No wonder the Pentagon has announced it’s working on a plan to fund tools and researchers to help organizations defend themselves against the pervasive threat of cyber assaults known as distributed denial-of-service (DDoS) attacks. In recent days, the agency said it’s looking to fund researchers who can come up with tools as part of a program starting next April that would, among other things, help organizations recover from DDoS attacks in a maximum of 10 seconds. And the acknowledgement of that hunt for researchers for the program, called Extreme DDoS Defense, arguably comes not a moment too soon. A few new industry reports are out that show the number of DDoS attacks is trending upward, even hitting new highs. Their provenance and targets take many forms – from organized, malicious hackers targeting sophisticated organizations to more isolated incidents where, experts say, the intent is to just find a weakness somewhere, anywhere. But the result is a kind of cyber blitz that’s growing in number and aggressiveness. New York Magazine was among those organizations recently hit by a DDoS attack, and at a critical moment. After publishing the blockbuster results of an interview with 35 women who’ve accused Bill Cosby of sexually assaulting them, the magazine’s website was knocked offline by what appeared to be a DDoS attack. Attacks like those, said Incapsula co-founder Marc Gaffan, are not only on the rise but “have essentially been going up for the last two years, quarter over quarter.” His company is a cloud-based application delivery service. According to another cloud services provider, Akamai Technologies, DDoS attacks were up 132% in the second quarter compared to the same period in 2014. During the period between April and June this year, Akamai’s research also found 12 attacks it described as “mega attacks” – which peaked at more than 100 gigabits per second and 50 million packets per second. What’s more, the company said, few organizations are able to mount a strong enough defense to keep attacks like that at bay. “The threat posed by distributed denial of service (DDoS) and web application attacks continues to grow each quarter,” said John Summers, vice president of Akamai’s cloud security business unit. “Malicious actors are continually changing the game by switching tactics, seeking out new vulnerabilities and even bringing back old techniques that were considered outdated.” Once upon a time, Gaffan said, the attacks were largely the work of hackers looking to make a name for themselves, to make some larger point or to go after a controversial target to inflict some degree of discomfort. “They’re also about extortion and ransom,” Gaffan said. “They can be used to stoke competitive feuds, as well as a diversion for a larger attack. When it comes to extortion, attackers are looking online for businesses who’d suffer significantly if their website is down. Most companies don’t pay the ransom. “Often, we also see ransom numbers so small, they try to make it low enough that it’s a no-brainer for organizations to pay. Companies also hire DDoS gangs to take competitors down. There was one organization that came to us and said, ‘We were attacked.’ Two minutes later, a competitor put on Twitter that they were going out of business, and that’s why their site was down.” Such attacks continue to be a costly problem for the organizations that end up as targets. The Q2 2015 Global DDoS Threat Landscape from Incapsula showed, of network layer DDoS attacks, the longest during the quarter lasted 64 days. A little more than 20% of all attacks lasted over five days. The report based its data on 1,572 network layer and 2,714 application layer DDoS attacks on websites using Incapsula services from March 1st through May 7th. According to the organization’s DDoS Impact Survey, an attack on average costs a business $40,000 per hour. Implications include the loss of consumer trust, data theft, intellectual property loss, and more, according to the report. The report went on to note the longest application layer attack it found lasted for eight straight days. The average duration stretched for just over two and a half hours. And in the second quarter, almost 15% of all application layer DDoS traffic came from China, followed by Vietnam, the U.S., Brazil and Thailand. “What is most disconcerting is that many of these smaller assaults are launched from botnets-for-hire for just tens of dollars a month,” the organization’s threat landscape report reads. “This disproportion between attack cost and damage potential is the driving force behind DDoS intrusions for extortion and vandalism purposes.” Meanwhile, Arbor Networks Inc., a provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, found similar results. Its just-released Q2 2015 global DDoS attack data shows growth in the average size of attacks, with 21 percent of attacks during the quarter topping 1 gigabit per second. “One thing we see a lot of is just probing, just hitting the network as hard as they can to see where it will fall down,” said Gary Sockrider, principal security technologist at Arbor. “Another is where this is used for extortion. Where the business model is ok, now we’ve done this – pay us money.” Sockrider continued, “The lesson to take is this isn’t just a service provider problem. It’s no longer sufficient to leave it to deal with upstream. It’s everybody’s problem. You have to understand that threat, that you are a potential target, and bake that into your business resiliency planning.” Source: http://bgr.com/2015/08/31/ddos-attacks-report-2015-trends/
