Faced with a wave of DDoS attacks, a horde of hackers claiming to be Anonymous and major data leaks from state-owned CAT Telecom all in protest of Thailand’s Single Gateway surveillance program, ICT Minister Uttama Savanayana took to Twitter to reassure people that everything was in order and that we had nothing to fear because we have regular data backups. Yes, apparently regular backups and standards in data storage are the answer to a hack and data leak. The tweet was up for most of the weekend before he deleted it to save himself further embarrassment. To recap, a group claiming to be Anonymous issued a statement in the wee hours of Thursday morning to attack the Thai Government and in particular CAT Telecom for refusing to back down on Single Gateway internet super censorship and surveillance project which, despite promises from the Prime Minister that it was just a clerical error never existed, is forging ahead full steam. Since then at various moments, hackers have managed to temporarily take down an obscure army internal accounting website, the ICT Ministry and CAT Telecom. The Anons also posted screenshots of what they claimed was CAT customer data with names blanked out, taunting the ICT Minister by asking what data standard allows for plaintext storage of passwords. CAT Telecom initially responded by saying the information posted was false and that the hackers only tried to infiltrate CAT’s dealer network and did so unsuccessfully at that. The Anons responded with more CAT customer data and a screenshot of a login in CAT’s CRM module. One would have thought that this would have caused the junta to think twice about centralizing everything but no. The ICT Minister had the stage in the weekly two-minutes of hate propaganda show, sorry, I meant Thailand Moves Forward propaganda show, in which he extolled the virtues of a single Geoment Service Chanel [sic] which called for even more centralization. Half the jokes were of using designer clothing to serve the people the other, well, let’s just say that geo in Thai is a anatomical word that would not befit the pages of this publication. So apparently not only he totally clueless as to what a modern day hack is (by saying that he had backup) but he cannot use a spell checker. By Sunday, CAT’s My 3G self-service portal was still down, though whether it was from the attack or if someone pulled the plug as a precaution was anyone’s guess. However, that hardly made the social media circles. Why? Well, because despite oodles of taxpayer cash (roughly $1 billion each for CAT and TOT for their 3G networks, plus who knows how much more to run the network), CAT and TOT have between them less than 100,000 subscribers, none of which bothered to check their balance or top up over the weekend, it seemed. Also noteworthy was how servers in CAT’s data center had their latency and jitter both jump but again, that could be a routing issue rather than someone installing deep-packet-inspection gear. But was the hack actually from a real Anon? Anonymous is more of a state of mind that a club with a for formal job interview and membership cards. Anyone can claim to be an Anon. Their key tenets are anti-surveillance and anti-censorship, both of which the Thai Single Gateway are aimed at imposing. One developer who did not want to be identified told TelecomAsia that the hacks on Thai government websites were simply too easy. He sent a screenshot with a page of .go.th sites with old, unpatched mysql servers that were ripe for taking over. His point being, a script kiddie noob could have carried out hacks on these government websites and it did not require the skills of a true Anon. Source: http://www.telecomasia.net/blog/content/thai-govt-website-ddosed-cat-customer-data-leaked DDoS? Well, considering that Thai government websites cannot even stand up to use on a busy day without crashing, again, that hardly requires serious firepower. The CAT data breach also happened about a month ago if the rumors in the underground are to be believed. Talking about the underground, none of my shadier contacts know who did it the attack. Considering the rather small size of the Thai hacking community, this is odd. To further throw doubt on everything, the F5 hackers dared me over Twitter to double check a phone number in the CAT data breach to see if the data was real or made up. I did call up the number and he had no clue about being hacked and said he was not a CAT customer. Not looking good for the hackers then. To be fair I did try to ask if he was working at the company he was listed as working for but the chap hung up on me first, obviously annoyed at my questions. But perhaps the number had been reused (the phone line application with CAT was way back in August 2014), perhaps he never got the phone line and had totally forgot about it. Or maybe it was made-up data and the hacker thought I would not call to fact-check. At this juncture, my gut feeling is leaning towards this entire episode being a honey trap to lure out dissenters and convince the undecided of the need to give up further liberties so that the government can protect us from Anonymous. If so, that has worked wonders. Then there is the separate matter of the 231 pages of leaked documents that are a headache just to try and read through. Who leaked them and why? It is a curious mix of army and MICT secret documents which begs the question, who would even have access to both sets of documents in the first place? Very few. But regardless as to whether this initial hack was real or staged, the matter of the Thailand’s Single Gateway has now reached the eyes of Anons the world over. One wonders if they are planning a real attack soon.
View article:
Thai govt website DDoSed as CAT customer data leaked


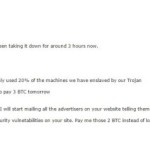 Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml
Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml