In our five-minute CIO series, Lior Tabansky explains how cyberattacks could have a seismic effect on the world order. Lior Tabansky is a cyber power scholar at the Blavatnik Interdisciplinary Cyber Research Center (ICRC) and the director of strategy in Tel-Aviv-based cybersecurity consultancy firm CSG. Tabansky brings a refreshing interdisciplinary approach to cybersecurity to the table, facilitated by his political science and security studies, 15 years of hands-on IT professional practice, and high-level think tank, policy and corporate experience. His strategic cybersecurity expertise stems from a unique combination: service in the Israeli Air Force, subsequent career designing and managing business ICT infrastructure, postgraduate political science education and a proven commitment to interdisciplinary, academic policy-oriented research. Tabansky recently wrote an insightful and timely book – Cybersecurity in Israel – co-authored with Prof Isaac Ben-Israel and published by Springer. This comprehensive yet concise work offers an ‘insider’ strategic analysis of Israeli cyber power, with invaluable lessons to be learned by governments and corporations alike. How does one become a cyber scholar? I was always interested in politics and international relations because, since high school, I figured out this was important and I wanted to know how the world works. In parallel, around the mid-90s, the whole PC revolution happened and it fascinated me. And then you realise that things don’t work like they are supposed to, and I learned on my own to play with it and fix it and from there on, I pursued parallel academic tracks. One track was political science and security studies and, in parallel, I began working in IT as an admin because they paid more than other professions. Around 2003, I was doing a master’s on the role of IT in counter-terrorism and that’s how I became more established academically in this field. From there on, technology changed, and I was studying mostly the development of how it can challenge national security. Is most of your work academic? First of all, this subject is not very fashionable in academia because it is mostly current affairs; it relates to policy issues and is constantly moving, so it is on the fringes of the academic world. I had a lot of backlash for trying to pursue proper academic research with things that are constantly moving. It’s a conceptual issue. On top of that, the centre we established at Tel-Aviv University is more like a think tank in terms of influencing policy debates –it is mostly pure research. We also hold our Cyber Week conference in the summer, which attracts 5,000 people and delegations from 50 countries. With cyberattacks on the rise, every individual is threatened. How do you see the world we are in? This is not a purely defence issue, each one of us is affected. This is precisely why, as a civilisation, we build societies, states, cities and so on. The primary duty of the state is to provide security for society. Of course, you need to change a lot and adapt and this is where I think the west, and particularly the US, are doing a particularly bad job. They were the first to develop the whole field, to recognise and publish the deep implications of technology, and yet they are still all the time complaining about China, and now it has switched to Russia; but their governments fail to protect the companies, the citizens and civil society, and maybe they are not even trying. So, the failure is not even trying. This is a very typical problem. We are in the midst of a revolution similar to the industrial revolution and, unless society and states adapt, we will see dramatic shifts in world power. And, sitting where we are sitting, that is not a good thing. The shakes and tremors will come at everyone’s expense. Most of the rest of the world doesn’t like the western world’s dominance, and these are the ones who will continue to challenge the western way of life – it is a dangerous situation. Do you feel that the way the western world is going about cybersecurity – with an emphasis on surveillance rather than defence – is the wrong approach? Yes. It is not a resource issue. The US, for example, has by far the largest resources of all their competitors combined, definitely in defence and security. The NSA has been the largest employer of mathematicians for decades, so they are way ahead of all of us in that field. The problem is politics. How you work these things out and the balance between all sorts of values and security is very difficult, and, of course, no one knows how to get it right. It’s not a resource issue. The US has unlimited resources, manpower and technology, and they can get it right. If you try to focus too much on defence and security, you will harm civil liberties and so on, and no one wants that. The thing is, while we are figuring out how to solve it over the last few decades, your adversaries will try to act more and more in their interests. Has Israel gotten it right? There is much more to be done. We are relatively in a good situation compared to other western democracies. However, it is far away from the ideal situation that we have in security affairs. We pay taxes, we get security, and it works pretty well. Europe is in a great historic anomaly of having several decades of zero wars. This is only because societies got the defence issue right, which includes economics, diplomacy and other things. Unless we get it right in the cyber area, there will be changes. This is what history is about. And if we don’t get it right? Will some countries do better than others? There are a lot of instruments for cooperation between like-minded countries in terms of official bodies such as the EU and NATO and, more importantly, bilateral. This is where the strengths of the west lie, in the freedom to have people meet and develop new ideas. This is our best chance. It is a case of western civilisation versus the rest of the world that wants to compete with us. And yet, when it comes to security, organisations spend a fortune on cyber defence, only to have it unravel because one individual opens a phishing email … I’m happy to hear from you as a technology journalist acknowledge that technology can have human failure. From an information security perspective, we have a good empirical knowledge of how things happen. Most of the important breaches involve insiders; everything involves human behaviour. The top four strategies for cyber defence will mitigate 94pc of all breaches. There are already so many readily available, built-in technology solutions that we can use and yet we don’t, and the problem is with humans. This again brings me to society and politics, and policy and government issues, which are more complicated than a single solution or bunch of solutions. The other issue is, we do not know what the threats will look like. It is much worse when it is cyber because of the rate of change. Therefore, I don’t know if that is the official position of Israeli strategy but the underlying notion is, we don’t know what capability we will need in the future. It’s not like we can design a great aeroplane and it would take 20 years and we get there; we need to have an ecosystem in place that’s dynamic enough to identify changes and to adapt rapidly. It’s a dramatically different mindset from other defence issues. You can’t just plan ahead. It is much more complicated and you need to involve sectors of society, the private sector (whether they like it or not), the education system, academia. The main responsibility for national defence should be the defence organisations. In the last year, attacks such as WannaCry, and the various DDOS attacks on the internet of things and cloud organisations, suggest a worrying spike in attack capabilities. Do you agree? It is very predictable: if you take Moore’s Law and subsequent laws in networking and memory, and continue to extrapolate forward, yes, the internet of things is definitely going to happen. The complexity is growing, the number of potential threat vectors is growing, and it only means that you need to put in place better policies and prioritise where to put the limited funds we have. Unlike the Americans who have unlimited resources, in Israel, we don’t consider DDOS attacks a big problem, but of course we do things to prevent them. The Israeli government’s networks have been withstanding DDOS attacks, larger than the Estonians suffered in 2007, routinely. You need to assume things will go wrong and focus on the more narrow, more critical elements, because we cannot cover everything. Has the best attack not yet been invented? Since 2002, the government has legislated an arrangement for critical infrastructure protection. The concern was not information under threat, but the symbiosis between the operational technology and the information technology. I think this remains the major threat scenario: a disruptive or destructive attack on the systems that underpin our modern life. What would be the typical attack volume on Israel, what are you dealing with? State of the art! Whatever appears on the market, we usually get it first. Even 10 years ago, we had a lot of solutions readily available to deploy to mitigate massive DDOS attacks; even today, it is a matter of where you put your investment. If you spend enough money, you can mitigate any volume of DDOS attack, but is it worth the effort? Attackers are not interested in achieving the specific volume of attack, they are interested in achieving an effect. And the better your defences are, the more it helps you to incur higher costs on them. Source: https://www.siliconrepublic.com/enterprise/israel-cyber-defence
