The website of South Korea’s Ministry of Foreign Affairs has come under several cyberattacks originating from China but little damage has been reported so far, the ministry said Tuesday. “Several on-and-off DDoS attack attempts originating from China have taken place on websites including that of the Ministry of Foreign Affairs,” ministry spokesman Cho June-hyuck said in a press briefing. Defensive measures were immediately taken against the cyberattacks and no damage has been sustained, he said. The latest hacking attempts came as bilateral tensions remain high over the deployment of a US missile defense system in South Korea. Since the attempts, the foreign ministry has launched a special response team and distributed a response manual among the South Korean diplomatic missions in China, the spokesman noted. The spokesman did not elaborate on exactly who is behind the DDoS, or distributed denial of service, attacks, but they are the latest in a recent series of Chinese retaliations on South Korean industries and entities. A month earlier, the Chinese-language website of South Korean retail giant Lotte as well as its duty-free branch’s Chinese and Japanese-language websites sustained similar DDoS assaults, incurring heavy revenue losses. The attacks came as China stepped up its retaliatory actions over Seoul’s on-going deployment of the US missile interception system, Terminal High Altitude Area Defense. China vehemently protests the deployment which it said would compromise its security interests. “Our government pays attention to the Chinese government’s (past) expression of its consistent stance that it opposes any kind of cyberattack,” the ministry spokesman noted. “The government is expecting that (China) will continuously take responsible steps in accordance with the stance.” South Korea has also recently lodged a protest with the Chinese government after South Korean national flags were found destroyed in China, Cho said. “A national flag is a symbol of a nation’s dignity and the government takes very seriously the cases of destroyed Taegeukgi that took place in certain Chinese areas,” he said. “The government has officially lodged complaints with China on many occasions and demanded China take steps to address them immediately.” “In any case, the people-to-people exchange which is the foundation of the bilateral relationship should come under a man-made obstacle,” the spokesman said, adding that the South Korean government is trying to proactively react to China’s unjust measures in order to minimize any impact on South Korean companies. Referring to a media report alleging North Korean involvement in hacking attempts at a Poland bank and other international financial institutions, Cho also said that North Korea is likely to be using illegal cyber activities for a source of foreign currency earnings. “Given the international community’s concerns over the possibility that illegal income could be used for the development of weapons of mass destruction, North Korean cyber threats are emerging as new international threats along with its nuclear, missile and WMD threats.” (Yonhap) Source: http://www.koreaherald.com/view.php?ud=20170328000862
Follow this link:
Korean foreign ministry gets several DDoS attacks from China


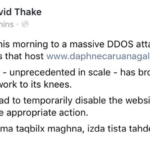 The servers hosting Daphne Caruana Galizia’s personal blog have suffered a DDoS attack. A DDos (denial of service) attack occurs when many systems flood the bandwidth of a targeted system, in an attempt to make the online service unavailable. Mrs Caruana Galizia does not yet know who is behind the attack, but did say it is highly likely to be a person of Maltese nationality.. Prior to the DDoS attack on the servers, she said, a fake Gmail account was setup – similar to her personal email address. The person who created the account, then emailed two persons working for the company who handle software support for the website, and tried to acquire information required to hack the site through them. This, however, did not work and the software support personnel realised that it was not Mrs Caruana Galizia’s email address, and also the use of broken English in the email. This, she said, is what led her to believe that the person behind the attack is Maltese. The police were contacted aftewr the DDOS attack occurred later, and an investigation is ongoing. The fake Gmail address used a proxy server, and thus far no culprit has been identified, she said. She explained that aside from the crime involving the DDoS attack, impersonation is also a crime. Vanilla Communications, a server hosting company owned by David Thake, hosts Daphne Caruana Galizia’s personal blog – a service that she pays for each month, she said. In a Facebook post, Mr Thake said that the servers hosting her website suffered a DDoS attack which he called “unprecedented in scale.” Mr Thake, in his post, said the attack brought the network to its knees. Source: http://www.independent.com.mt/articles/2017-03-21/local-news/Servers-hosting-Daphne-Caruana-Galizia-s-website-suffer-unprecedented-DDOS-attack-6736171884
The servers hosting Daphne Caruana Galizia’s personal blog have suffered a DDoS attack. A DDos (denial of service) attack occurs when many systems flood the bandwidth of a targeted system, in an attempt to make the online service unavailable. Mrs Caruana Galizia does not yet know who is behind the attack, but did say it is highly likely to be a person of Maltese nationality.. Prior to the DDoS attack on the servers, she said, a fake Gmail account was setup – similar to her personal email address. The person who created the account, then emailed two persons working for the company who handle software support for the website, and tried to acquire information required to hack the site through them. This, however, did not work and the software support personnel realised that it was not Mrs Caruana Galizia’s email address, and also the use of broken English in the email. This, she said, is what led her to believe that the person behind the attack is Maltese. The police were contacted aftewr the DDOS attack occurred later, and an investigation is ongoing. The fake Gmail address used a proxy server, and thus far no culprit has been identified, she said. She explained that aside from the crime involving the DDoS attack, impersonation is also a crime. Vanilla Communications, a server hosting company owned by David Thake, hosts Daphne Caruana Galizia’s personal blog – a service that she pays for each month, she said. In a Facebook post, Mr Thake said that the servers hosting her website suffered a DDoS attack which he called “unprecedented in scale.” Mr Thake, in his post, said the attack brought the network to its knees. Source: http://www.independent.com.mt/articles/2017-03-21/local-news/Servers-hosting-Daphne-Caruana-Galizia-s-website-suffer-unprecedented-DDOS-attack-6736171884