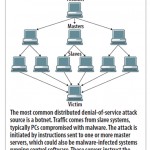
 Late last month, two members of the hacker group LulzSec pleaded guilty to launching distributed denial-of-service (DDoS) attacks against entities ranging from the state of Arizona to Nintendo to the CIA. Yet despite extensive media coverage of such attacks, chief information security officers are still surprised when their companies get hit. This is not an unforeseeable lightning bolt from the blue, people. The cyber world is full of anonymous arsonists, and too many businesses are operating without a fire department on call. A few sprinklers won’t cut it when things flare out of control. Firewalls and intrusion-prevention system appliances are no substitute for specialized DDoS backup when an attack escalates. Proactively securing a mitigation service can be a good insurance policy–in fact, it’s better than insurance, which pays off only after damage is done. That’s because mitigation services are designed to prevent destruction from occurring in the first place. Not only can a mitigation service act as a deterrent–many attackers will move on to easier prey when they see an initial DDoS attack fail–but these providers have the capacity and expertise to rapidly scale DDoS countermeasures against coordinated, professional attacks. That can mean keeping your website online even under heavy bombardment. Big And Small Companies At Risk Denial-of-service attacks used to be something that happened to other people, those with high online visibility. Not anymore. “We’ve seen very small companies come to us and they can’t figure out why they’re under attack,” says Chris Richter, VP of security products and services at Savvis. They ask, “‘What have we done?’” Blame the proliferation of prepackaged DDoS toolkits, such as the Low Orbit Ion Cannon and Dirt Jumper, for the fact that no one’s safe. Like any brute-force tactic, DDoS relies on the fact that any attack, even the most rudimentary, repeated with sufficient volume and frequency, can effectively shut down a network or website. Botnets often span thousands or millions of systems worldwide; Akamai, for example, provides a real-time attack heat map. In early July, attack rates were almost 30% above normal, with hot spots in Delaware and Italy. Geographic dispersion, coupled with network traffic crafted to look like legitimate connections from normal users, makes DDoS attacks both extremely effective and difficult to defeat if you’re not an expert with the right tools. There are three main distributed denial-of-service categories: > > Volumetric attacks overwhelm WAN circuits with tens of gigabits per second of meaningless traffic–so-called ICMP or UDP floods. > > Layer 3 attacks abuse TCP. For example, SYN floods overload network equipment by starting but never completing thousands of TCP sessions using forged sender addresses. SYN floods can be in excess of 1 million packets per second, largely in response to the wider deployment of hardware countermeasures on firewalls and other security appliances, says Neal Quinn, COO of DDoS mitigation specialist Prolexic. > > Layer 7 floods use HTTP GET or POST requests to overload application and Web servers. From the attacker’s perspective, L7 exploits aren’t anonymous. The attacking client’s identity (IP address) is exposed because a TCP handshake must be completed. Attackers who use this approach consider the risk outweighed by the technique’s effectiveness at much lower volumes and the traffic’s stealthy nature. Requests are designed to look like normal Web traffic, factors that make L7 attacks hard to detect. Our InformationWeek 2012 Strategic Security Survey shows that the increasing sophistication of threats is the most-cited reason for worry among respondents who say their orgs are more vulnerable now than in 2011, and L7 attacks are certainly sophisticated. They’re also getting more common: Mark Teolis, founder and CEO of DOSarrest , a DDoS mitigation service, says 85% of the attacks his company sees have a Layer 7 component. Attackers leveraging L7 are often developers; they may do some reconnaissance on a website, looking for page requests that aren’t cacheable and are very CPU-intensive–things like filling a shopping cart, searching a database, or posting a complex form. Teolis says that a mere 2 to 3 Mbps increase in specially crafted L7 traffic can be crippling. “We’ve had gaming sites tell us they can handle 30,000 customers, but if 100 hit this one thing, it’ll bring down the entire site,” he says. Layer 7 attacks are tough to defeat not only because the incremental traffic is minimal, but because it mimics normal user behavior. Teolis has seen attacks where an individual bot may hit a site only once or twice an hour–but there are 20,000 bots involved. Conventional network security appliances just can’t handle that kind of scenario. And meanwhile, legitimate customers can’t reach your site. Why Us? The motivations for a DDoS attack are as varied as the perpetrators. For many, it’s just business, with targets strategically chosen by cyber criminals. Others are political–a prime example is LulzSec hitting the Arizona Department of Public