View article:
‘Cyberattacks could contribute to a dramatic shift in world power’
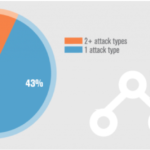 Information security company Verisign just published its Distributed Denial of Trends Report for Q1 2017. This report talks about changes in the frequency, size, and type of DDoS attack that the company has observed over the first few months of this year. The main takeaway is this: The number of DDoS attacks has plunged by 23 percent compared to the previous quarter. That’s good! However, the average peak attack size has increased by almost 26 percent, making them vastly more potent at taking down websites and critical online infrastructure. That’s bad. The report also notes that attacks are sophisticated in nature, and use several different attack types to take down a website. While 43 percent use just one attack vector, 25 percent use two, and six percent use five. This, obviously, makes it much more difficult to mitigate against. Verisign’s report also talks about the largest DDoS attack observed by the company in Q1. This was a multi-vector attack that peaked at 120 Gbps, and with a throughput of 90 Mpps. Per the report: This attack sent a flood of traffic to the targeted network in excess of 60 Gbps for more than 15 hours. The attackers were very persistent in their attempts to disrupt the victim’s network by sending attack traffic on a daily basis for over two weeks. The attack consisted primarily of TCP SYN and TCP RST floods of varying packet sizes and employed one of the signatures associated with the Mirai IoT botnet. The event also included UDP floods and IP fragments which increased the volume of the attack. So, in short. The attackers were using several different attack types, and they were able to sustain the attack over a long period of time. This shows the attacker has resources, either to create or rent a botnet of that size, and to sustain an attack over two weeks. The fact that DDoS attacks have increased in potency is hardly a surprise. They’ve been getting bigger and bigger, as bad actors figure out they can easily rope insecure Internet of Things (IoT) devices into their botnets. The Mirai botnet, for example, which took down Dyn last year, and with it much of the Internet, consisted of hundreds of thousands of insecure IoT products. The main thing you can gleam from the Verisign report is that DDoS attacks are increasingly professional, for lack of a better word. It’s not 2005 anymore. We’ve moved past the halcyon days of teenagers taking down sites with copies of LOIC they’d downloaded off Rapidshare. Now, it’s more potent. More commoditized. And the people operating them aren’t doing it for shits and giggles. Source: https://thenextweb.com/insider/2017/05/24/report-ddos-attacks-are-less-common-but-theyre-bigger/#.tnw_RJHfi1AZ
Information security company Verisign just published its Distributed Denial of Trends Report for Q1 2017. This report talks about changes in the frequency, size, and type of DDoS attack that the company has observed over the first few months of this year. The main takeaway is this: The number of DDoS attacks has plunged by 23 percent compared to the previous quarter. That’s good! However, the average peak attack size has increased by almost 26 percent, making them vastly more potent at taking down websites and critical online infrastructure. That’s bad. The report also notes that attacks are sophisticated in nature, and use several different attack types to take down a website. While 43 percent use just one attack vector, 25 percent use two, and six percent use five. This, obviously, makes it much more difficult to mitigate against. Verisign’s report also talks about the largest DDoS attack observed by the company in Q1. This was a multi-vector attack that peaked at 120 Gbps, and with a throughput of 90 Mpps. Per the report: This attack sent a flood of traffic to the targeted network in excess of 60 Gbps for more than 15 hours. The attackers were very persistent in their attempts to disrupt the victim’s network by sending attack traffic on a daily basis for over two weeks. The attack consisted primarily of TCP SYN and TCP RST floods of varying packet sizes and employed one of the signatures associated with the Mirai IoT botnet. The event also included UDP floods and IP fragments which increased the volume of the attack. So, in short. The attackers were using several different attack types, and they were able to sustain the attack over a long period of time. This shows the attacker has resources, either to create or rent a botnet of that size, and to sustain an attack over two weeks. The fact that DDoS attacks have increased in potency is hardly a surprise. They’ve been getting bigger and bigger, as bad actors figure out they can easily