Recent happenings at what was considered one of the more reliable and trustworthy offshore online poker rooms, Carbon Poker, is simply furthering the case for regulated online poker in the United States. Anyone calling for a ban of online gambling in the U.S. should pay particular attention to what has taken place at Carbon Poker over the past couple weeks, as these are the types of online poker operators that will survive a federal online gambling ban. If Sheldon Adelson gets his way, regulated sites like WSOP.com would be forced to shut down and sites like Carbon would continue to fill the void. In the past couple weeks the site experienced several significant problems that have left many players concerned about the safety of their accounts and their personal information, as well as with the overall integrity of the games at the site. Server crash leads to data breach The first issue occurred during one of the biggest tournament days in Carbon Poker’s history. On November 23, the Main Event of the Carbon Poker Online Poker Series, along with dozens of other tournaments at the site, were running when the Carbon Poker servers’ crashed, bringing everything to a screeching halt. Site-wide server crashes are rare, but they do happen. Unfortunately for Carbon, this was not a typical server crash, which is bad enough in its own right. According to multiple reports by poker players on social media sites and on the poker forums, the server crash not only caused widespread disconnections, but also caused hole cards to change mid-hand for players still able to log in and play, and even more worrisome, customers were inexplicably able to gain access to other players’ accounts when they tried to log back on to the site. Players reported that this first of its kind (to my knowledge) technical glitch, not only allowed them access to other Carbon Poker’s players accounts, but they were capable of gambling with those funds (including players that were active on the site when the servers crashed), as well as being able to see the accountholders sensitive personal information. A DDoS superuser? As concerning as the server crash and data breach were, things got even worse this weekend when, after several days of unexplained and consistent disconnect issues, widespread rumors began to take hold that targeted DDoS attacks were behind the ongoing technical issues, and were being used to win pots. Following pages of frustration over the ongoing disconnects, the DDoS rumors took hold with an out of left field (something that is not uncommon on 2+2) accusation: I found the hacker that is disconnecting the server. He builds big pots and once he min-raises he crashes the server and scoops the pot. His username is L4ss3m4jj4n. He did it to me a few times and took quite a bit from me at PLO. I then followed him and watched him do it to others. I emailed support so lets see what happens.” And from there it escalated: “Guys, I would normally say this is just somebody coming up with a wild conspiracy theory, but this is serious, everybody should open up this table, it’s table 24 in the $215/125k, something is super super fishy about the way L4ss3m4jj4n is playing, every disconnect has benefited him so far, it seems too obvious if you watch it for a few of the disconnects.” “second time i’m witnessing him betting in big pot and a disconnect taking place.” “Kh8s9d7h board he checks, phat1cat bets 1888 into 3750, l4ss3m4jj4n minraises to 3776 and disconnect.” In addition to the forum gossip, the potential DDoS superuser was also discussed/mentioned on social media by well-known poker players and poker commentators. Click here and also here. As the story began to unfold, over 100 players started monitoring this person’s play as it was being live-streamed on Twitch.com, and at the same time were furiously contacting Carbon Poker customer support en masse to have something done about the situation. You can read a good summary (for those that can’t handle 200 pages of 2+2 posts) of what took place at Carbon Poker/Merge Gaming here. It should be stated, that whether this was a concerted DDOS attack by some nefarious player(s), or if the sites are simply experiencing ongoing technical issues is unclear. What is clear is that unregulated sites make it much harder for players to be treated fairly and properly compensated when these things occur. It also shows the inability of players on unregulated sites to take their grievances to a regulatory body that oversees the site. The important takeaway is, if these types of issues are occurring at Carbon Poker, considered one of the top unregulated online poker sites still serving the U.S. market, what is happening at the other, more suspect, operators? Source: http://www.pokerupdate.com/news/networks-and-rooms/12083-carbon-poker-crash-and-possible-ddos-attacks-highlight-need-for-legalization/
See the original post:
Carbon Poker Crash and Possible DDoS Attacks Highlight Need for Legalization
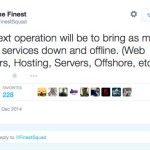 The Finest Squad is set out to bring cyber criminals to justice around the world; their main plan at the moment is to bring DDoS services down. When you visit the @FinestSquad Twitter account they are going all out with their tweets, you can clearly see they want the world to see they brought the Lizard Squad crew to their knees with its pinned tweet. Lizard Squad has been removed from twitter thanks to the Finest Squad, and then they say in their tweet, “Your welcome fellow gamers. We will make sure their IRC stays offline.” The next few steps for the Finest Squad include taking down / offline as many DDoS services, these include hosting, offshore, hosting, web booters and more. They have also announced on its Twitter account they are setting up a new YouTube channel, a news bulletin and a community forum – these are being developed right now so stay tuned. They also want to stack up its team; they basically want more of the finest. They do stress no illegal activities allowed, are you interested. This new role comes after they hired a professional full-time web designer/developer and web site security specialist. Looks like the Finest Squad is here to help all the gamers out there, PlayStation and Xbox gamers will be thrilled to bits Lizard Squad has had the Finest treatment. They do not like these kids harassing people and that is why they are there to bring justice. So far the Finest Squad website lists the LizardSquad member Obnoxious being arrested, @LizardPatrol, @LizardSquad and many more being removed from Twitter. All these wrong doings are being hunted, such as the EZTV proxy site being shutdown – read more here. Are you happy with what the Finest Squad have done so far? Source: http://www.onlinesocialmedia.net/20141217/finest-squad-to-bring-ddos-services-down/
The Finest Squad is set out to bring cyber criminals to justice around the world; their main plan at the moment is to bring DDoS services down. When you visit the @FinestSquad Twitter account they are going all out with their tweets, you can clearly see they want the world to see they brought the Lizard Squad crew to their knees with its pinned tweet. Lizard Squad has been removed from twitter thanks to the Finest Squad, and then they say in their tweet, “Your welcome fellow gamers. We will make sure their IRC stays offline.” The next few steps for the Finest Squad include taking down / offline as many DDoS services, these include hosting, offshore, hosting, web booters and more. They have also announced on its Twitter account they are setting up a new YouTube channel, a news bulletin and a community forum – these are being developed right now so stay tuned. They also want to stack up its team; they basically want more of the finest. They do stress no illegal activities allowed, are you interested. This new role comes after they hired a professional full-time web designer/developer and web site security specialist. Looks like the Finest Squad is here to help all the gamers out there, PlayStation and Xbox gamers will be thrilled to bits Lizard Squad has had the Finest treatment. They do not like these kids harassing people and that is why they are there to bring justice. So far the Finest Squad website lists the LizardSquad member Obnoxious being arrested, @LizardPatrol, @LizardSquad and many more being removed from Twitter. All these wrong doings are being hunted, such as the EZTV proxy site being shutdown – read more here. Are you happy with what the Finest Squad have done so far? Source: http://www.onlinesocialmedia.net/20141217/finest-squad-to-bring-ddos-services-down/ 

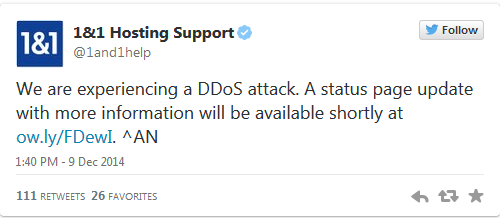
 UK hosting company 1&1 went titsup late on Tuesday night and struggled to recover this morning, after claiming it had been the victim of a Distributed-Denial-of-Service (DDoS) attack. The website collapsed shortly before 10pm yesterday, and it has taken 1&1 a full 12 hours to get its service back up and running. Readers who told the Reg about the outage said that the service had been flaky for several hours before it keeled over. 1&1 blamed the downtime on a DDoS attack in a tweet. However, although the website appeared to be returning to normal, 1&1 had yet to update its customers about the status of its system at time of writing. Customers were still griping about the mysterious outage this morning. Indeed, 1&1 was tight-lipped about the cause of the service disruption on its status page, which made no mention of a system security breach. Last month, Fasthosts blamed a five-hour outage it had suffered on a DDoS attack. Source: http://www.theregister.co.uk/2014/12/10/1_and_1_hosting_firm_claims_ddos_attack_downs_website/
UK hosting company 1&1 went titsup late on Tuesday night and struggled to recover this morning, after claiming it had been the victim of a Distributed-Denial-of-Service (DDoS) attack. The website collapsed shortly before 10pm yesterday, and it has taken 1&1 a full 12 hours to get its service back up and running. Readers who told the Reg about the outage said that the service had been flaky for several hours before it keeled over. 1&1 blamed the downtime on a DDoS attack in a tweet. However, although the website appeared to be returning to normal, 1&1 had yet to update its customers about the status of its system at time of writing. Customers were still griping about the mysterious outage this morning. Indeed, 1&1 was tight-lipped about the cause of the service disruption on its status page, which made no mention of a system security breach. Last month, Fasthosts blamed a five-hour outage it had suffered on a DDoS attack. Source: http://www.theregister.co.uk/2014/12/10/1_and_1_hosting_firm_claims_ddos_attack_downs_website/