Safety to protest the state’s strict immigration law, SB 1070. And for some, it’s just sport. Given this randomness, it’s impossible to predict the need for professional distributed denial-of-service mitigation. For example, Teolis says one of DOSarrest ‘s customers was the Dog Whisperer, that guru of man’s best friend. “If Cesar Millan can get attacked, anyone is fair game,” he says. Purchasing mitigation services requires the same kind of budgeting as any form of IT security: What you spend on controls should be proportional to the value of the data or website. So, while any organization with an online presence is at some risk, those with financial or reputational assets that could be seriously damaged by going dark should take DDoS mitigation most seriously. Everyone should take these preparatory steps. > > Do online reconnaissance: Follow what’s being said about your company online, particularly on public social networks, and look for chatter that might hint at extortion or hacktivism. Subscribe to security threat assessment reports covering the latest DDoS techniques and incidents. Prolexic is one source for threat advisories; US-CERT also has overviews, like this one on Anonymous. > > Heed threat mitigation recommendations: DDoS threat reports typically include details about the attack signature and recommended mitigation steps. For example, a recent Prolexic report on the High Orbit Ion Cannon identifies specific attack signatures, in this case HTTP requests, and content filter rules to block them. For L3/L4 attacks, incorporate these rules into your firewall; do likewise for L7 attacks if your firewall supports application-layer filtering. > > Have a communications strategy: Know what you’ll tell employees, customers, and the media should you be the victim of an attack. Don’t wait to make statements up on the fly. > > Have an emergency mitigation backup plan: Although most DDoS mitigation services operate on a monthly subscription basis, if you haven’t signed up and an attack overwhelms your defenses, at least know who you’re gonna call. Quinn and Teolis say their services can be operational and filtering DDoS traffic within minutes, though of course it will cost you. What To Look For In DDoS Mitigation At the risk of oversimplification, DDoS mitigation services are fundamentally remote network traffic filters. Once your system detects an attack affecting your network or servers, you redirect traffic to the service; the service filters out the junk and passes legitimate packets to their original destinations. In this sense, it’s like a cloud-based spam filter for websites. This traffic redirection, so-called on-ramping, is typically done via DNS. The mitigation provider creates a virtual IP address, the customer makes a DNS A record (hostname) change pointing to the remote VIPA, traffic flows through the mitigation provider’s filters, and the provider forwards only legitimate traffic on to the original site. Those facing attacks on multiple systems can divert entire subnets using Border Gateway Protocol advertisements, using Generic Routing Encapsulation tunneling to direct traffic to the mitigation provider. Advertising a new route to an entire address block protects an entire group of machines and, says Quinn, has the advantage of being asymmetrical, in that the mitigation service is used only for inbound traffic. The most important DDoS mitigation features are breadth of attack coverage, speed of service initiation (traffic on-ramping), and traffic capacity. Given the increasing popularity of application-layer attacks, any service should include both L3/4 and L7 mitigation technology. Services may segment features into proactive, before-the-attack monitoring and reactive, during-the-incident mitigation. Customers with monthly subscriptions should demand typical and maximum mitigation times–measured in minutes, not hours–backed up by a service-level agreement with teeth. Even those procuring emergency mitigation services should expect fairly rapid response. Most DDoS specialists staff operations centers 24/7. With DDoS mitigation, procrastination can be expensive. For those 70% of customers who first turn to DOSarrest in an emergency, the setup fee for the first month is around $3,500 to $4,000, depending on the complexity of the site. In contrast, an average monthly cost on a subscription basis is $700 per public-facing IP address. Filtered bandwidth is another way to differentiate between services. Some, like Prolexic, adopt an all-you-can-eat pricing model. For a flat fee per server, customers can use the service as often as they need with as much bandwidth as required. Others, like DOSarrest , keep the “use as often as you like” model but include only a certain amount of clean bandwidth (10 Mbps in its case) in the base subscription, charging extra for higher-bandwidth tiers. Teolis says 10 Mbps is sufficient for at least 90% of his company’s customers. A few services use a pricing model akin to an attorney’s retainer, with a low monthly subscription but hefty fees for each DDoS incident. Richter says Savvis is moving to this model, saying that customers want