rope insecure Internet of Things (IoT) devices into their botnets. The Mirai botnet, for example, which took down Dyn last year, and with it much of the Internet, consisted of hundreds of thousands of insecure IoT products. The main thing you can gleam from the Verisign report is that DDoS attacks are increasingly professional, for lack of a better word. It’s not 2005 anymore. We’ve moved past the halcyon days of teenagers taking down sites with copies of LOIC they’d downloaded off Rapidshare. Now, it’s more potent. More commoditized. And the people operating them aren’t doing it for shits and giggles. Source: https://thenextweb.com/insider/2017/05/24/report-ddos-attacks-are-less-common-but-theyre-bigger/#.tnw_RJHfi1AZ 


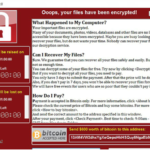 What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/
What is it ? WannaCry also know as WanaCrypt 2.0 is a form of malware commonly known as “Ransom Ware”. Where did it come from ? It was originally developed by the NSA in the US called “Eternal Blue” and was a way for them to secretly access computers. It was based on a flaw in windows machines, Unfortunately the NSA did not store this weaponized malware securely enough and someone hacked in and stole it. At this point it was loose and easily findable on the Internet. If you see a screen like this, you’re machine is definitely infected. Here is a link below from Microsoft to check/scan if your PC has a virus. https://www.microsoft.com/security/scanner/en-us/default.aspx Who is responsible for this ? At this point no one knows but there are a lot of smart people working on it and they will be caught eventually…This is my opinion. Is someone making money from this ? Yes, as with all ransom ware there is a money component.These are 3 discovered bitcoin Identifiers that victims are paying the ransom to Which is hardcoded into the Malware. As of 09:15 EST May 14, 2017 The total ransom paid is a total of $15,150.00 USD. This is surprisingly low, it’s definitely going to rise. Check for yourself on its progress by clicking the 3 links below. https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn How did my computer get infected ? If you’re on a corporate network, you most likely got it from another computer on your network. If you’re at home on a cable modem you got it through email phishing or visiting a hacked or a sketchy website. How did it spread so quickly ? As you most likely know by now, millions of computers were infected in a few short days and those most affected by this are on corporate, Government and University networks. It spreads on these networks by using a windows flaw that goes from machine to machine using Microsoft’s SMB feature . Here’s a short list of victims from GITHUB NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals) Nissan (uk) http://www.chroniclelive.co.uk/news/north-east-news/cyber-attack-nhs-latest-news-13029913 Telefonica (spain) ( https://twitter.com/SkyNews/status/863044193727389696 ) power firm Iberdrola and Gas Natural ( spain ) FedEx (us) ( https://twitter.com/jeancreed1/status/863089728253505539 ) University of Waterloo ( us ) Russia interior ministry & Megafon (russia) https://twitter.com/dabazdyrev/status/863034199460261890/photo/1 VTB (russian bank) https://twitter.com/vassgatov/status/863175506790952962 Russian Railroads (RZD) https://twitter.com/vassgatov/status/863175723846176768 Portugal Telecom ???????? – Sberbank Russia ( russia ) Shaheen Airlines (india, claimed on twitter) Train station in frankfurt ( germany ) Neustadt station ( germany ) the entire network of German Rail seems to be affected ( @farbenstau ) in China secondary schools and universities had been affected ( source ) A Library in Oman ( @99arwan1 ) China Yanshui County Public Security Bureau ( https://twitter.com/95cnsec/status/863292545278685184 ) Schools/Education (France) https://twitter.com/Damien_Bancal/status/863305670568837120 A mall in singapore https://twitter.com/nkl0x55/status/863340271391580 ATMs in china https://twitter.com/95cnsec/status/863382193615159 Renault STC telecom Norwegian soccer team ticket sales Is my website spreading this malware ? I can only say that any DOSarrest customers using our advanced WAF are not spreading this Malware as we won’t allow this type of malicious traffic to get to your server. Is it still spreading ? No, good news ! This thing had a kill switch built into its code, so if any machine can access this site www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com it won’t spread from that machine. I’m infected, What should I do ? We recommend that you wipe your machine clean and restore from back-ups….of course everyone has backups, Right ? Need more info… Try Github.com Microsoft to get the free patch if you need it. Source: https://www.dosarrest.com/ddos-blog/wannacry-faq/