Recent happenings at what was considered one of the more reliable and trustworthy offshore online poker rooms, Carbon Poker, is simply furthering the case for regulated online poker in the United States. Anyone calling for a ban of online gambling in the U.S. should pay particular attention to what has taken place at Carbon Poker over the past couple weeks, as these are the types of online poker operators that will survive a federal online gambling ban. If Sheldon Adelson gets his way, regulated sites like WSOP.com would be forced to shut down and sites like Carbon would continue to fill the void. In the past couple weeks the site experienced several significant problems that have left many players concerned about the safety of their accounts and their personal information, as well as with the overall integrity of the games at the site. Server crash leads to data breach The first issue occurred during one of the biggest tournament days in Carbon Poker’s history. On November 23, the Main Event of the Carbon Poker Online Poker Series, along with dozens of other tournaments at the site, were running when the Carbon Poker servers’ crashed, bringing everything to a screeching halt. Site-wide server crashes are rare, but they do happen. Unfortunately for Carbon, this was not a typical server crash, which is bad enough in its own right. According to multiple reports by poker players on social media sites and on the poker forums, the server crash not only caused widespread disconnections, but also caused hole cards to change mid-hand for players still able to log in and play, and even more worrisome, customers were inexplicably able to gain access to other players’ accounts when they tried to log back on to the site. Players reported that this first of its kind (to my knowledge) technical glitch, not only allowed them access to other Carbon Poker’s players accounts, but they were capable of gambling with those funds (including players that were active on the site when the servers crashed), as well as being able to see the accountholders sensitive personal information. A DDoS superuser? As concerning as the server crash and data breach were, things got even worse this weekend when, after several days of unexplained and consistent disconnect issues, widespread rumors began to take hold that targeted DDoS attacks were behind the ongoing technical issues, and were being used to win pots. Following pages of frustration over the ongoing disconnects, the DDoS rumors took hold with an out of left field (something that is not uncommon on 2+2) accusation: I found the hacker that is disconnecting the server. He builds big pots and once he min-raises he crashes the server and scoops the pot. His username is L4ss3m4jj4n. He did it to me a few times and took quite a bit from me at PLO. I then followed him and watched him do it to others. I emailed support so lets see what happens.” And from there it escalated: “Guys, I would normally say this is just somebody coming up with a wild conspiracy theory, but this is serious, everybody should open up this table, it’s table 24 in the $215/125k, something is super super fishy about the way L4ss3m4jj4n is playing, every disconnect has benefited him so far, it seems too obvious if you watch it for a few of the disconnects.” “second time i’m witnessing him betting in big pot and a disconnect taking place.” “Kh8s9d7h board he checks, phat1cat bets 1888 into 3750, l4ss3m4jj4n minraises to 3776 and disconnect.” In addition to the forum gossip, the potential DDoS superuser was also discussed/mentioned on social media by well-known poker players and poker commentators. Click here and also here. As the story began to unfold, over 100 players started monitoring this person’s play as it was being live-streamed on Twitch.com, and at the same time were furiously contacting Carbon Poker customer support en masse to have something done about the situation. You can read a good summary (for those that can’t handle 200 pages of 2+2 posts) of what took place at Carbon Poker/Merge Gaming here. It should be stated, that whether this was a concerted DDOS attack by some nefarious player(s), or if the sites are simply experiencing ongoing technical issues is unclear. What is clear is that unregulated sites make it much harder for players to be treated fairly and properly compensated when these things occur. It also shows the inability of players on unregulated sites to take their grievances to a regulatory body that oversees the site. The important takeaway is, if these types of issues are occurring at Carbon Poker, considered one of the top unregulated online poker sites still serving the U.S. market, what is happening at the other, more suspect, operators? Source: http://www.pokerupdate.com/news/networks-and-rooms/12083-carbon-poker-crash-and-possible-ddos-attacks-highlight-need-for-legalization/
