The “total war” that Anonymous declared earlier this month against Donald Trump has quickly devolved into a civil war among hackers fighting within the group and pro-Trump supporters who are trolling them within their chat rooms. In early March, hackers affiliated with Anonymous tried to reboot their Operation Trump campaign by calling for everyone to take down Trump’s websites in a coordinated effort on April 1. Almost immediately, the initiative was criticized by people within Anonymous as irresponsible and “cringeworthy,” but a dedicated group apparently moved on with the plan. It’s April 1: Many of the GOP frontrunner’s sites are still standing, there are now two competing OpTrump chat rooms with totally different missions, and one of them has been flooded with pro-Trump supporters and others leaving trolling comments like “Hitler did nothing wrong.” In short: The so-called war seems to be a complete disaster. ‘A mess is happening’ It’s unclear when the split between Anonymous factions occurred, but it seems to have happened sometime after a hacker named Beemsee, who has been leading the original OpTrump effort, released a new statement claiming that attacking Trump’s websites was all a ruse for publicity around April Fools’ Day. “There is no DDoS,” Beemsee and two other hackers wrote, using the acronym for a distributed denial-of-service attack, a tactic used to overload a website. “It’s only purpose was to gain attention, which this Operation needs. … the point of this Operation is not to attack Donald Trump. Instead, it is going to try to give citizens some insight.” Beemsee and their cohorts say in their statement that people should try and capture “the darker nature of Trump’s supporters” and post it on social media sites with hashtags like #OpTrump and #Trump2016. But a hacker called AnonymousLoyalist disagreed. In a competing statement, the hacker wrote that they moved to a “far more organized channel, which has already seen unsurprisingly large amounts of success.” That channel is #OpTrump2016, but it was unclear exactly what that success boiled down to. When Tech Insider viewed the #OpTrump2016 chat room on Friday, it was an unorganized mess. Most Anonymous chat rooms are moderated in some way, and people usually get kicked out for spamming or posting nonsense. But it appeared to be flooded with trolls intent on calling them children, “social justice warriors,” and, more often than not, homophobic slurs. “A mess is happening,” wrote one user in #OpTrump, expressing a shared frustration among others in Beemsee’s chat room. The ‘war’ goes on It was clear on Friday that at least some of Trump’s websites were indeed under cyberattack. The website CitizensForTrump.com is currently unreachable, and the site for Trump’s hotels brought up an error for a few seconds before pulling up a cached version powered by CloudFlare, a service that protects from attacks like this. Anonymous may be able to bring down some of Trump’s unprotected websites, but it will almost certainly come back online after a few hours or days. And many of his other sites are probably not at risk at all, since Tech Insider previously spoke with CloudFlare CEO Matthew Prince, and he wasn’t particularly worried. “DDoS attacks are not particularly sophisticated cyber attacks,” Prince said. “They are sort of the functional equivalent of a caveman with a club.” A representative for Trump did not immediately respond to a request for comment from Tech Insider, but spokeswoman Hope Hicks previously told Tech Insider: “The government and law-enforcement authorities are seeking the arrest of the people responsible for attempting to illegally hack Mr. Trump’s accounts and telephone information.” Depending on who you believe in Anonymous, the plan is a coordinated DDoS attack or a social-media shaming campaign against Trump’s supporters. But Beemsee left open the possibility of something else, perhaps an actual way to take over one of their targeted websites — which the hacker collective has been scanning for vulnerabilities since the beginning. “This is NOT the last time you hear of this operation,” Beemsee wrote. “We will be watching, and will act when the time is right.” Source: http://www.businessinsider.com/anonymous-war-donald-trump-fail-2016-4
Excerpt from:
The Anonymous ‘war’ on Donald Trump is a complete disaster


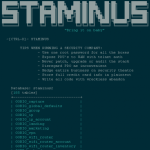 Staminus Communications Inc ., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data. Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday. “Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.” Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages. Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks. The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards. Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online. I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them. It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services. Source: https://krebsonsecurity.com/2016/03/hackers-target-anti-ddos-firm-staminus/
Staminus Communications Inc ., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data. Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday. “Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.” Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages. Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks. The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards. Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online. I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them. It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services. Source: https://krebsonsecurity.com/2016/03/hackers-target-anti-ddos-firm-staminus/