Most experts agree that agencies can’t defend against and mitigate the impact of denial of service attacks all by themselves, but there are step they can take to strengthen their defenses. Denial of service — DOS — is a blanket term for a variety of types of attacks, carried out in numerous ways, all directed at making online resources unavailable to the public. Attacks can be launched from multiple platforms, creating a distributed denial of service attack, or DDOS. Although they usually do not damage the target systems or compromise data, they can damage reputations, cost money and interfere with carrying out missions. Specifics will vary with each attack, but the U.S. Computer Emergency Readiness Team notes that, “In general, the best practice for mitigating DDOS attacks involves advanced preparation.” Some recommendations for advance preparation from US-CERT include: Develop a checklist for standard operating procedures to follow in the event of an attack, including maintaining a checklist of contact information for internal firewall teams, intrusion detection teams and network teams, as well as for service providers. Identify who should be contacted during an attack, what processes should be followed by each and what information is needed. ISPs and hosting providers might provide mitigation services. Be aware of the service-level agreement provisions. Identify and prioritize critical services that should be maintained during an attack so IT staff will know what resources can be turned off or blocked as needed to limit the effects of the attack. Ensure that critical systems have sufficient capacity to withstand an attack. Keep network diagrams, IT infrastructure details and asset inventories current and available to help understand the environment. Have a baseline of the daily volume, type, and performance of network traffic to help identify the type, target and vector of attack. Identify existing bottlenecks and remediation actions needed. Harden the configuration settings of the network, operating systems and applications by disabling unnecessary services and applications. Implement a bogon (bogus IP address) block list at the network boundary to drop bogus IP traffic. Employ service screening on edge routers where possible to decrease the load on stateful security devices such as firewalls. Separate or compartmentalize critical services, including public and private services; intranet, extranet, and Internet services; and create single-purpose servers for services such as HTTP, FTP, and DNS. Some additional advice for preparing yourself from Marc Gaffan, cofounder of Incapsula: Have the capacity to absorb additional traffic. It might be impractical to provision all the bandwidth needed, and the exact amount to have available will be a business decision. But a good rule of thumb would be to maintain about 150 percent of normally needed capacity. Maintain customer transparency. Ideally, people coming to the site shouldn’t know it is defending itself against an attack. “People don’t like to hang around where something bad is going on,” Gaffan said. And if a bogus connection is suspected, give the user a chance to verify. It might be impractical to use additional security such as Captcha verification for every connection during an attack, but don’t arbitrarily drop every questionable connection. Differentiate between legitimate automated traffic and DOS traffic. There can be a high volume of legitimate automated traffic generated by search engine crawls and management tools that should not be blocked. Knowing what this traffic looks like in advance can help identify DOS traffic. Be prepared to quickly identify and respond to DOS attacks so that defenses can be brought to bear quickly, minimizing downtime. For DDoS protection against your eCommerce site click here . Source: http://gcn.com/Articles/2013/01/24/9-steps-defend-against-DDOS.aspx?Page=2
Originally posted here:
9 steps that help defend against Distributed Denial of Service (DDoS) Attacks

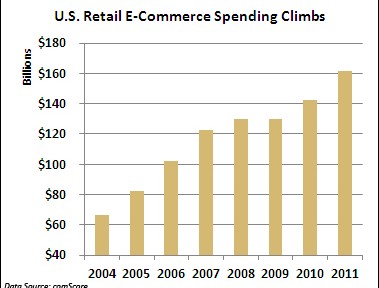
 A string of cyber attacks on U.S. financial institutions has created headaches this fall by slowing down or preventing online banking access for millions of Americans. But imagine the real economic damage that similar-style attacks would cause if they struck U.S. retailers this holiday-shopping season, potentially eating into projected online sales of $54 billion. While retailers deserve credit for bolstering their defenses against credit-card-hungry organized crime rings, security professionals believe the industry is vulnerable to this different kind of onslaught aimed at crippling online sales. “The gloves are off in cyber space. The reality is if they want it to get worse, it can get worse,” said Dave Aitel, a former computer scientist at the National Security Agency. “I don’t think people are really prepared mentally to what happens if Amazon goes down.” Unlike the ongoing cyber attacks against U.S. banks, there doesn’t appear to be a specific cyber threat against retailers. Yet there are concerns that retailers aren’t ready for denial-of-service (DDoS) attacks from a powerful state actor like Iran, which many in the U.S. government suspect had a hand in the recent attacks on financial institutions like Bank of America (BAC) and J.P. Morgan Chase (JPM). “The Iranians are in the business of making a point and the bank attacks are not likely to have the impact they need, hence retailers are the next most likely target, especially in the holiday season,” said Aitel, CEO of Immunity, a cyber security firm that works with Fortune 500 companies. Online Sales Exceed $160B It’s hard to overstate the importance of e-commerce in today’s smartphone and social network dominated world. According to