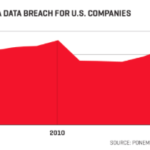
 Business is under assault from cybercriminals like never before, and the cost to companies is exploding. Here’s what you need to know about safeguarding your digital assets. 1. Under attack In the summer of 2015, several of New York’s most prestigious and trusted corporate law firms, including Cravath Swaine & Moore and Weil Gotshal & Manges, found themselves under cyberattack. A trio of hackers in China had snuck into the firms’ computer networks by tricking partners into revealing their email passwords. Once inside the partners’ accounts, the thieves snooped on highly sensitive documents about upcoming mergers. Then, from computers halfway around the world, the cybercrooks allegedly traded on the purloined information, netting $4 million in stock market gains. Like most other victims of corporate espionage, the firms preferred to keep mum about having been victimized. They feared antagonizing other digital thugs as well as damaging their reputations as keepers of clients’ secrets. Instead, word of the attack leaked in the press and then was confirmed by federal prosecutors and the firms themselves. The Feds made public their discoveries and trumpeted their efforts to bring the alleged perpetrators to justice. “This case of cyber meets securities fraud should serve as a wake-up call for law firms around the world,” said Preet Bharara, then the U.S. Attorney in Manhattan. “You are and will be the targets of cyberhacking because you have information valuable to would-be criminals.” It may have been a shock to the system for the legal community, but the incident only served to underscore a hard truth that CEOs, company directors, and network security experts have been grappling with for some time now: Business is under assault like never before from hackers, and the cost and severity of the problem is escalating almost daily. The latest statistics are a call to arms: According to Cisco, the number of so-called distributed denial-of-service (DDoS) attacks—assaults that flood a system’s servers with junk web traffic—jumped globally by 172% in 2016. Cisco projects the total to grow by another two and a half times, to 3.1 million attacks, by 2021. Indeed, the pace of cyberassaults is only increasing. Internet security firm Nexusguard reports that it observed a 380% increase in the number of DDoS attacks in the first quarter of 2017 compared with a year earlier. As the number and scale of network attacks grow, the toll on business is rising. The average total cost of a data breach in the U.S. in 2014 was $5.85 million, according to research from IBM and the Ponemon Institute, and this year it’s estimated to be $7.35 million. According to a report earlier this year from business insurer Hiscox, cybercrime cost the global economy more than $450 billion in 2016. The WannaCry ransomware attack alone, which crippled computers in more than 150 countries in May, could cost as much as $4 billion according to some estimates. What is slowly dawning on corporate hacking victims is how vulnerable and defenseless they really are, even when their opponents may be three guys in a room halfway around the world. Expensive data-security systems and high-priced information security consultants don’t faze today’s hackers, who have the resources to relentlessly mount assaults until they succeed. In the New York law-firm case, for example, prosecutors said the attackers attempted to penetrate targeted servers more than 100,000 times over seven months. It has become abundantly clear that no network is completely safe. Where once companies thought they could defend themselves against an onslaught, they’re now realizing that resistance is, if not futile, certainly less important than having a plan in place to detect and neutralize intruders when they strike. But there remains a gaping chasm between awareness of the threat and readiness to address it: A survey last fall by IBM and Ponemon of 2,400 security and IT professionals found that 75% of the respondents said they did not have a formal cybersecurity incident response plan across their organization. And 66% of those who replied weren’t confident in their organization’s ability to recover from an attack. Cybercrime is metastasizing for the same reason online services have become so popular with consumers and businesses alike: Ever-more-accessible technology. Hacking is easier than ever thanks to the ever-growing number of online targets and the proliferation of off-the-shelf attack software. The very Internet networks that were built for convenience and profit are exposing their users to a steady stream of new threats. What’s more, the tense state of affairs is a glaring example of how the entire nature of business has changed in the digital age. In most cases, technology is much more than just a supplement to a company’s core operations. For scores of the world’s most valuable companies—from Alphabet to Amazon to Facebook to Uber—the assets that live on their networks are their core operations. No sector of corporate America is safe. Hackers have plundered big retailers like Neiman Marcus and Home Depot for credit card and customer information. They’ve burrowed into banks like JPMorgan Chase. Even tech companies can’t seem to protect themselves. Yahoo’s ineptitude in repelling (or even being aware of) hackers forced it to reduce its sale price to Verizon. Google and Facebook recently fell victim to a hacker who conned their accountants into wiring him a total of more than $100 million. And OneLogin, a startup that bills itself as a secure password management service, recently lost certain customer data to hackers. In one survey, 66% of security and I.T. professionals replied that they weren’t confident that their organization could recover from a cyberattack. It’s not like companies aren’t trying to play defense. Accenture estimates that companies worldwide spent $84 billion in 2015 to protect against attacks. That spending is an acknowledgment that every company needs to safeguard its digital assets, which in turn requires knowing about the criminals that keep coming at them and what defenses they can build to minimize the damage. 