usage-based pricing that resembles other cloud services. Prolexic’s Quinn counters that this pricing structure leads to unpredictable bills. Bottom line, there’s a DDoS service to suit your tolerance for risk and budgetary volatility. Optional services available from some providers include postattack analysis and forensics (what happened, from where, and by whom) and access to a managed network reputation database that tracks active botnets and sites linked to fraudulent or criminal activity, a feature that facilitates automated blacklisting to help prevent attacks in the first place. Aside from looking at service features, evaluate each company’s technical expertise and track record. DDoS mitigation specialists, for whom this is a core business (or perhaps their only business) arguably have more experience and focus than Internet service providers or managed security providers for which DDoS mitigation is just a sideline. Not surprisingly, Quinn, whose company was among the first to offer DDoS mitigation as a service, suggests customers should make vendors show evidence that DDoS mitigation is something they do regularly, not as a rare occurrence. Make sure the service has highly qualified staff dedicated to the task. Ask whether the provider has experts available 24/7 and how long it will take to access someone with the technical ability and authority to work on your problem. Unfortunately there’s no rule of thumb for measuring the DDoS mitigation return on investment; it’s really a case-by-case calculation based on the financial value of the site being attacked. It relies on factors such as the cost in lost revenue or organizational reputation for every minute of downtime. Quinn cites a common analyst cost estimate, which Cisco also uses in its product marketing, of $30 million for a 24-hour outage at a large e-commerce site. There’s a cruel asymmetry to DDoS attacks: They can cost thousands to mitigate, inflict millions in damage, and yet attackers can launch them on the cheap. A small botnet can be rented for as little as $600 a month, meaning a serious, sustained attack against multiple targets can be pulled off for $5,000 or $10,000. With damages potentially two or three orders of magnitude higher than the DDoS mitigation costs, many organizations are finding mitigation a worthwhile investment. In fact, three-quarters of DOSarrest ‘s customers don’t wait for a DDoS attack to flip the switch, but permanently filter all of their traffic through the service. That makes sense, particularly if it’s a high-value or high-visibility site, if your traffic fits within the cap, or if you’re using an uncapped service like Prolexic. These services use the same sorts of colocation hosting centers where companies would typically house public-facing websites, and they do geographically distributed load balancing and traffic routing to multiple data centers. That makes the risk of downtime on the provider’s end minimal. And this approach could actually reduce WAN costs since it filters junk before it ever touches your systems. Recommendations If a mitigation service is too expensive, there are things IT can do to lower the exposure and limit the damage from DDoS attacks (discussed more in depth in our full report): 1. Fortify your edge network: Ensure that firewall and IDS systems have DoS features turned on, including things like dropping spoofed or malformed packets, setting SYN, ICMP, and UDP flood drop thresholds, limiting connections per server and client, and dynamically filtering and automatically blocking (at least for a short time) clients sending bad packets. 2. Develop a whitelist of known good external systems: These include business partner gateways, ISP links and cloud providers. This ensures that stringent edge filtering, whether done on your firewall or by a DDoS service, lets good traffic through. 3. Perform regular audits and reviews of your edge devices: Look for anomalies like bandwidth spikes. This works best if the data is centrally collected and analyzed across every device in your network. 4. Understand how to identify DDoS traffic: Research attack signatures and have someone on your network team who knows how to use a packet sniffer to discriminate between legitimate and DDoS traffic. 5. Prepare DNS: Lower the DNS TTL for public-facing Web servers, since these are most likely to be attacked. If you need to protect an entire server subnet, have a plan to readvertise BGP routes to a mitigation service. 6. Keep public Web servers off your enterprise ISP link: With Web servers being the most common DDoS target, Michael Davis, CEO of Savid Technologies and a regular InformationWeek contributor, recommends Web hosting with a vendor that doesn’t share your pipes. “Your website may be down, but at least the rest of your business is up,” says Davis. 7. Practice good server and application security hygiene: Layer 7 attacks exploit operating system and application security flaws, often using buffer overflows to inject attack code into SQL databases or Web servers, so keep systems patched. For DDoS protection please click here . Source: Darkreading
Late last month, two members of the hacker group LulzSec pleaded guilty to launching distributed denial-of-service (DDoS) attacks against entities ranging from the state of Arizona to Nintendo to the CIA. Yet despite extensive media coverage of such attacks, chief information security officers are still surprised when their companies get hit. This is not an unforeseeable lightning bolt from the blue, people. The cyber world is full of anonymous arsonists, and too many businesses are operating without a fire department on call. A few sprinklers won’t cut it when things flare out of control. Firewalls and intrusion-prevention system appliances are no substitute for specialized DDoS backup when an attack escalates. Proactively securing a mitigation service can be a good insurance policy–in fact, it’s better than insurance, which pays off only after damage is done. That’s because mitigation services are designed to prevent destruction from occurring in the first place. Not only can a mitigation service act as a deterrent–many attackers will move on to easier prey when they see an initial DDoS attack fail–but these providers have the capacity and expertise to rapidly scale DDoS countermeasures against coordinated, professional attacks. That can mean keeping your website online even under heavy bombardment. Big And Small Companies At Risk Denial-of-service attacks used to be something that happened to other people, those with high online visibility. Not anymore. “We’ve seen very small companies come to us and they can’t figure out why they’re under attack,” says Chris Richter, VP of security products and services at Savvis. They ask, “‘What have we done?’” Blame the proliferation of prepackaged DDoS toolkits, such as the Low Orbit Ion Cannon and Dirt Jumper, for the fact that no one’s safe. Like any brute-force tactic, DDoS relies on the fact that any attack, even the most rudimentary, repeated with sufficient volume and frequency, can effectively shut down a network or website. Botnets often span thousands or millions of systems worldwide; Akamai, for example, provides a real-time attack heat map. In early July, attack rates were almost 30% above normal, with hot spots in Delaware and Italy. Geographic dispersion, coupled with network traffic crafted to look like legitimate connections from normal users, makes DDoS attacks both extremely effective and difficult to defeat if you’re not an expert with the right tools. There are three main distributed denial-of-service categories: > > Volumetric attacks overwhelm WAN circuits with tens of gigabits per second of meaningless traffic–so-called ICMP or UDP floods. > > Layer 3 attacks abuse TCP. For example, SYN floods overload network equipment by starting but never completing thousands of TCP sessions using forged sender addresses. SYN floods can be in excess of 1 million packets per second, largely in response to the wider deployment of hardware countermeasures on firewalls and other security appliances, says Neal Quinn, COO of DDoS mitigation specialist Prolexic. > > Layer 7 floods use HTTP GET or POST requests to overload application and Web servers. From the attacker’s perspective, L7 exploits aren’t anonymous. The attacking client’s identity (IP address) is exposed because a TCP handshake must be completed. Attackers who use this approach consider the risk outweighed by the technique’s effectiveness at much lower volumes and the traffic’s stealthy nature. Requests are designed to look like normal Web traffic, factors that make L7 attacks hard to detect. Our InformationWeek 2012 Strategic Security Survey shows that the increasing sophistication of threats is the most-cited reason for worry among respondents who say their orgs are more vulnerable now than in 2011, and L7 attacks are certainly sophisticated. They’re also getting more common: Mark Teolis, founder and CEO of DOSarrest , a DDoS mitigation service, says 85% of the attacks his company sees have a Layer 7 component. Attackers leveraging L7 are often developers; they may do some reconnaissance on a website, looking for page requests that aren’t cacheable and are very CPU-intensive–things like filling a shopping cart, searching a database, or posting a complex form. Teolis says that a mere 2 to 3 Mbps increase in specially crafted L7 traffic can be crippling. “We’ve had gaming sites tell us they can handle 30,000 customers, but if 100 hit this one thing, it’ll bring down the entire site,” he says. Layer 7 attacks are tough to defeat not only because the incremental traffic is minimal, but because it mimics normal user behavior. Teolis has seen attacks where an individual bot may hit a site only once or twice an hour–but there are 20,000 bots involved. Conventional network security appliances just can’t handle that kind of scenario. And meanwhile, legitimate customers can’t reach your site. Why Us? The motivations for a DDoS attack are as varied as the perpetrators. For many, it’s just business, with targets strategically chosen by cyber criminals. Others are political–a prime example is LulzSec hitting the Arizona Department of Public Safety to protest the state’s strict immigration law, SB 1070. And