View post:
DDoS attacks are getting much more powerful and the Pentagon is scrambling for solutions


 Internet users Wednesday night protested the plans for a single gateway by attacking and bringing down the main websites of the prime minister, the Defence Ministry and the Ministry of Information and Communication Technology. Communications experts said “denial of service” attacks flooded the three sites, effectively making them impossible to access. The sites began to recover early Wednesday. The three sites went offline at about 10pm Wednesday, after netizens warned they intended to attack, and the government said such attacks would be treated as violations of the Computer Crime Act. The ICT deputy permanent secretary, Somsak Khaosuwan, claimed his ministry’s site did not crash because of an attack, but because it was overloaded by visitors monitoring the planned attack. Sites affected as of early Wednesday were the main government information website thaigov.go.th, the ICT ministry’s site at mict.go.th and the defence ministry’s website, mod.go.th. By early Wednesday, however, only the MICT site remained inaccessible, possibly because authorities had actually taken it offline. Warnings on Wednesday afternoon from credible sources in the Thai hacking community said they planned to attack government websites to protest the recent disclosure of government plans to reduce internet access to a single gateway, controlled by CAT Telecom Co. It appeared that the government site takedowns were by internet users, who answered calls on social media to go on online and continuously click refresh, causing overloads on the three targeted sites. The simultaneous denial-of-service attack works like normal attacks by over-exceeding a website’s capacity to handle internet traffic. But whereas normal attacks are carried out by a program or bot, Wednesday night’s protest was carried out by thousands of online users. After the secret plan was accidentally disclosed by a government press release, authorities sent out Deputy Prime Minister Prajin Junthong to try to spin the plan. He said that the single gateway initiative was only a proposition and that no “firm decisions have been made.” Critics of the plan idea contend it will take away freedom of information, with some even comparing it to the tightened grip of a communist country. A change.org petition opposing the single gateway initiative passed 100,000 signatures as of Wednesday. Source: http://www.bangkokpost.com/news/security/714432/single-gateway-protest-halts-government-websites
Internet users Wednesday night protested the plans for a single gateway by attacking and bringing down the main websites of the prime minister, the Defence Ministry and the Ministry of Information and Communication Technology. Communications experts said “denial of service” attacks flooded the three sites, effectively making them impossible to access. The sites began to recover early Wednesday. The three sites went offline at about 10pm Wednesday, after netizens warned they intended to attack, and the government said such attacks would be treated as violations of the Computer Crime Act. The ICT deputy permanent secretary, Somsak Khaosuwan, claimed his ministry’s site did not crash because of an attack, but because it was overloaded by visitors monitoring the planned attack. Sites affected as of early Wednesday were the main government information website thaigov.go.th, the ICT ministry’s site at mict.go.th and the defence ministry’s website, mod.go.th. By early Wednesday, however, only the MICT site remained inaccessible, possibly because authorities had actually taken it offline. Warnings on Wednesday afternoon from credible sources in the Thai hacking community said they planned to attack government websites to protest the recent disclosure of government plans to reduce internet access to a single gateway, controlled by CAT Telecom Co. It appeared that the government site takedowns were by internet users, who answered calls on social media to go on online and continuously click refresh, causing overloads on the three targeted sites. The simultaneous denial-of-service attack works like normal attacks by over-exceeding a website’s capacity to handle internet traffic. But whereas normal attacks are carried out by a program or bot, Wednesday night’s protest was carried out by thousands of online users. After the secret plan was accidentally disclosed by a government press release, authorities sent out Deputy Prime Minister Prajin Junthong to try to spin the plan. He said that the single gateway initiative was only a proposition and that no “firm decisions have been made.” Critics of the plan idea contend it will take away freedom of information, with some even comparing it to the tightened grip of a communist country. A change.org petition opposing the single gateway initiative passed 100,000 signatures as of Wednesday. Source: http://www.bangkokpost.com/news/security/714432/single-gateway-protest-halts-government-websites 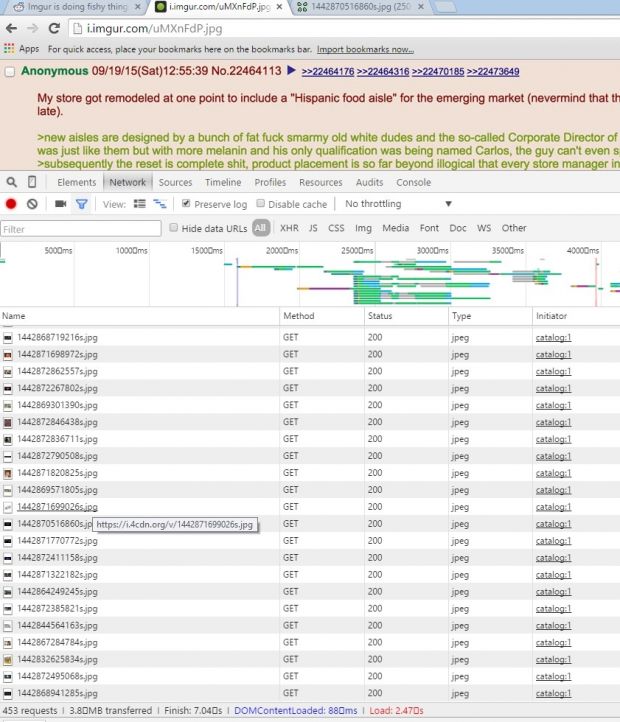
 A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml
A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml