The media and Latin American journalists are starting to experience firsthand what until recently seemed to be the exclusive concern of US, European or Asian media outlets: cyberattacks.? This type of online criminal activity, known as Distributed Denial of Service (DDoS), is the other side of technological advances that aim to maximize flow of information online.? Cybercrime legislation is backward and broken in Latin America, where the lack of a culture of information security or economic resources of journalists and media outlets ensures that attacks are successful.? One of the most recent cases occurred in Mexico, where minutes after publishing an investigation about the alleged responsibility of federal police in extrajudicial executions of several young people in Apatzingan, a town in the state of Michoacan, the Aristegui Noticias site was out of services for hours, a victim of a DDoS attack.? The Knight Center for Journalism in the Americas consulted Robert Guerra, an expert on cyber security and Internet freedom, and Luis Horacio Najera, a Mexican journalist and expert in the field, on the consequences of these attacks for media companies.? “The main consequence of a cyber attack in the context of Latin America is the reduction of critical spaces that encourage debate or the exposure of misconduct and abuse of power, like corruption,” Guerra said. Guerra, founder of Privaterra, an organization based in Canada that advises private companies and NGOs on data privacy, believes that “any attack, whether cyber or physical, deteriorates freedom of expression and of the press in the country where it occurs.” In the context of countries like Mexico, where media workers are victims of assassinations, kidnappings and threats, this “silent war” on the Internet is presented as a new alarm when speaking about freedom of expression and of the press. Momentary “blackouts” of online media affect the flow of information, the legitimacy of the company and its journalists, and also cause adverse economics effects for the media companies which base their income in online advertising. “The attacks almost always occur as a result of some publication, that is to say they are more reactive than proactive,” Guerra said of the Latin American case. “The freedom of the press is vulnerable not only when a journalist is killed or a broadcaster is exploited.” In fact, in the 2014 Annual Report of the Special Rapporteur for Freedom of Expression of the Inter-American Commission on Human Rights (CIDH), at least four cases of these attacks on media in Mexico were reported. “With the changes in technology and ways of doing journalism, cyber attacks will become more frequent because they attack the legitimacy of the journalist, and also affect the publication of news. Therefore, all attacks and threats should be condemned with the same intensity,” Guerra added. In addition to clear legislation, the region also lacks information on how and where these attacks occur, as well as statistics on their targets and consequences. In 2000, one of the companies specializing in digital security solutions, Arbor Networks, joined Google Ideas (an Internet research and conflict solution implementation think tank) to create a map that tracks digital attacks happening around the world, in real time. The aim was to create a tool for identifying these anonymous attacks: What is the origin of the attack, its target, and the duration and type of attack? It also aimed to analyze trends. Looking at the map, you can see that the peak of the cyber attacks in Latin America happened in December 2014. “It’s very interesting to see that most of the attacks are concentrated in a few countries in the region and that they are the result of specific moments in those countries,” Guerra said. “In the case of Guatemala, a reason for the attacks may be that at that time people were discussing the results of the International Commission Against Impunity in Guatemala. In the case of Peru, the second round of December 2014 regional elections may have influenced events.” What is a DDoS attack? At the technical level, a DDoS attack occurs when millions of simultaneous requests are sent to a single server in order to make it collapse. It is a targeted, deliberate action using hundreds of connected computers to make a simultaneous attack.? In an interview with the Knight Center, Hector Jara, founder and director of Enfinity, a Panamanian cybersecurity and information safety management company, explained the concept with an analogy. “Imagine a highway where a few cars circulating at high speeds and the traffic is fluid. As you add more and more cars, the driving pace slows and traffic is less fluid. If we continue to add cars, you will reach a point where the highway is saturated and cannot meet the demand, and the cars will be stopped. The same thing happens with connections to a website. The number of connections that it can respond to is limited, and if it makes more and more connection, at some point it will be saturated. The more capacity the organization has, this is more difficult to achieve – we think of Google Facebook, among others – but the limit always exists.” Jara also explained how criminal organizations use other types of attacks – for example phishing – through which they infect computers of ordinary users. “These infected computers are known as zombies , and can be controlled and used by these organizations