2. A new breed of criminal Hacking is particularly frustrating for corporate executives who don’t understand their enemy. Embezzlers or extortionists? Sure. But faceless gangs of nasty nerds? It’s often harder for CEOs to wrap their brains around the motivation of their antagonists—or their audacity. “At the C-level they feel violated,” says Jay Leek, a venture capitalist pursuing cybersecurity investments and a former chief information security officer at private equity giant Blackstone. “I witness this emotional ‘What just happened?’ You don’t walk in physically to a company and violate it.” The brazenness Leek describes is a hallmark of hackers who—despite their mystique in popular culture—are basically everyday thieves, like bank robbers. Where hackers are different, however, is that they rarely meet in person. Instead, they convene in online forums on the “dark web,” an anonymous layer of the Internet that requires a special browser to access. Deep in the forums, crooks hatch hacking plots of all sorts: breaking into corporate databases or selling stolen Social Security numbers or purchasing inside information from unscrupulous employees. Cybercriminals have proved adept at adopting successful corporate strategies of their own. A recent development has seen the cleverest crooks selling hacking tools to criminal small-fry. It’s analogous to semiconductor companies licensing their technology to device manufacturers. According to a report from security software giant Symantec, gangs now offer so-called ransomware as a service, a trick that involves licensing software that freezes computer files until a company pays up. The gangs then take their cut for providing the license to their criminal customers. If it weren’t all blatantly illegal, the practices would be laudably corporate. “Cybercriminals no longer need all the skills to complete any particular crime,” says Nicole Friedlander, a former assistant U.S. Attorney in charge of the key Southern District of New York’s complex fraud and cybercrime unit. “Instead, they can hire other cybercriminals online who have those skills and do it together.” In that sense, hackers have become service providers like doctors or lawyers or anyone else, says Friedlander, who joined the New York office of law firm Sullivan & Cromwell last year. Graphic by Nicolas Rapp But the bad guys aren’t all freelancers. In fact, some of the most sinister hacking outfits operating today are “state-sponsored” groups supported, or at least loosely supervised, by governments. That includes the Russians who are believed to have hacked into the Democratic National Committee last year and the North Korean team credited with unleashing the WannaCry malware as a moneymaking scheme. 3. Playing defense In early March, the information security team at ride-hailing giant Uber leaped into action: An Uber employee had reported a suspicious email message, and similar reports were flooding in from all over the company. Uber’s databases contain the email addresses and personal information of millions of riders around the world, making security a particularly pressing issue. And the company has had its share of problems as a caretaker of sensitive data. In 2014, Uber suffered a breach that exposed the insurance and driver’s license information of tens of thousands of drivers; it took the mega-startup months to discover and investigate the incident and fully notify its drivers. As soon as the alarm was raised in March, Uber established an “incident commander” to manage the developing situation. The job of the incident commander—a term of art in cybersecurity circles—is to keep the company informed about potential attacks. It turned out that the attack was targeting users of Google’s Gmail service, not Uber itself. But anyone with a Gmail address was vulnerable. Later that same day Google fixed the vulnerability in its Gmail service, allowing Uber’s incident commander to stand down. Uber’s reaction is an example of the vigilance with which companies must treat the torrent of threats coming at them every day. John “Four” Flynn, a former Facebook executive who now is chief information security officer for Uber, says the key to cybersecurity incidents—which he defines as everything from a data breach to a stolen laptop—is to have a clear communication strategy. “During an incident, the role of executives is to give support,” says Flynn. “There’s no room for confusion about who’s in charge.” Graphic by Nicolas Rapp Flynn has every right to sound confident in his authority. The chief information security officer, or CISO, is possibly the hottest job in the C-suite today. Cybercrime is so serious that