South Africa is the most targeted country in Africa when it comes to distributed denial-of-service (DDOS) attacks. This was revealed by Vernon Fryer, chief technology security officer at Vodacom, in a keynote address during ITWeb Security Summit 2015, in Midrand, this morning. In computing, a DDOS attack is an attempt to make a machine or network resource unavailable to its intended users. Such an attack generally consists of efforts to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet. Fryer was speaking with reference to statistics from the Vodacom Cyber Intelligence Centre, which the company established eight years ago to analyse the threat landscape on the African continent. He revealed over the past 18 months, there has been a marked increase in DDOS attacks on the continent, with a typical attack averaging 9Gbps. “There has been about a 150% increase in the number of DDOS [attacks] in the last 18 months in Africa,” he said. In terms of the number of attacks, Kenya, Uganda, Algeria, Nigeria and Tanzania respectively come after SA, said Fryer, pointing to the analysis done by the Vodacom Cyber Intelligence Centre last Thursday. According to Fryer, the majority of in-bound traffic to SA emanated mainly from China, Germany, Brazil, Vietnam, Russia, Cyprus, Turkey, Switzerland, Canada and the US. However, he noted, it was surprising Switzerland and Canada were featuring on the list this year, something never witnessed previously. Another unexpected trend showed traffic coming from Swaziland, he added, pointing out the growing number of Chinese communities in the country could be a reason for this spike. Describing some of the attack vectors cyber criminals were making use of in the region, Fryer pointed to scareware, ransomware, fake anti-virus, as well as TDSS Rootkit, among others. The trending malware included KINS Trojan, Skypot, VirRansom, SpyEye Trojan and the Chameleon Botnet. With regard to ransomware attacks in Africa, Tanzania is the most attacked on the African continent, Fryer said. He also noted the trending hacker groups in Africa include Anonymous, also known as the Lizard Squad, the Syrian Electronic Army, as well as the Yemen Cyber Army. Faced with the rise in the level and sophistication of attacks, Fryer said organisations need to constantly monitor the behaviour of their firewalls. Typically, he said, organisations take about five years without monitoring their firewall. “We need to understand if our firewalls are capable of handling today’s threats. Thus, the performance of firewalls needs to be constantly monitored,” he concluded. Source: http://www.itweb.co.za/index.php?option=com_content&view=article&id=143446:SA-a-target-for-DDOS&catid=234
Taken from:
South Africa a target for DDoS


 In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/
In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/ 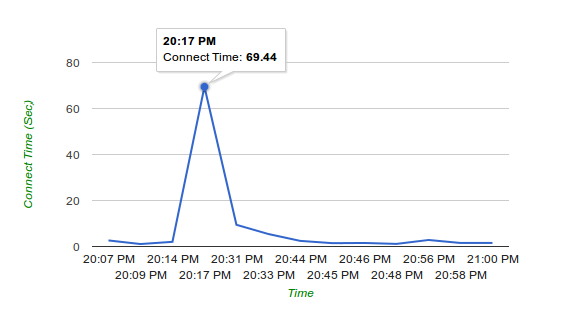
 The admin of Therealdeal market ( http://trdealmgn4uvm42g.onion/ ) provided us with some insights about the recent DDo’s attacks that are hitting all the major DNM’s in the past week: In the past few days, it seems like almost every DN market is being hit by DDoS attacks. Our logs show huge amounts of basic http requests aiming for dynamic pages, probably in attempt to (ab)use as many resources as possible on the server side, for example by requesting for pages that execute many sql queries or generate captcha codes. As we are security oriented we manged to halt the attack on our servers the moment it showed up in the logs. Although this required fast thinking, due to the fact that dealing with this kind of attack over tor is not the same as dealing with such attack over clearnet. New addresses? Shifting Pages? Waiting? All these did not work for other markets… Here you can see the beginning and failure, as caught by Dnstats: As you can see, our market’s response time spiked to almost 70 seconds while our market’s usual response time is insanely fast, almost like most clearnet sites. But also, you can see that the response time was back to 2-3 seconds a little after. Here is an example of a darknet market that didn’t know how to combat this problem: The flat line at 0 seconds meaning there was no response from the server. The Problem As opposed to cleanet attacks, where mitigation steps could be taken by simply blocking the offending IP addresses,when it comes to tor, the requests are coming from the localhost (127.0.0.1) IP address as everything is tunneled through tor. Another problem is the fact that the attackers are using the same user-agent of tor browser – hence we cannot drop packets based on UA strings. The attackers are also aiming for critical pages of our site – for example the captcha generation page. Removing this page will not allow our users to login, or will open the site to bruteforce attempts. Renaming this page just made them aim for the new url (almost instantly, seems very much automated). One of the temporary solutions was to run a script that constantly renamed and re-wrote the login page after 1 successful request for a captcha… Attacks then turned into POST requests aiming for the login page. Solutions If you are a DNM owner or just the security admin, check your webserver logs. There is something unique in the HTTP requests, maybe a string asking you