The FBI says it has credible evidence to link the Chinese government to attackers who leveraged two Chinese telecom companies and the Baidu search engine to carry out recent distributed denial of service (DDoS) attacks targeting unnamed U.S. websites. The FBI issued a confidential Flash Alert to U.S. companies alleging that the Chinese government sanctioned activities in which Internet traffic was “manipulated to create cyber attacks directed at U.S.-based websites” using man-in-the-middle (MitM) techniques. “Analysis by the U.S. government indicated that Internet traffic which originated outside China, was intercepted and modified to make unsuspecting users send repeated requests to U.S.-based websites,” the Flash Alert reportedly said. “The malicious activity occurred on China’s backbone Internet infrastructure, and temporarily disrupted all operations on the U.S.-based websites.” Analysis of the attacks revealed that malware was injected into the browsers of users when web traffic reached China Unicom or China Telecom networks – both state-owned telecommunications companies – “at the same points in these routes that censor traffic for the Chinese government.” “The location of the [man-in-the-middle] system on backbone networks operating censorship equipment indicates that the [man-in-the-middle] attack could not have occurred without some level of cooperation by the administrators of these systems,” the Alert said. “The malicious Javascript would direct the unsuspecting user’s browsers to make repeated requests to targeted U.S.-based websites.” While the FBI Flash Alert did not specify which company’s websites were attacked, it is likely that the popular web-based software developers collaboration platform GitHub was among those targeted. Researchers from the University of California at Berkeley, the University of Toronto, and Princeton recently published details of a powerful Chinese MitM tool dubbed the “Great Cannon,” which was used in DDoS attacks targeting websites operated by the anti-censorship project GreatFire.org, and later connected to the attacks on GitHub. “Specifically, the Cannon manipulates the traffic of ‘bystander’ systems outside China, silently programming their browsers to create a massive DDoS attack,” the researchers said. “The operational deployment of the Great Cannon represents a significant escalation in state-level information control: the normalization of widespread use of an attack tool to enforce censorship by weaponizing users.” GitHub was likely targeted because GreatFire.org had begun to mirror some content on the platform. The attacks against GreatFire employed the same techniques as those seen in the GitHub attack, which leveraged hijacked Internet traffic. “The web browser’s request for the Baidu javascript is detected by the Chinese passive infrastructure as it enters China. A fake response is sent out from within China instead of the actual Baidu Analytics script. This fake response is a malicious javascript that tells the user’s browser to continuously reload two specific pages on GitHub.com,” analysis of the attack revealed. This analysis aligns with details of the GreatFire.org attacks which was released previously. “Millions of global internet users, visiting thousands of websites hosted inside and outside China, were randomly receiving malicious code which was used to launch cyber-attacks against GreatFire.org’s websites. Baidu’s Analytics code (h.js) was one of the files replaced by malicious code which triggered the attacks,” officials at GreatFire.org said. “Baidu Analytics, akin to Google Analytics, is used by thousands of websites. Any visitor to any website using Baidu Analytics or other Baidu resources would have been exposed to the malicious code.” GreatFire.org said it has conclusive evidence that the Chinese government using the nation’s infrastructure to conduct the attacks, and had previously published a detailed report, which was further backed up by the analysis provided by the university researchers. “We show that, while the attack infrastructure is co-located with the Great Firewall, the attack was carried out by a separate offensive system, with different capabilities and design, that we term the Great Cannon,” the researchers wrote. “The Great Cannon is not simply an extension of the Great Firewall, but a distinct attack tool that hijacks traffic to (or presumably from) individual IP addresses, and can arbitrarily replace unencrypted content as a man-in-the-middle.” Source: http://en.hackdig.com/06/23256.htm
See the article here:
FBI Links Chinese Government to DDoS Attacks on US Websites


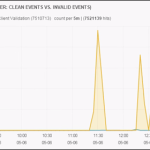 In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/
In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/