these formerly little-known and unloved executives now typically have a direct line to boards of directors—a big break from the past. Before, the CISO would report to the chief information officer, who was responsible for buying and operating computers, not obsessing over flies in the ointment. If the CISO sounded the alarm over a breach, too often he or she ended up being the one sacrificed to appease top management. “It was my job to tell my boss his baby was ugly,” one former information security executive laments. These days, though, smart companies treat hacking threats like other existential risks to their business—recessions, terrorist attacks, and natural disasters come to mind—and plan accordingly. The CISO is pivotal in maintaining readiness. “If you’re a Fortune 500 company, you already have a response,” says Leek, the former executive at Blackstone, which had several portfolio companies that suffered breaches, including arts-and-crafts merchant Michaels Stores. “But people forget to take it out, blow the dust off, and recall: ‘Let’s do what we decided when we had a sound mind.’ ” Having a clear line of authority and a good action plan take a company only so far. At some point it has to call the cops, specifically the Federal Bureau of Investigation or the U.S. Secret Service. Both agencies have reach and power that allow them to take the fight to foreign cybercrooks. On several occasions, U.S. law enforcement agents working undercover on the dark web have managed to lure presumed offenders out of hiding with phony deals, and then had them apprehended in and extradited to the U.S. During the incident, the role of executives is to give support,” says Uber’s chief information officer. “There’s no room for confusion about who’s in charge.” Calling law enforcement has downsides, however. The likely outcome—an investigation—imposes burdens on the victim company in terms of money and time. And it increases the chance that sensitive details about the hack will leak publicly. That’s why the best course of action is for companies to avoid FBI-level hacking incidents in the first place. A new, multibillion-dollar industry has sprung up to help. 4. An industry is born The videoconference camera looked like any other. But unbeknownst to its corporate owner, the device was working overtime: Hackers had captured the microphone remotely and were using it to spy on every meeting that took place in the boardroom. The company, which does not want to be identified, finally got wise to the spying scheme thanks to Darktrace, a global cybersecurity company that uses artificial intelligence to detect aberrant activity on client networks. Darktrace CEO Nicole Eagan says her company noticed the camera had been gobbling abnormal amounts of data. This raised a red flag, enabling Darktrace to notify its client that something was amiss. Darktrace is just one of hundreds of firms that offer help to combat the hacking epidemic. Once a stodgy corner of enterprise software, cybersecurity has become a hot sector for venture capitalists. Investors put some $3.5 billion into a total of 404 security startups last year, according to New York research firm CB Insights. That’s up from $1.8 billion for 279 investments in 2013. Graphic by Nicolas Rapp For executives, all of this entrepreneurial activity translates into a dizzying array of security options. There are newcomers like Tanium, for instance, which offers a service that lets companies see who is on their network. Publicly traded Palo Alto Networks makes a kind of intelligent firewall that uses machine learning to thwart intruders. There are also a host of niche security firms such as Area 1 (which specializes in defending against phishing scams) and Lookout (which is a mobile-phone-focused security service). With all of this firepower arrayed against it, how can cybercrime continue to grow so fast? One answer is that some of the glitzy defense systems don’t work as advertised. Security insiders grumble about firms bamboozling clients with “blinky lights” in order to sell “scareware”—software that plays to customers’ insecurities but doesn’t protect them. At the end of the day, though, humans are as much to blame as software. “The weak underbelly of security is not tech failure but poor process implementation or social engineering,” says Asheem Chandna, an investor with Greylock Partners and a Palo Alto Networks director. Chandna notes that most hacking attacks come about in two ways, neither of which involves a high level of technical sophistication: An employee clicks on a booby-trapped link or attachment—perhaps in an email that appears to be from her boss—or someone steals an employee’s log-in credentials and gets access to the company network. While cyberdefense tools can mitigate such attacks, some will always succeed. Humans are curious creatures and, in a big organization, there will always be someone who clicks on a message like, “Uh-oh. Did you see these pictures of you from the office party?” When it comes to hacking, a penny of offense can defeat a dollar’s worth of defense. That’s why the fight against hacking promises to be a never-ending battle. Source: https://fortune.com/2017/06/22/cybersecurity-business-fights-back/