comScore (CSOR), annual U.S. retail e-commerce spending has surged 143% since 2004 to $161.52 billion last year. Despite the sluggish domestic economy and tepid retail sales growth, e-commerce spending jumped 13% between 2010 and 2011. Online shopping is crucial during the all-important holiday-shopping season. E-commerce spending rose 14% last holiday season to $37.2 billion, comScore said. In the face of continued economic uncertainty, online spending is projected to climb 17% this season to $54.47 billion, according to MarketLive. “It’s very important for any retailer to have a web presence or you risk being left out in the cold,” said Andrew Lipsman, vice president of industry analysis at comScore, who noted that even in-person purchases typically originate online. Adapting to Shifting Threat Security professionals believe retailers’ cyber defenses are more porous than those of financial institutions — and even some banks succumbed to relentless DDoS attacks this fall. Given their prior experience combating thieves in Russia and elsewhere trying to siphon funds or snatch credit-card numbers, retailers aren’t really positioned to halt massive DDoS attacks from powerful state actors like Iran. “That’s a very different threat and in many ways is more severe,” said Aitel. “They’re not thinking: What if it’s not about the money? What if someone wants to take me out just to take me out?” Cedric Leighton, a former NSA official, said he agrees that retailers are not as well prepared as their financial peers. “I don’t think they’ve gotten to the point where they can truly say their whole cyber supply chain is as well secured as they need to be in this day and age,” said Leighton, CEO of a Washington, D.C.-based risk-management consultancy. Leighton said hackers could also disrupt companies’ supply chains by messing with order quantities and locations, creating costly problems for retailers. Just this week Barnes & Noble (BKS) fell victim to a very sophisticated criminal attack that may have resulted in stolen credit and debit card information at 63 of its stores. Amazon Atop Target List The importance of a robust cyber defense is even more important for online retailers like Amazon.com and Overstock (OSTK). “If they aren’t available online, there is no business. They don’t exist,” said Ronen Kenig, director of security product marketing at Tel Aviv-based security firm Radware (RDWR). In a potential cyber attack on U.S. retailers, Amazon.com would clearly be the biggest prize. The Seattle company generated $17.4 billion in revenue last holiday quarter. “When you attack the United States you don’t attack Topeka, Kansas,” said Aitel. “Amazon is the big boy on the block. They are of course also the best protected.” Amazon.com and Wal-Mart (WMT) declined to comment for this story, while Target (TGT) didn’t respond to a request for comment. “Every company is going to look at what its exposure is. The greater the company is placed at risk, then the more they are going to invest in trying to protect themselves,” said Mallory Duncan, general counsel at the National Retail Federation. Noting that some companies “rely extremely heavily on the Internet,” Duncan said, “When you have a bet-the-company type of situation, they’re going to take extraordinary steps to protect that channel.” Cyber Monday in Focus Aitel suggested the days around Cyber Monday — the first work day after Black Friday — as a time when retailers need to be particularly vigilant about the cyber threat. According to comScore, U.S. e-commerce spending on Cyber Monday rose 22% last year to $1.25 billion, making it the highest online spending day in history. “The attackers always like to choose the worst time for the victim,” said Kenig. Bolstering Cyber Defenses So what specifically should retailers be doing to prevent or mitigate the impact of DDoS attacks this holiday season? Leighton said it’s crucial for companies to implement redundant systems with backups that allow switching from one system to the other when necessary. From a bigger picture standpoint, retailers should strive to install security programs that go above and beyond industry security standards, which Aitel said “are really the bottom bar.” Security professionals have been particularly alarmed by some recent cyber attacks that inflicted damage on physical assets, including a devastating attack unleashed on Saudi Arabia’s state run oil company Saudi Aramco Some believe Iran may have been behind this attack, which destroyed an estimated 30,000 computers. Aitel said, “Companies have to look at what happened to Saudi Aramco and say: What would we do if that happened to us? Until they have a good answer for that, they shouldn’t be sleeping that well.” For advanced DDoS protection against your eCommerce site click here . Source: http://www.foxbusiness.com/industries/2012/10/24/would-cyber-attacks-ruin-christmas-for-retailers/