to pay to a specific address. (assuming these are the same offenders). Otherwise there might be something else … Hint: you might need to load tcpdump during an attack. Hopefully, you are not using some kind of VPS and have your own dedicated servers and proxy servers. Or if you are using some shit VPS, then hopefully you are using KVM or XEN. (first reason being the memory is leakable and accessible by any other user of the same service). The other reason is – control on the kernel level. You can drop packets containing specific strings by using iptables, or use regex too. This is one example of a commad that we executed (amongst others) to get rid of the offenders, we cannot specify all of them, so be creative! iptables -A INPUT -p tcp –dport 80 -m string –algo bm –string “(RANSOM_BITCOIN_ADDRESS)” -j DROP Where (RANSOM_BITCOIN_ADDRESS) is the unique part of the request… To Other Market Admins: There are additional things to be done, but if we expose them, this will only start a cat and mouse game with these attackers. If you are a DNM admin feel free to sign up as a buyer at TheRealDeal Market and send us a message (including your commonly used PGP), since at the end of the day even though you might see us a competitor in a way, there are some things (like people stuck without their pain medication from mexico) that are priceless… Source: http://www.deepdotweb.com/2015/05/11/this-is-the-ransom-ddos-that-is-hitting-the-dark-net-markets/
The admin of Therealdeal market ( http://trdealmgn4uvm42g.onion/ ) provided us with some insights about the recent DDo’s attacks that are hitting all the major DNM’s in the past week: In the past few days, it seems like almost every DN market is being hit by DDoS attacks. Our logs show huge amounts of basic http requests aiming for dynamic pages, probably in attempt to (ab)use as many resources as possible on the server side, for example by requesting for pages that execute many sql queries or generate captcha codes. As we are security oriented we manged to halt the attack on our servers the moment it showed up in the logs. Although this required fast thinking, due to the fact that dealing with this kind of attack over tor is not the same as dealing with such attack over clearnet. New addresses? Shifting Pages? Waiting? All these did not work for other markets… Here you can see the beginning and failure, as caught by Dnstats: As you can see, our market’s response time spiked to almost 70 seconds while our market’s usual response time is insanely fast, almost like most clearnet sites. But also, you can see that the response time was back to 2-3 seconds a little after. Here is an example of a darknet market that didn’t know how to combat this problem: The flat line at 0 seconds meaning there was no response from the server. The Problem As opposed to cleanet attacks, where mitigation steps could be taken by simply blocking the offending IP addresses,when it comes to tor, the requests are coming from the localhost (127.0.0.1) IP address as everything is tunneled through tor. Another problem is the fact that the attackers are using the same user-agent of tor browser – hence we cannot drop packets based on UA strings. The attackers are also aiming for critical pages of our site – for example the captcha generation page. Removing this page will not allow our users to login, or will open the site to bruteforce attempts. Renaming this page just made them aim for the new url (almost instantly, seems very much automated). One of the temporary solutions was to run a script that constantly renamed and re-wrote the login page after 1 successful request for a captcha… Attacks then turned into POST requests aiming for the login page. Solutions If you are a DNM owner or just the security admin, check your webserver logs. There is something unique in the HTTP requests, maybe a string asking you to pay to a specific address. (assuming these are the same offenders). Otherwise there might be something else … Hint: you might need to load tcpdump during an attack. Hopefully, you are not using some kind of VPS and have your own dedicated servers and proxy servers. Or if you are using some shit VPS, then hopefully you are using KVM or XEN. (first reason being the memory is leakable and accessible by any other user of the same service). The other reason is – control on the kernel level. You can drop packets containing specific strings by using iptables, or use regex too. This is one example of a commad that we executed (amongst others) to get rid of the offenders, we cannot specify all of them, so be creative! iptables -A INPUT -p tcp –dport 80 -m string –algo bm –string “(RANSOM_BITCOIN_ADDRESS)” -j DROP Where (RANSOM_BITCOIN_ADDRESS) is the unique part of the request… To Other Market Admins: There are additional things to be done, but if we expose them, this will only start a cat and mouse game with these attackers. If you are a DNM admin feel free to sign up as a buyer at TheRealDeal Market and send us a message (including your commonly used PGP), since at the end of the day even though you might see us a competitor in a way, there are some things (like people stuck without their pain medication from mexico) that are priceless… Source: http://www.deepdotweb.com/2015/05/11/this-is-the-ransom-ddos-that-is-hitting-the-dark-net-markets/