Business is under assault from cybercriminals like never before, and the cost to companies is exploding. Here’s what you need to know about safeguarding your digital assets. 1. Under attack In the summer of 2015, several of New York’s most prestigious and trusted corporate law firms, including Cravath Swaine & Moore and Weil Gotshal & Manges, found themselves under cyberattack. A trio of hackers in China had snuck into the firms’ computer networks by tricking partners into revealing their email passwords. Once inside the partners’ accounts, the thieves snooped on highly sensitive documents about upcoming mergers. Then, from computers halfway around the world, the cybercrooks allegedly traded on the purloined information, netting $4 million in stock market gains. Like most other victims of corporate espionage, the firms preferred to keep mum about having been victimized. They feared antagonizing other digital thugs as well as damaging their reputations as keepers of clients’ secrets. Instead, word of the attack leaked in the press and then was confirmed by federal prosecutors and the firms themselves. The Feds made public their discoveries and trumpeted their efforts to bring the alleged perpetrators to justice. “This case of cyber meets securities fraud should serve as a wake-up call for law firms around the world,” said Preet Bharara, then the U.S. Attorney in Manhattan. “You are and will be the targets of cyberhacking because you have information valuable to would-be criminals.” It may have been a shock to the system for the legal community, but the incident only served to underscore a hard truth that CEOs, company directors, and network security experts have been grappling with for some time now: Business is under assault like never before from hackers, and the cost and severity of the problem is escalating almost daily. The latest statistics are a call to arms: According to Cisco, the number of so-called distributed denial-of-service (DDoS) attacks—assaults that flood a system’s servers with junk web traffic—jumped globally by 172% in 2016. Cisco projects the total to grow by another two and a half times, to 3.1 million attacks, by 2021. Indeed, the pace of cyberassaults is only increasing. Internet security firm Nexusguard reports that it observed a 380% increase in the number of DDoS attacks in the first quarter of 2017 compared with a year earlier. As the number and scale of network attacks grow, the toll on business is rising. The average total cost of a data breach in the U.S. in 2014 was $5.85 million, according to research from IBM and the Ponemon Institute, and this year it’s estimated to be $7.35 million. According to a report earlier this year from business insurer Hiscox, cybercrime cost the global economy more than $450 billion in 2016. The WannaCry ransomware attack alone, which crippled computers in more than 150 countries in May, could cost as much as $4 billion according to some estimates. What is slowly dawning on corporate hacking victims is how vulnerable and defenseless they really are, even when their opponents may be three guys in a room halfway around the world. Expensive data-security systems and high-priced information security consultants don’t faze today’s hackers, who have the resources to relentlessly mount assaults until they succeed. In the New York law-firm case, for example, prosecutors said the attackers attempted to penetrate targeted servers more than 100,000 times over seven months. It has become abundantly clear that no network is completely safe. Where once companies thought they could defend themselves against an onslaught, they’re now realizing that resistance is, if not futile, certainly less important than having a plan in place to detect and neutralize intruders when they strike. But there remains a gaping chasm between awareness of the threat and readiness to address it: A survey last fall by IBM and Ponemon of 2,400 security and IT professionals found that 75% of the respondents said they did not have a formal cybersecurity incident response plan across their organization. And 66% of those who replied weren’t confident in their organization’s ability to recover from an attack. Cybercrime is metastasizing for the same reason online services have become so popular with consumers and businesses alike: Ever-more-accessible technology. Hacking is easier than ever thanks to the ever-growing number of online targets and the proliferation of off-the-shelf attack software. The very Internet networks that were built for convenience and profit are exposing their users to a steady stream of new threats. What’s more, the tense state of affairs is a glaring example of how the entire nature of business has changed in the digital age. In most cases, technology is much more than just a supplement to a company’s core operations. For scores of the world’s most valuable companies—from Alphabet to Amazon to Facebook to Uber—the assets that live on their networks are their core operations. No sector of corporate America is safe. Hackers have plundered big retailers like Neiman Marcus and Home Depot for credit card and customer information. They’ve burrowed into banks like JPMorgan Chase. Even tech companies can’t seem to protect themselves. Yahoo’s ineptitude in repelling (or even being aware of) hackers forced it to reduce its sale price to Verizon. Google and Facebook recently fell victim to a hacker who conned their accountants into wiring him a total of more than $100 million. And OneLogin, a startup that bills itself as a secure password management service, recently lost certain customer data to hackers. In one survey, 66% of security and I.T. professionals replied that they weren’t confident that their organization could recover from a cyberattack. It’s not like companies aren’t trying to play defense. Accenture estimates that companies worldwide spent $84 billion in 2015 to protect against attacks. That spending is an acknowledgment that every company needs to safeguard its digital assets, which in turn requires knowing about the criminals that keep coming at them and what defenses they can build to minimize the damage. 