to launch other attacks, such as DDoS. In fact these organizations assemble networks of zombie computers (known as botnets ) that they then ‘rent’ for non-sanctioned purposes”. The cybersecurity expert said that in addition to political purposes and censorship attacks, other attacks are related to digital protest. For example, the term Hacktivism is a new form of protest increasingly being used. One of the latest examples of the use of technology as a means of social protest was during the removal of former President Fernando Lugo of Paraguay when attacks on public bodies were made and one of them closed access to the official website of the Presidency. Asked about possible actions against these attacks, Jara explained that “while we can design a communications architecture in a way that can protect against these attacks – for example there are technological tools such as Web Application Firewalls and services such as CloudFlare , which can mitigate the impact and in some cases completely limit it – by the nature of the attack, if those interested in launching the attack had enough resources and time, it is likely that the would force a site out of operation.” While in the United States DDoS attacks are considered crimes and are punishable under the penal code, this has not been shown to combat the situation. The question is what can legislation achieve regarding this issue. Experts agree that international cooperation is key to fighting cybercrime. In 2014, Mexico hosted the “Workshop on legislation on cybercrime in Latin America”, organized to support Latin American countries in developing legislation on cyber crime, in accordance with international standards proposed in the “Budapest Convention “. During the meeting, possible reforms to criminal law of the participating countries and constitutional reforms in telecommunications were debated. While Argentina, Chile, Colombia, Costa Rica, Mexico, Paraguay and Peru have expressed their interest in joining the treaty, Dominican Republic and Panama have already completed this process. “Most regional legislation concerning information security have been poorly, and in many cases have been motivated by local public security crisis,” said Guerra of Privaterra. “So, from the start, these are deficient laws that in many cases secretly seek to impact civil society through censorship and criminalization of social networking activity.” Guerra also said it is not possible to speak of general solutions in Latin America, but that “each region has its own dynamics, and accordingly, legislation should create or strengthen legal counter methods to give tools for protection to civil society. These tools should be autonomous and independent of government.” Meanwhile, Jara noted that while regulations should establish a legal framework that protects personal information and data, in the case of journalists, these professionals should take measures to protect such data. “Because of the work, they may be a target of criminal organizations and sometimes governments. If they also have blogs or personal pages, they should ensure the safety of them, as a vulnerable site also becomes the focus of attack, ” Jara said. Source: https://knightcenter.utexas.edu/blog/00-16118-ddos-attacks-are-growing-digital-threat-freedom-expression-latin-america
Read More:
DDoS attacks are a growing digital threat to freedom of expression in Latin America


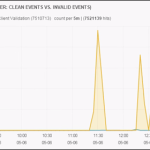 In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/
In 2012, Anonymous introduced HOIC (high orbit ion cannon) as a replacement to LOIC (low orbit ion cannon). Unlike its predecessors, that were built upon C#, and later java. This new DDoS player was built upon the unsuspecting language of Visual Basic. Taught in high school classrooms, Visual Basic was largely seen by the programming community as a means for kids and young programmers to get their feet wet in the experience of programming. Considered by many programmers as grossly inefficient and a memory hog; Visual Basic was an unsuspected carrier for what would become one of the most powerful means of DDoS. One of the popular notions of HOIC has been its ability to randomize variables such as: user agent, referrer and URI, during an attack. In the same manner, an attack tool known as HULK (developed by: Barry Shteiman, 2012), written in Python, was developed in recent history. Within a controlled environment we tested these DDoS tools to judge their effectiveness and total output. In controlled trials the DDoS output of LOIC (Visual Basic on Windows) outperforms the DDoS output HULK (Python on Linux) by +40%. Figure 1: HOIC Test in Stable Windows Environment Figure 2: HULK Test While many of us in the Internet security industry ridicule and downplay the “kiddie hacker;” it is clear that it sometimes only takes a kiddie to build an empire. Lessons in open source economics teach us that in an open access environment, it takes only a small few to bring about radical change and innovation. Today HOIC has become one of the primary tools of groups such as anonymous. From this lesson, we can expect that challenges and sudden changes, will not come from those paid hundreds of thousands a year; but from those small few kiddies, whom are politically motivated and are paid nothing. Source: http://www.dosarrest.com/ddos-blog/how-visual-basic-broke-modern-python-welcome-to-the-world-of-high-orbit-ion-cannon/