The advisory alerts enterprises to a DDoS botnet-building operation by attackers taking advantage of the Shellshock Bash bug in Linux-based, Mac OS X and Cygwin systems. Failure to take action can result in a vulnerable system being used to propagate a DDoS botnet, launch DDoS attacks, exfiltrate confidential data and run programs on behalf of attackers. “PLXsert has observed the DDoS botnet-building operation of an attacker using Shellshock to gain access to and control Linux-based systems.” said Stuart Scholly, senior vice president and general manager, Security Business Unit, Akamai. “We are sharing this information to help enterprises patch their systems to prevent unauthorised access and use by this botnet. Akamai customers have multiple options to minimise the risk of a breach and to mitigate DDoS attacks enabled by this vulnerability.” Attackers breach vulnerable systems Malicious actors are using the Bash bug vulnerability, which is reportedly present in GNU Bash versions 1.03 through 4.3, to download and execute payloads on victim machines. These payloads include executable files and script files written in programming languages such as Perl, Python or PHP. The dropped files are capable of launching DDoS attacks, stealing sensitive information and moving laterally across internal networks to breach other systems. In addition, malicious attackers have implemented backdoor functionality to gain unrestricted access to victim machines in the future. DDoS botnet uses Internet Relay Chat IRC for communication PLXsert recorded an actual IRC conversation of a botnet-building operation that uses the Shellshock vulnerability to add new bots to a botnet. The observed botnet involved 695 bots. IRC channels #p and #x were used to issue commands, and new bots were requested to join channel #new. Web applications at high risk Web applications that use the Common Gateway Interface (CGI) method to serve dynamic content are at risk for the Bash bug. It is important to check internal and external web servers for this type of application and others that may potentially pass input to Bash. The Shellshock vulnerability has also been exploited in OpenSSH (OpenBSD Secure Shell), a set of computer programs that provides encrypted communication sessions. In this case the vulnerability is exploited after authentication, which lowers the risk of exploitation but should still be considered high risk. Enterprises need to patch (and re-patch) vulnerable hosts Enterprises must update and patch vulnerable hosts as soon as possible. Some of the earlier patches were insufficient. It is important to obtain and apply the latest patch from the operating system developer. Fully patched, remote exploitation attempts of this type will be unsuccessful. PLXsert anticipates further infestation and the expansion of this DDoS botnet. Get the Shellshock DDoS Botnet Threat Advisory to learn more In the Bash bug advisory, PLXsert shares its analysis and details, including: Vulnerable Bash versions DDoS building capabilities of binary payloads Types of DDoS attacks IRC conversation from within the DDoS botnet How to mitigate this vulnerability DDoS mitigation Source: http://www.australiansecuritymagazine.com.au/2014/11/akamai-observes-shellshock-used-build-ddos-botnet/
Read More:
Shellshock Being Used to Build a DDoS Botnet to launch DDoS attacks


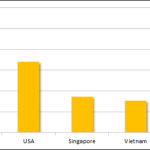 Majority of DDoS traffic in 2014 originated from India, says a new research from Symantec. Of the top 50 countries that witnessed the highest volume of originating DDoS traffic, India accounted for 26 percent of all DDoS traffic, followed by the USA with 17 percent, the research said. The results prove India has a high number of bot infected machines and a low adoption rate of filtering of spoofed packets, but may not imply that people behind the attacks are located in India because DDoS attacks are often orchestrated remotely. However, the study indicates that India is emerging as a hotbed to launch these attacks, potentially because of the low cyber security awareness, lack of adequate security practices and infrastructure, said Tarun Kaura, director, Technology Sales at Symantec India. The year 2014 saw an increase in the compromise of Linux servers, including those from cloud providers. These high bandwidth servers are then used as part of a botnet to perform DDoS attacks. The so-called “Booter” services can be hired for as little as INR 300 ($5 USD) to perform DDoS attacks for a few minutes against any target. Longer attacks can be bought for larger prices. They also offer monthly subscription services, often used by gamers to take down competitors. As the most attacked sector globally, the gaming industry experiences nearly 46 percent of attacks, followed by the software and media sectors While it’s not happening on a broad scale now, it’s likely we’ll see an increase in DDoS attacks originating from mobile and IoT devices in the future, Symantec said. DDoS attacks make an online service unavailable by overwhelming it with traffic from multiple sources. A Domain Name Server (DNS) amplification attack is a popular form of DDoS, which floods a publically available target system with DNS response traffic. Symantec’s research indicates that DNS amplification attacks have increased by 183 percent from January to August 2014. Motivations behind DDoS Attacks include hacking and financial blackmail with the threat of taking the business offline personal grudge. It also acts as a diversion technique to distract IT security response teams while a targeted attack is conducted. Source: http://www.infotechlead.com/2014/10/24/india-accounts-26-top-ddos-traffic-symantec-26196
Majority of DDoS traffic in 2014 originated from India, says a new research from Symantec. Of the top 50 countries that witnessed the highest volume of originating DDoS traffic, India accounted for 26 percent of all DDoS traffic, followed by the USA with 17 percent, the research said. The results prove India has a high number of bot infected machines and a low adoption rate of filtering of spoofed packets, but may not imply that people behind the attacks are located in India because DDoS attacks are often orchestrated remotely. However, the study indicates that India is emerging as a hotbed to launch these attacks, potentially because of the low cyber security awareness, lack of adequate security practices and infrastructure, said Tarun Kaura, director, Technology Sales at Symantec India. The year 2014 saw an increase in the compromise of Linux servers, including those from cloud providers. These high bandwidth servers are then used as part of a botnet to perform DDoS attacks. The so-called “Booter” services can be hired for as little as INR 300 ($5 USD) to perform DDoS attacks for a few minutes against any target. Longer attacks can be bought for larger prices. They also offer monthly subscription services, often used by gamers to take down competitors. As the most attacked sector globally, the gaming industry experiences nearly 46 percent of attacks, followed by the software and media sectors While it’s not happening on a broad scale now, it’s likely we’ll see an increase in DDoS attacks originating from mobile and IoT devices in the future, Symantec said. DDoS attacks make an online service unavailable by overwhelming it with traffic from multiple sources. A Domain Name Server (DNS) amplification attack is a popular form of DDoS, which floods a publically available target system with DNS response traffic. Symantec’s research indicates that DNS amplification attacks have increased by 183 percent from January to August 2014. Motivations behind DDoS Attacks include hacking and financial blackmail with the threat of taking the business offline personal grudge. It also acts as a diversion technique to distract IT security response teams while a targeted attack is conducted. Source: http://www.infotechlead.com/2014/10/24/india-accounts-26-top-ddos-traffic-symantec-26196