. After a while they also managed to identify two of the hackers. When one of them posted a photo from a town in Southern Norway, VG was able to locate the exact house it had been taken from with use of Google Street View. The information was given to the police – and the two hackers later had to serve time in jail. Entertaining error page For a news room all alarms go off when the main site is down. And Audun Ytterdal believes it will be very hard to avoid never being shut down. So what to do when it happens? Of course identify and fix the problem. But VG also decided to give people a good laugh by designing an entertaining error page. The error page is a fun version of the normal front page of the site. “The last time we used this we had people tweeting that they would rather see the error page of VG than any other news site,” smiles Ytterdal. Source: http://www.schibsted.pl/2016/02/how-norways-biggest-news-site-protects-itself-from-ddos-attacks/
Every day hackers attack Norway´s largest news site, VG. But not without risk. VG has both helped the police put hackers behind bars and alerted mothers about what their adventurous sons are up to. VG.no is one of the most successful news sites in the world. Every week 4 million Norwegians – out of a population of 5 million – visit the site for the latest news. But that also makes VG.no a target for hackers. “Whenever there is a new security hole discovered, someone want to try it on VG,” says Audun Ytterdal, head of IT operations in VG. During the Schibsted Tech Polska Winter Event 2016 he presented “War stories from the ops trenches”, describing how the media house protects itself from a continuous flow of DDoS attacks. Under attack every day VG is well prepared for hacker attacks – and is able to deal with lots of traffic without going down. According to Ytterdal the site can handle up to 30 GB per second. “Usually we see around 10.000 http-hits per second. But during the attacks we can experience up to 100.000 http-hits per second,” he explains. Called the hacker´s mum In the presentation he explains some of the technical measures taken to secure the news site from attack. But he also tells entertaining stories about how the IT staff used their technical skills to identify the hackers. And not always the hackers have everything planned out! Take for instance the young hacker who managed to take over the front page of the business site E24.no with photos of himself in a balaclava taken in his mum´s bathroom. However smart he had been breaking into the site, he had forgotten to remove the location info added to the image file when he took the photo with his mobile phone. “So we could see where he lived – and we called his mum informing her that her son was up to activities she may not approve of,” laughs Audun Ytterdal. Sent hackers to jail In another case the hackers bragged about their achievement on Twitter. That gave the IT operations department the opportunity to contact them directly. After a while they also managed to identify two of the hackers. When one of them posted a photo from a town in Southern Norway, VG was able to locate the exact house it had been taken from with use of Google Street View. The information was given to the police – and the two hackers later had to serve time in jail. Entertaining error page For a news room all alarms go off when the main site is down. And Audun Ytterdal believes it will be very hard to avoid never being shut down. So what to do when it happens? Of course identify and fix the problem. But VG also decided to give people a good laugh by designing an entertaining error page. The error page is a fun version of the normal front page of the site. “The last time we used this we had people tweeting that they would rather see the error page of VG than any other news site,” smiles Ytterdal. Source: http://www.schibsted.pl/2016/02/how-norways-biggest-news-site-protects-itself-from-ddos-attacks/ 
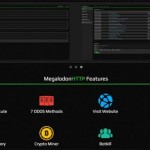 Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml
Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml