Last month’s arrest in Bosnia and Herzegovena of two individuals connected to the cyber-crime group DD4BC have been definitely linked to a series of DDoS extortion attacks over the past 18 months, many of which were targeted at online-gambling firms. PokerStars and Betfair are among the various companies to have been targeted by the extortionists, who typically sought modest and largely-anonymous payments made in Bitcoins in exchange for ceasing the attacks. The DD4BC group, an acronym for DDoS (Distributed Denial of Service attack) For BitCoins, is a loosely organized group of online hackers and thieves who have congregated in some of the Internet’s darker, more anonymous holes. The group’s widespread members share information and online weaponry in their attempts to extract payments from their targets. Failure to provide payoffs by the group’s targeted victims typically results in intermittent and ongoing DDoS attacks, designed to flood the victim’s servers with meaningless online traffic, making normal business impossible. The arrests of the two unidentified individuals was announced by Europol earlier this month, with one of the two individuals described as being a leader of the informal DD4BC group. These initial arrests were part of an international operation dubbed Operation Pleaides. According to the Netherlands-based Europol, which is the official intelligence agency of the European Union, “The action was initiated as part of a global law enforcement response against the criminal organisation. Key members of the organised network were identified in Bosnia and Herzegovina by the UK Metropolitan Police Cyber Crime Unit (MPCCU) which provided vital information to the investigation. Police authorities from Australia, France, Japan, Romania, the USA, Switzerland and INTERPOL supported the coordinated activities. “Operation Pleiades resulted in the arrest of a main target and one more suspect detained,” the Europol statement added. “Multiple property searches were carried out and an extensive amount of evidence was seized,” indicating that more arrests of DD4BC members are likely in the coming weeks and months. The actual “Operation Pleiades” action was initiated in Austria and included Europol’s European Cybercrime Centre (EC3) and the Joint Cybercrime Action Taskforce. The operation slowly unwound the ghostly online tracks of the extortionists by examining “blockchain” entries for Bitcoin transactions related to the DDoS threats, plus other data linked to the group’s activities. Bitcoin-based transactions are anonymous but not perfectly transparent, and can often be traced back to their originators using secondary means. The DD4BC attacks, which appear to have started in early 2014, have targeted several different business and government sectors. Victims range from online gambling firms to Bitcoin exchanges and mining groups, to online banking and payment processors. Even some government institutions have been targeted. Online-poker market leader PokerStars was confirmed as one the DD4BC extortion attempts in April 2015, amid information on the DD4BC attacks assembled by Arbor Networks, the security division of NetScout Systems, Inc. Massachusetts-based NetScout appears to have assisted international authorities in identifying the perpetrators behind the hundreds of DD4BC attacks. In addition to PokerStars, Betfair is almost certainly another of the DD4BC group’s victims. Betfair was also targeted last April in a DDoS attack strong enough to knock both its betting exchange and fixed-odds sportsbook offline. The attack on the “unnamed online casino” (likely Betfair) began in earnest on April 10th, following an initial probing attack launched the day before, along with a demand for payment. The information amassed by Arbor Networks also includes many of the threats e-mailed by DD4BC members to their intended victims. Here’s the e-mail that was sent to the “unnamed” casino company (likely Betfair), immediately following attacks against Stars and online payment processor NETeller: From: DD4BC Team [mailto:dd4bct@gmail.com] Sent: 10 April 2015 02:07 PM To Subject: Re: DDOS ATTACK! Hitting pokerstars.com at the moment. Good luck if you think you can stop what they can’t. But you still have time. On Thu, Apr 9, 2015 at 3:46 PM, DD4BC Team wrote: Hello, To introduce ourselves first: https://blogs.akamai.com/2014/12/dd4bc-anatomy-of-a-bitcoin-extortion-campaign.html http://bitcoinbountyhunter.com/bitalo.html http://cointelegraph.com/news/113499/notorious-hacker-group-involved-in-excoin-theft-owner-accusesccedk-of-withholding-info Or just google “DD4BC” and you will find more info. Recently, we were DDoS-ing Neteller. You probably know it already. So, it’s your turn! is going under attack unless you pay 20 Bitcoin. Pay to 18NeYaX6GCnibNkwyuGhGLuU2tYzbxvW7z Please note that it will not be easy to mitigate our attack, because our current UDP flood power is 400-500 Gbps, so don’t even bother. Right now we are running small demonstrative attack on your server. Don’t worry, it will stop in 1 hour. It’s just to prove that we are serious. We are aware that you probably don’t have 20 BTC at the moment, so we are giving you 48 hours to get it and pay us. We do not know your exact location, so it’s hard