A string of cyber attacks on U.S. financial institutions has created headaches this fall by slowing down or preventing online banking access for millions of Americans. But imagine the real economic damage that similar-style attacks would cause if they struck U.S. retailers this holiday-shopping season, potentially eating into projected online sales of $54 billion. While retailers deserve credit for bolstering their defenses against credit-card-hungry organized crime rings, security professionals believe the industry is vulnerable to this different kind of onslaught aimed at crippling online sales. “The gloves are off in cyber space. The reality is if they want it to get worse, it can get worse,” said Dave Aitel, a former computer scientist at the National Security Agency. “I don’t think people are really prepared mentally to what happens if Amazon goes down.” Unlike the ongoing cyber attacks against U.S. banks, there doesn’t appear to be a specific cyber threat against retailers. Yet there are concerns that retailers aren’t ready for denial-of-service (DDoS) attacks from a powerful state actor like Iran, which many in the U.S. government suspect had a hand in the recent attacks on financial institutions like Bank of America (BAC) and J.P. Morgan Chase (JPM). “The Iranians are in the business of making a point and the bank attacks are not likely to have the impact they need, hence retailers are the next most likely target, especially in the holiday season,” said Aitel, CEO of Immunity, a cyber security firm that works with Fortune 500 companies. Online Sales Exceed $160B It’s hard to overstate the importance of e-commerce in today’s smartphone and social network dominated world. According to comScore (CSOR), annual U.S. retail e-commerce spending has surged 143% since 2004 to $161.52 billion last year. Despite the sluggish domestic economy and tepid retail sales growth, e-commerce spending jumped 13% between 2010 and 2011. Online shopping is crucial during the all-important holiday-shopping season. E-commerce spending rose 14% last holiday season to $37.2 billion, comScore said. In the face of continued economic uncertainty, online spending is projected to climb 17% this season to $54.47 billion, according to MarketLive. “It’s very important for any retailer to have a web presence or you risk being left out in the cold,” said Andrew Lipsman, vice president of industry analysis at comScore, who noted that even in-person purchases typically originate online. Adapting to Shifting Threat Security professionals believe retailers’ cyber defenses are more porous than those of financial institutions — and even some banks succumbed to relentless DDoS attacks this fall. Given their prior experience combating thieves in Russia and elsewhere trying to siphon funds or snatch credit-card numbers, retailers aren’t really positioned to halt massive DDoS attacks from powerful state actors like Iran. “That’s a very different threat and in many ways is more severe,” said Aitel. “They’re not thinking: What if it’s not about the money? What if someone wants to take me out just to take me out?” Cedric Leighton, a former NSA official, said he agrees that retailers are not as well prepared as their financial peers. “I don’t think they’ve gotten to the point where they can truly say their whole cyber supply chain is as well secured as they need to be in this day and age,” said Leighton, CEO of a Washington, D.C.-based risk-management consultancy. Leighton said hackers could also disrupt companies’ supply chains by messing with order quantities and locations, creating costly problems for retailers. Just this week Barnes & Noble (BKS) fell victim to a very sophisticated criminal attack that may have resulted in stolen credit and debit card information at 63 of its stores. Amazon Atop Target List The importance of a robust cyber defense is even more important for online retailers like Amazon.com and Overstock (OSTK). “If they aren’t available online, there is no business. They don’t exist,” said Ronen Kenig, director of security product marketing at Tel Aviv-based security firm Radware (RDWR). In a potential cyber attack on U.S. retailers, Amazon.com would clearly be the biggest prize. The Seattle company generated $17.4 billion in revenue last holiday quarter. “When you attack the United States you don’t attack Topeka, Kansas,” said Aitel. “Amazon is the big boy on the block. They are of course also the best protected.” Amazon.com and Wal-Mart (WMT) declined to comment for this story, while Target (TGT) didn’t respond to a request for comment. “Every company is going to look at what its exposure is. The greater the company is placed at risk, then the more they are going to invest in trying to protect themselves,” said Mallory Duncan, general counsel at the National Retail Federation. Noting that some companies “rely extremely heavily on the Internet,” Duncan said, “When you have a bet-the-company type of situation, they’re going to take extraordinary steps to protect that channel.” Cyber Monday in Focus Aitel suggested the days around Cyber Monday — the first work day after Black Friday — as a time when retailers need to be particularly vigilant about the cyber threat. According to comScore, U.S. e-commerce spending on Cyber Monday rose 22% last year to $1.25 billion, making it the highest online spending day in history. “The attackers always like to choose the worst time for the victim,” said Kenig. Bolstering Cyber Defenses So what specifically should retailers be doing to prevent or mitigate the impact of DDoS attacks this holiday season? Leighton said it’s crucial for companies to implement redundant systems with backups that allow switching from one system to the other when necessary. From a bigger picture standpoint, retailers should strive to install security programs that go above and beyond industry security standards, which Aitel said “are really the bottom bar.” Security professionals have been particularly alarmed by some recent cyber attacks that inflicted damage on physical assets, including a devastating attack unleashed on Saudi Arabia’s state run oil company Saudi Aramco Some believe Iran may have been behind this attack, which destroyed an estimated 30,000 computers. Aitel said, “Companies have to look at what happened to Saudi Aramco and say: What would we do if that happened to us? Until they have a good answer for that, they shouldn’t be sleeping that well.” For advanced DDoS protection against your eCommerce site click here . Source: http://www.foxbusiness.com/industries/2012/10/24/would-cyber-attacks-ruin-christmas-for-retailers/