See the original post:
Carbon Poker Crash and Possible DDoS Attacks Highlight Need for Legalization


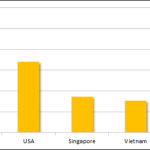 Majority of DDoS traffic in 2014 originated from India, says a new research from Symantec. Of the top 50 countries that witnessed the highest volume of originating DDoS traffic, India accounted for 26 percent of all DDoS traffic, followed by the USA with 17 percent, the research said. The results prove India has a high number of bot infected machines and a low adoption rate of filtering of spoofed packets, but may not imply that people behind the attacks are located in India because DDoS attacks are often orchestrated remotely. However, the study indicates that India is emerging as a hotbed to launch these attacks, potentially because of the low cyber security awareness, lack of adequate security practices and infrastructure, said Tarun Kaura, director, Technology Sales at Symantec India. The year 2014 saw an increase in the compromise of Linux servers, including those from cloud providers. These high bandwidth servers are then used as part of a botnet to perform DDoS attacks. The so-called “Booter” services can be hired for as little as INR 300 ($5 USD) to perform DDoS attacks for a few minutes against any target. Longer attacks can be bought for larger prices. They also offer monthly subscription services, often used by gamers to take down competitors. As the most attacked sector globally, the gaming industry experiences nearly 46 percent of attacks, followed by the software and media sectors While it’s not happening on a broad scale now, it’s likely we’ll see an increase in DDoS attacks originating from mobile and IoT devices in the future, Symantec said. DDoS attacks make an online service unavailable by overwhelming it with traffic from multiple sources. A Domain Name Server (DNS) amplification attack is a popular form of DDoS, which floods a publically available target system with DNS response traffic. Symantec’s research indicates that DNS amplification attacks have increased by 183 percent from January to August 2014. Motivations behind DDoS Attacks include hacking and financial blackmail with the threat of taking the business offline personal grudge. It also acts as a diversion technique to distract IT security response teams while a targeted attack is conducted. Source: http://www.infotechlead.com/2014/10/24/india-accounts-26-top-ddos-traffic-symantec-26196
Majority of DDoS traffic in 2014 originated from India, says a new research from Symantec. Of the top 50 countries that witnessed the highest volume of originating DDoS traffic, India accounted for 26 percent of all DDoS traffic, followed by the USA with 17 percent, the research said. The results prove India has a high number of bot infected machines and a low adoption rate of filtering of spoofed packets, but may not imply that people behind the attacks are located in India because DDoS attacks are often orchestrated remotely. However, the study indicates that India is emerging as a hotbed to launch these attacks, potentially because of the low cyber security awareness, lack of adequate security practices and infrastructure, said Tarun Kaura, director, Technology Sales at Symantec India. The year 2014 saw an increase in the compromise of Linux servers, including those from cloud providers. These high bandwidth servers are then used as part of a botnet to perform DDoS attacks. The so-called “Booter” services can be hired for as little as INR 300 ($5 USD) to perform DDoS attacks for a few minutes against any target. Longer attacks can be bought for larger prices. They also offer monthly subscription services, often used by gamers to take down competitors. As the most attacked sector globally, the gaming industry experiences nearly 46 percent of attacks, followed by the software and media sectors While it’s not happening on a broad scale now, it’s likely we’ll see an increase in DDoS attacks originating from mobile and IoT devices in the future, Symantec said. DDoS attacks make an online service unavailable by overwhelming it with traffic from multiple sources. A Domain Name Server (DNS) amplification attack is a popular form of DDoS, which floods a publically available target system with DNS response traffic. Symantec’s research indicates that DNS amplification attacks have increased by 183 percent from January to August 2014. Motivations behind DDoS Attacks include hacking and financial blackmail with the threat of taking the business offline personal grudge. It also acts as a diversion technique to distract IT security response teams while a targeted attack is conducted. Source: http://www.infotechlead.com/2014/10/24/india-accounts-26-top-ddos-traffic-symantec-26196