to recommend any Bitcoin exchanger, so use Google. Current price of 1 BTC is about 250 USD. IMPORTANT: You don’t even have to reply. Just pay 20 BTC to 18NeYaX6GCnibNkwyuGhGLuU2tYzbxvW7z – we will know it’s you and you will never hear from us again. We say it because for big companies it’s usually the problem as they don’t want that there is proof that they cooperated. If you need to contact us, feel free to use some free email service. But if you ignore us, and don’t pay within 48 hours, long term attack will start, price to stop will go to 50 BTC and will keep increasing for every hour of attack. ONE MORE TIME: It’s a one-time payment. Pay and you will not hear from us ever again! Variations on the same extortion letter were sent to several other victims; this sample was distinct with the specific mentions of PokerStars and NETeller. In addition to those two firms and the likely inclusion of Betfair, several other online-gambling companies are known to be targets of the group. Those companies include Nitrogen Sports, Malta-based NRR Entertainment Ltd. (including slottyvegas.com and betatcasino.com), Betbtc.com, Redbet.com and others. It is also likely that last July’s DDoS attacks against several New Jersey (U.S.) online sites were the work of DD4BC extortionists. Though those attacks are not referenced in the ASERT compilation, the July attacks are also outside the date range of most of the earlier attacks included in that report. When the New Jersey attacks occurred, NJ Division of Gaming Enforcement director David Rebuck stated this about the perpetrator: “He’s a known actor. He’s done this before.” While DD4BC seems likely to be peeled open by international invetigators, DDoS-based extortion attempts aren’t going to go away. The reason is that the tools needed to launch such attacks are too cheaply and commonly available to would-be cyber-attackers. As a result, the best defense remain vigilance, rapid response… and robust Internet connectivity. According to Wil van Gemert, Europol’s Deputy Director of Operations, “Law enforcement and its partners have to act now to ensure that the cyberspace affecting nearly every part of our daily life is secure against new threats posed by malicious groups. These groups employ aggressive measures to silence the victims with the threat of public exposure and reputation damage. Without enhanced reporting mechanisms law enforcement is missing vital means to protect companies and users from recurring cyber-attacks. Police actions such as Operation Pleiades highlight the importance of incident reporting and information sharing between law enforcement agencies and the targets of DDoS and extortion attacks.” Source: http://www.flushdraw.net/news/misc/two-arrested-in-ddos-attacks-linked-to-online-gambling-site-extortion/
Excerpt from:
Two Arrested in DDoS Attacks Linked to Online Gambling Site Extortion


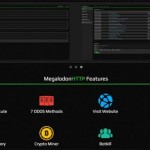 Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml
Hacker was arrested one month ago in Europol operation Norway’s law enforcement authorities have identified a previously arrested suspect as the author of the MegalodonHTTP malware, used for infecting computers and adding them to a botnet used for DDoS attacks. The yet unnamed suspect, known only by his online moniker of Bin4ry, was arrested in December 2015 , during the second stage of Operation Falling sTAR, launched in October 2015 against users of RATs (Remote Access Trojans). During this second phase of the operation, Europol authorities coordinated the arrests of 12 individuals in France, Norway and Romania. Five of the suspects were arrested in Norway. Damballa helped authorities track down MegalodonHTTP’s author A big part in arrest played US cyber-security vendor Damballa, who helped Europol break down the botnet’s activities, and then worked with Norwegian authorities to track down the malware’s author. “We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business,” said Loucif Kharouni, Senior Threat Researcher for Damaballa. Damballa’s team analyzed the MegalodonHTTP malware in late November 2015, as the malware was starting to become more prevalent on the Dark Web, being sold in two separate packages, one that cost $35, and the second that cost $100. Damballa: MegalodonHTTP is not an advanced malware The malware was sold both from Dark Web hacking forums, but also from the now defunct bina4ry.com domain, and came equipped with an automated installer and administration panel, so even skids (script kiddies) could use it, without possessing advanced technical in advance. According to Bin4ry’s description of MegalodonHTTP, the malware was capable of launching seven types of DDoS attacks, remote shells on infected machines, included Bitcoin mining features, but also had the option to kill antivirus processes. At the time of their analysis, Damaballa researchers said that despite being quite potent in terms of features, the malware was not the work of a skilled coder, worked only on Windows machines, and needed the .NET Framework installed, which narrowed the number of machines it could work from. MegalodonHTTP DDoS botnet administration panel Source: http://news.softpedia.com/news/author-of-megalodonhttp-ddos-malware-arrested-in-norway-498981.shtml