2. A new breed of criminal Hacking is particularly frustrating for corporate executives who don’t understand their enemy. Embezzlers or extortionists? Sure. But faceless gangs of nasty nerds? It’s often harder for CEOs to wrap their brains around the motivation of their antagonists—or their audacity. “At the C-level they feel violated,” says Jay Leek, a venture capitalist pursuing cybersecurity investments and a former chief information security officer at private equity giant Blackstone. “I witness this emotional ‘What just happened?’ You don’t walk in physically to a company and violate it.” The brazenness Leek describes is a hallmark of hackers who—despite their mystique in popular culture—are basically everyday thieves, like bank robbers. Where hackers are different, however, is that they rarely meet in person. Instead, they convene in online forums on the “dark web,” an anonymous layer of the Internet that requires a special browser to access. Deep in the forums, crooks hatch hacking plots of all sorts: breaking into corporate databases or selling stolen Social Security numbers or purchasing inside information from unscrupulous employees. Cybercriminals have proved adept at adopting successful corporate strategies of their own. A recent development has seen the cleverest crooks selling hacking tools to criminal small-fry. It’s analogous to semiconductor companies licensing their technology to device manufacturers. According to a report from security software giant Symantec, gangs now offer so-called ransomware as a service, a trick that involves licensing software that freezes computer files until a company pays up. The gangs then take their cut for providing the license to their criminal customers. If it weren’t all blatantly illegal, the practices would be laudably corporate. “Cybercriminals no longer need all the skills to complete any particular crime,” says Nicole Friedlander, a former assistant U.S. Attorney in charge of the key Southern District of New York’s complex fraud and cybercrime unit. “Instead, they can hire other cybercriminals online who have those skills and do it together.” In that sense, hackers have become service providers like doctors or lawyers or anyone else, says Friedlander, who joined the New York office of law firm Sullivan & Cromwell last year. Graphic by Nicolas Rapp But the bad guys aren’t all freelancers. In fact, some of the most sinister hacking outfits operating today are “state-sponsored” groups supported, or at least loosely supervised, by governments. That includes the Russians who are believed to have hacked into the Democratic National Committee last year and the North Korean team credited with unleashing the WannaCry malware as a moneymaking scheme. 3. Playing defense In early March, the information security team at ride-hailing giant Uber leaped into action: An Uber employee had reported a suspicious email message, and similar reports were flooding in from all over the company. Uber’s databases contain the email addresses and personal information of millions of riders around the world, making security a particularly pressing issue. And the company has had its share of problems as a caretaker of sensitive data. In 2014, Uber suffered a breach that exposed the insurance and driver’s license information of tens of thousands of drivers; it took the mega-startup months to discover and investigate the incident and fully notify its drivers. As soon as the alarm was raised in March, Uber established an “incident commander” to manage the developing situation. The job of the incident commander—a term of art in cybersecurity circles—is to keep the company informed about potential attacks. It turned out that the attack was targeting users of Google’s Gmail service, not Uber itself. But anyone with a Gmail address was vulnerable. Later that same day Google fixed the vulnerability in its Gmail service, allowing Uber’s incident commander to stand down. Uber’s reaction is an example of the vigilance with which companies must treat the torrent of threats coming at them every day. John “Four” Flynn, a former Facebook executive who now is chief information security officer for Uber, says the key to cybersecurity incidents—which he defines as everything from a data breach to a stolen laptop—is to have a clear communication strategy. “During an incident, the role of executives is to give support,” says Flynn. “There’s no room for confusion about who’s in charge.” Graphic by Nicolas Rapp Flynn has every right to sound confident in his authority. The chief information security officer, or CISO, is possibly the hottest job in the C-suite today. Cybercrime is so serious that these formerly little-known and unloved executives now typically have a direct line to boards of directors—a big break from the past. Before, the CISO would report to the chief information officer, who was responsible for buying