for some, it’s just sport. Given this randomness, it’s impossible to predict the need for professional distributed denial-of-service mitigation. For example, Teolis says one of DOSarrest ‘s customers was the Dog Whisperer, that guru of man’s best friend. “If Cesar Millan can get attacked, anyone is fair game,” he says. Purchasing mitigation services requires the same kind of budgeting as any form of IT security: What you spend on controls should be proportional to the value of the data or website. So, while any organization with an online presence is at some risk, those with financial or reputational assets that could be seriously damaged by going dark should take DDoS mitigation most seriously. Everyone should take these preparatory steps. > > Do online reconnaissance: Follow what’s being said about your company online, particularly on public social networks, and look for chatter that might hint at extortion or hacktivism. Subscribe to security threat assessment reports covering the latest DDoS techniques and incidents. Prolexic is one source for threat advisories; US-CERT also has overviews, like this one on Anonymous. > > Heed threat mitigation recommendations: DDoS threat reports typically include details about the attack signature and recommended mitigation steps. For example, a recent Prolexic report on the High Orbit Ion Cannon identifies specific attack signatures, in this case HTTP requests, and content filter rules to block them. For L3/L4 attacks, incorporate these rules into your firewall; do likewise for L7 attacks if your firewall supports application-layer filtering. > > Have a communications strategy: Know what you’ll tell employees, customers, and the media should you be the victim of an attack. Don’t wait to make statements up on the fly. > > Have an emergency mitigation backup plan: Although most DDoS mitigation services operate on a monthly subscription basis, if you haven’t signed up and an attack overwhelms your defenses, at least know who you’re gonna call. Quinn and Teolis say their services can be operational and filtering DDoS traffic within minutes, though of course it will cost you. What To Look For In DDoS Mitigation At the risk of oversimplification, DDoS mitigation services are fundamentally remote network traffic filters. Once your system detects an attack affecting your network or servers, you redirect traffic to the service; the service filters out the junk and passes legitimate packets to their original destinations. In this sense, it’s like a cloud-based spam filter for websites. This traffic redirection, so-called on-ramping, is typically done via DNS. The mitigation provider creates a virtual IP address, the customer makes a DNS A record (hostname) change pointing to the remote VIPA, traffic flows through the mitigation provider’s filters, and the provider forwards only legitimate traffic on to the original site. Those facing attacks on multiple systems can divert entire subnets using Border Gateway Protocol advertisements, using Generic Routing Encapsulation tunneling to direct traffic to the mitigation provider. Advertising a new route to an entire address block protects an entire group of machines and, says Quinn, has the advantage of being asymmetrical, in that the mitigation service is used only for inbound traffic. The most important DDoS mitigation features are breadth of attack coverage, speed of service initiation (traffic on-ramping), and traffic capacity. Given the increasing popularity of application-layer attacks, any service should include both L3/4 and L7 mitigation technology. Services may segment features into proactive, before-the-attack monitoring and reactive, during-the-incident mitigation. Customers with monthly subscriptions should demand typical and maximum mitigation times–measured in minutes, not hours–backed up by a service-level agreement with teeth. Even those procuring emergency mitigation services should expect fairly rapid response. Most DDoS specialists staff operations centers 24/7. With DDoS mitigation, procrastination can be expensive. For those 70% of customers who first turn to DOSarrest in an emergency, the setup fee for the first month is around $3,500 to $4,000, depending on the complexity of the site. In contrast, an average monthly cost on a subscription basis is $700 per public-facing IP address. Filtered bandwidth is another way to differentiate between services. Some, like Prolexic, adopt an all-you-can-eat pricing model. For a flat fee per server, customers can use the service as often as they need with as much bandwidth as required. Others, like DOSarrest , keep the “use as often as you like” model but include only a certain amount of clean bandwidth (10 Mbps in its case) in the base subscription, charging extra for higher-bandwidth tiers. Teolis says 10 Mbps is sufficient for at least 90% of his company’s customers. A few services use a pricing model akin to an attorney’s retainer, with a low monthly subscription but hefty fees for each DDoS incident. Richter says Savvis is moving to this model, saying that customers want usage-based pricing that resembles other cloud services. Prolexic’s