A denial-of-service attack, in which perpetrators flood a targeted website with requests that overwhelm the site’s servers, is believed to have caused Monday morning’s outage. A cyberattack took down The Seattle Times website for about 90 minutes Monday morning. Seattletimes.com was unavailable from about 8 a.m. to 9:30 a.m. as a result of a denial-of-service attack, company spokeswoman Jill Mackie said. “The Seattle Times website experienced technical problems Monday morning due to an external attack that appears to have targeted other sites,” Mackie said in a statement. “We continue to monitor the situation and apologize for any inconvenience this caused readers.” Denial-of-service attacks are designed to flood a website with requests, essentially overwhelming the site’s servers and preventing it from responding to other users. The result is a site that grinds to a halt or runs so slowly that it becomes unusable. Such attacks on their own aren’t designed to damage a target’s computer systems or steal files. The attacks, a fixture of Internet security threats for decades, have been blamed on culprits ranging from political operatives to young, tech-savvy hackers connected by social media. The ease with which such attacks could be orchestrated was illustrated in 2000 when a 15-year-old Canadian boy, working under the alias “Mafiaboy,” was able to temporarily bring down the websites of Yahoo, CNN and Amazon.com, among others. Mackie said The Seattle Times’ information technology staff believes Monday’s attack on the website was carried out by a cyberattack group that calls itself Vikingdom2015. The group is said to have targeted several government and media websites, including those of the Indiana state government and the Bangor (Maine) Daily News, with denial-of-service attacks. IBM security researchers said the group was formed from former members of the Team Cyber Poison hacker group, and began attacking websites this month. Source: http://www.seattletimes.com/business/technology/cyberattack-temporarily-blocks-seattletimescom/
View original post here:
DDoS attack temporarily blocks seattletimes.com

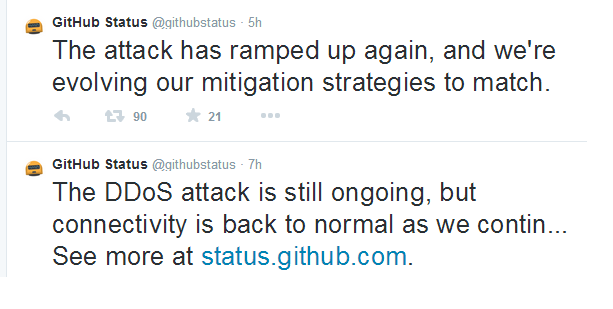
 San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/
San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/