The education sector is the fastest growing segment in taking up distributed denial of service (DDoS) mitigation, according to DDoS protection services firm DOSarrest. The firm’s CTO Jag Bains told Computing that many companies -not just e-commerce firms – are deploying DDoS protection. “If their website goes down as a result of an attack, they can lose their SEO ranking or it could have an effect on their brand, there is a lot at stake aside from revenues,” he said. And despite there not being a particular industry that looks at DDoS protection as a must, DOSarrest’s general manager, Mark Teolis claimed that the education sector is one area which has grown significantly. “Our fastest growing segment in the last six months is the education sector believe it or not,” he said. Teolis explained that the firm was getting business from “schools from the UK, the US and international universities” but said he couldn’t identify a specific reason as to why the sector has shown a sudden interest. Bains believes that it may be as a result of educational institutes guarding themselves against their own students. “Students have easy access to DDoS tools, so they may want to try it against their own [school or university]. They could be motivated because they’re failing in something, and there are enough smart kids around to access tools – it is easy to Google them anyway,” he said. But Teolis said that the tools have been available on the internet for a long time, so questioned why there was a sudden surge in interest from educational institutes. Bains suggested that it could be because the school and university websites have become an integral part of the education system. “We’ve been talking about e-commerce and gaming [as being key industries for DDoS protection], but web presence itself is very important and schools and universities need to make their websites accessible. They need a website to give out grades, information and schedules – five years ago they weren’t really using the web page apart from explaining where the school is located,” he said. But while the education sector may be taking a keen interest, Teolis claims that there is not one segment that is “taking up 30 per cent of the market”. He said that “10 or 15 per cent of the market is as good as it gets”. As for a particular industry that has not taken DDoS as seriously as others, Teolis believes many e-commerce firms haven’t contemplated being the victim of a DDoS attack. “There are still the odd e-commerce guys out there [who haven’t taken it as seriously]. Money is rolling in and they’re just focused on that; DDoS for them is somebody else’s problem. A lot of it is ‘my ISP will deal with it’, the fact of the matter is, it is difficult to stop all of the attacks,” he said. Source: http://www.computing.co.uk/ctg/news/2325009/education-sector-is-fastest-growing-for-ddos-mitigation-dosarrest
See the original article here:
Education sector is fastest growing for DDoS mitigation

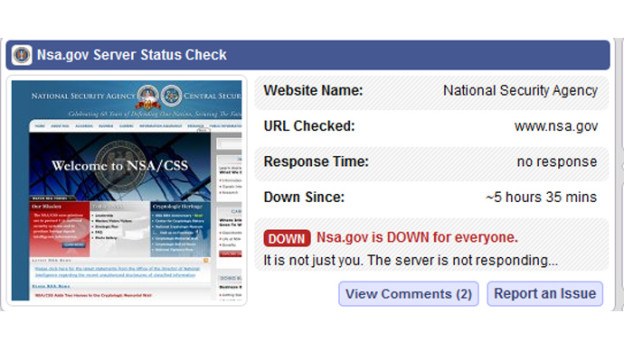
 The website for the United States National Security Agency suddenly went offline Friday. NSA.gov has been unavailable globally as of late Friday afternoon, and Twitter accounts belonging to people loosely affiliated with the Anonymous hacktivism movement have suggested they are responsible. Twitter users @AnonymousOwn3r and @TruthIzSexy both were quick to comment on the matter, and implied that a distributed denial-of-service attack, or DDoS, may have been waged as an act of protest against the NSA Allegations that those users participated in the DDoS — a method of over-loading a website with too much traffic — are currently unverified, and @AnonymousOwn3r has previously taken credit for downing websites in a similar fashion, although those claims have been largely contested. The crippling of NSA.gov comes amid a series of damning national security documents that have been disclosed without authorization by former intelligence contractor Edward Snowden. The revelations in the leaked documents have impassioned people around the globe outraged by evidence of widespread surveillance operated by the NSA, and a massive “Stop Watching Us” rally is scheduled for Saturday in Washington, DC. DDoS attacks are illegal in the United States under the Computer Fraud and Abuse Act, or CFAA, and two cases are currently underway in California and Virginia in which federal judges are weighing in on instances in which members of Anonymous allegedly used the technique to take down an array of sites during anti-copyright campaigns waged by the group in 2010 and 2011. In those cases, so-called hacktivsits are reported to have conspired together to send immense loads of traffic to targeted websites, rendering them inaccessible due to the overload.
The website for the United States National Security Agency suddenly went offline Friday. NSA.gov has been unavailable globally as of late Friday afternoon, and Twitter accounts belonging to people loosely affiliated with the Anonymous hacktivism movement have suggested they are responsible. Twitter users @AnonymousOwn3r and @TruthIzSexy both were quick to comment on the matter, and implied that a distributed denial-of-service attack, or DDoS, may have been waged as an act of protest against the NSA Allegations that those users participated in the DDoS — a method of over-loading a website with too much traffic — are currently unverified, and @AnonymousOwn3r has previously taken credit for downing websites in a similar fashion, although those claims have been largely contested. The crippling of NSA.gov comes amid a series of damning national security documents that have been disclosed without authorization by former intelligence contractor Edward Snowden. The revelations in the leaked documents have impassioned people around the globe outraged by evidence of widespread surveillance operated by the NSA, and a massive “Stop Watching Us” rally is scheduled for Saturday in Washington, DC. DDoS attacks are illegal in the United States under the Computer Fraud and Abuse Act, or CFAA, and two cases are currently underway in California and Virginia in which federal judges are weighing in on instances in which members of Anonymous allegedly used the technique to take down an array of sites during anti-copyright campaigns waged by the group in 2010 and 2011. In those cases, so-called hacktivsits are reported to have conspired together to send immense loads of traffic to targeted websites, rendering them inaccessible due to the overload.