Quinn counters that this pricing structure leads to unpredictable bills. Bottom line, there’s a DDoS service to suit your tolerance for risk and budgetary volatility. Optional services available from some providers include postattack analysis and forensics (what happened, from where, and by whom) and access to a managed network reputation database that tracks active botnets and sites linked to fraudulent or criminal activity, a feature that facilitates automated blacklisting to help prevent attacks in the first place. Aside from looking at service features, evaluate each company’s technical expertise and track record. DDoS mitigation specialists, for whom this is a core business (or perhaps their only business) arguably have more experience and focus than Internet service providers or managed security providers for which DDoS mitigation is just a sideline. Not surprisingly, Quinn, whose company was among the first to offer DDoS mitigation as a service, suggests customers should make vendors show evidence that DDoS mitigation is something they do regularly, not as a rare occurrence. Make sure the service has highly qualified staff dedicated to the task. Ask whether the provider has experts available 24/7 and how long it will take to access someone with the technical ability and authority to work on your problem. Unfortunately there’s no rule of thumb for measuring the DDoS mitigation return on investment; it’s really a case-by-case calculation based on the financial value of the site being attacked. It relies on factors such as the cost in lost revenue or organizational reputation for every minute of downtime. Quinn cites a common analyst cost estimate, which Cisco also uses in its product marketing, of $30 million for a 24-hour outage at a large e-commerce site. There’s a cruel asymmetry to DDoS attacks: They can cost thousands to mitigate, inflict millions in damage, and yet attackers can launch them on the cheap. A small botnet can be rented for as little as $600 a month, meaning a serious, sustained attack against multiple targets can be pulled off for $5,000 or $10,000. With damages potentially two or three orders of magnitude higher than the DDoS mitigation costs, many organizations are finding mitigation a worthwhile investment. In fact, three-quarters of DOSarrest ‘s customers don’t wait for a DDoS attack to flip the switch, but permanently filter all of their traffic through the service. That makes sense, particularly if it’s a high-value or high-visibility site, if your traffic fits within the cap, or if you’re using an uncapped service like Prolexic. These services use the same sorts of colocation hosting centers where companies would typically house public-facing websites, and they do geographically distributed load balancing and traffic routing to multiple data centers. That makes the risk of downtime on the provider’s end minimal. And this approach could actually reduce WAN costs since it filters junk before it ever touches your systems. Recommendations If a mitigation service is too expensive, there are things IT can do to lower the exposure and limit the damage from DDoS attacks (discussed more in depth in our full report): 1. Fortify your edge network: Ensure that firewall and IDS systems have DoS features turned on, including things like dropping spoofed or malformed packets, setting SYN, ICMP, and UDP flood drop thresholds, limiting connections per server and client, and dynamically filtering and automatically blocking (at least for a short time) clients sending bad packets. 2. Develop a whitelist of known good external systems: These include business partner gateways, ISP links and cloud providers. This ensures that stringent edge filtering, whether done on your firewall or by a DDoS service, lets good traffic through. 3. Perform regular audits and reviews of your edge devices: Look for anomalies like bandwidth spikes. This works best if the data is centrally collected and analyzed across every device in your network. 4. Understand how to identify DDoS traffic: Research attack signatures and have someone on your network team who knows how to use a packet sniffer to discriminate between legitimate and DDoS traffic. 5. Prepare DNS: Lower the DNS TTL for public-facing Web servers, since these are most likely to be attacked. If you need to protect an entire server subnet, have a plan to readvertise BGP routes to a mitigation service. 6. Keep public Web servers off your enterprise ISP link: With Web servers being the most common DDoS target, Michael Davis, CEO of Savid Technologies and a regular InformationWeek contributor, recommends Web hosting with a vendor that doesn’t share your pipes. “Your website may be down, but at least the rest of your business is up,” says Davis. 7. Practice good server and application security hygiene: Layer 7 attacks exploit operating system and application security flaws, often using buffer overflows to inject attack code into SQL databases or Web servers, so keep systems patched. For DDoS protection please click here . Source: Darkreading
Continued here:
How To Select A Distributed Denial of Service ‘DDoS’ Mitigation Service

