Reports this week claimed Sony Pictures were carrying out denial of service attacks against certain websites which were sharing files stolen in the devastating cyber-attack against the studio. The sources speaking to Recode said that Sony Pictures was using Amazon Web Services’ (AWS) cloud computing infrastructure in Tokyo and Singapore to flood websites which are sharing the files illegally, but this claim has now been denied by the company involved. A spokesperson for AWS has however categorically denied that this is the situation, telling IBTimes UK : AWS employs a number of automated detection and mitigation techniques to prevent the misuse of our services. In cases where the misuse is not detected and stopped by the automated measures, we take manual action as soon as we become aware of any misuse. Our terms are clear about this. The activity being reported is not currently happening on AWS. It is unclear if Sony Pictures is carrying out the attacks suggested by the sources speaking to Recode, and simply using another computing infrastructure, or if the studio is not actually carrying out these attacks at all. Martin McKeay, who works with cloud services provider Akamai, told ITSecurity Guru that there could be some truth in the speculation: “It has the potential for being true and not utterly impossible to be some truth to this, and I don’t think it is utterly impossible that they are doing it through some third party who is doing this via AWS,” he said. “There are some systems out there for doing load testing and some of them can be done through AWS and can generate traffic like that, but what is more likely is that they are feeding the torrent sites with false information and causing a DDoS in that way.” Tim Erlin from Tripwire told IBTimes UK that if there is truth to the rumour, it could spell even more trouble for Sony Pictures: “Taking the step to ‘hack back’ against perceived legitimate targets, based on their own assessment of guilt, presents a myriad of potential legal problems. If Sony manages to disrupt, intentionally or accidentally, a legitimate service in the process, they may be adding to their problems, rather than improving the situation.” Sony Pictures has not commented on these reports, but the company is still trying to get its systems back fully under its control since the studio was attacked by a group of mysterious hackers called Guardians of Peace almost three weeks ago. “ The movie of terrorism” The group, which claims to have stolen “tens of terabytes” of information from Sony Pictures, released the latest tranche of stolen documents on Wednesday. Along with releasing copies of Sony Pictures’ films, the leak includes personal and financial information of thousands of the company’s employees, internal emails from executive discussing high profile stars like Angelina Jolie and films like Jobs, the Steve Jobs biopic. The leaked data has also included highly sensitive information on actors’ salaries and the amount of money that it is being paid by Netflix for its films. Source: http://www.ibtimes.co.uk/sony-pictures-not-using-amazon-web-services-ddos-illegal-file-sharing-websites-1479230
Read More:
Sony Pictures not using Amazon Web Services to DDoS illegal file-sharing websites

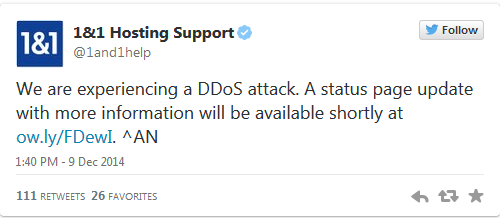
 UK hosting company 1&1 went titsup late on Tuesday night and struggled to recover this morning, after claiming it had been the victim of a Distributed-Denial-of-Service (DDoS) attack. The website collapsed shortly before 10pm yesterday, and it has taken 1&1 a full 12 hours to get its service back up and running. Readers who told the Reg about the outage said that the service had been flaky for several hours before it keeled over. 1&1 blamed the downtime on a DDoS attack in a tweet. However, although the website appeared to be returning to normal, 1&1 had yet to update its customers about the status of its system at time of writing. Customers were still griping about the mysterious outage this morning. Indeed, 1&1 was tight-lipped about the cause of the service disruption on its status page, which made no mention of a system security breach. Last month, Fasthosts blamed a five-hour outage it had suffered on a DDoS attack. Source: http://www.theregister.co.uk/2014/12/10/1_and_1_hosting_firm_claims_ddos_attack_downs_website/
UK hosting company 1&1 went titsup late on Tuesday night and struggled to recover this morning, after claiming it had been the victim of a Distributed-Denial-of-Service (DDoS) attack. The website collapsed shortly before 10pm yesterday, and it has taken 1&1 a full 12 hours to get its service back up and running. Readers who told the Reg about the outage said that the service had been flaky for several hours before it keeled over. 1&1 blamed the downtime on a DDoS attack in a tweet. However, although the website appeared to be returning to normal, 1&1 had yet to update its customers about the status of its system at time of writing. Customers were still griping about the mysterious outage this morning. Indeed, 1&1 was tight-lipped about the cause of the service disruption on its status page, which made no mention of a system security breach. Last month, Fasthosts blamed a five-hour outage it had suffered on a DDoS attack. Source: http://www.theregister.co.uk/2014/12/10/1_and_1_hosting_firm_claims_ddos_attack_downs_website/