and operating computers, not obsessing over flies in the ointment. If the CISO sounded the alarm over a breach, too often he or she ended up being the one sacrificed to appease top management. “It was my job to tell my boss his baby was ugly,” one former information security executive laments. These days, though, smart companies treat hacking threats like other existential risks to their business—recessions, terrorist attacks, and natural disasters come to mind—and plan accordingly. The CISO is pivotal in maintaining readiness. “If you’re a Fortune 500 company, you already have a response,” says Leek, the former executive at Blackstone, which had several portfolio companies that suffered breaches, including arts-and-crafts merchant Michaels Stores. “But people forget to take it out, blow the dust off, and recall: ‘Let’s do what we decided when we had a sound mind.’ ” Having a clear line of authority and a good action plan take a company only so far. At some point it has to call the cops, specifically the Federal Bureau of Investigation or the U.S. Secret Service. Both agencies have reach and power that allow them to take the fight to foreign cybercrooks. On several occasions, U.S. law enforcement agents working undercover on the dark web have managed to lure presumed offenders out of hiding with phony deals, and then had them apprehended in and extradited to the U.S. During the incident, the role of executives is to give support,” says Uber’s chief information officer. “There’s no room for confusion about who’s in charge.” Calling law enforcement has downsides, however. The likely outcome—an investigation—imposes burdens on the victim company in terms of money and time. And it increases the chance that sensitive details about the hack will leak publicly. That’s why the best course of action is for companies to avoid FBI-level hacking incidents in the first place. A new, multibillion-dollar industry has sprung up to help. 4. An industry is born The videoconference camera looked like any other. But unbeknownst to its corporate owner, the device was working overtime: Hackers had captured the microphone remotely and were using it to spy on every meeting that took place in the boardroom. The company, which does not want to be identified, finally got wise to the spying scheme thanks to Darktrace, a global cybersecurity company that uses artificial intelligence to detect aberrant activity on client networks. Darktrace CEO Nicole Eagan says her company noticed the camera had been gobbling abnormal amounts of data. This raised a red flag, enabling Darktrace to notify its client that something was amiss. Darktrace is just one of hundreds of firms that offer help to combat the hacking epidemic. Once a stodgy corner of enterprise software, cybersecurity has become a hot sector for venture capitalists. Investors put some $3.5 billion into a total of 404 security startups last year, according to New York research firm CB Insights. That’s up from $1.8 billion for 279 investments in 2013. Graphic by Nicolas Rapp For executives, all of this entrepreneurial activity translates into a dizzying array of security options. There are newcomers like Tanium, for instance, which offers a service that lets companies see who is on their network. Publicly traded Palo Alto Networks makes a kind of intelligent firewall that uses machine learning to thwart intruders. There are also a host of niche security firms such as Area 1 (which specializes in defending against phishing scams) and Lookout (which is a mobile-phone-focused security service). With all of this firepower arrayed against it, how can cybercrime continue to grow so fast? One answer is that some of the glitzy defense systems don’t work as advertised. Security insiders grumble about firms bamboozling clients with “blinky lights” in order to sell “scareware”—software that plays to customers’ insecurities but doesn’t protect them. At the end of the day, though, humans are as much to blame as software. “The weak underbelly of security is not tech failure but poor process implementation or social engineering,” says Asheem Chandna, an investor with Greylock Partners and a Palo Alto Networks director. Chandna notes that most hacking attacks come about in two ways, neither of which involves a high level of technical sophistication: An employee clicks on a booby-trapped link or attachment—perhaps in an email that appears to be from her boss—or someone steals an employee’s log-in credentials and gets access to the company network. While cyberdefense tools can mitigate such attacks, some will always succeed. Humans are curious creatures and, in a big organization, there will always be someone who clicks on a message like, “Uh-oh. Did you see these pictures of you from the office party?” When it comes to hacking, a penny of offense can defeat a dollar’s worth of defense. That’s why the fight against hacking promises to be a never-ending battle. Source: https://fortune.com/2017/06/22/cybersecurity-business-fights-back/
See the article here:
Hacked: How Business Is Fighting Back Against the Explosion in Cybercrime


 Business is under assault from cybercriminals like never before, and the cost to companies is exploding. Here’s what you need to know about safeguarding your digital assets. 1. Under attack In the summer of 2015, several of New York’s most prestigious and trusted corporate law firms, including Cravath Swaine & Moore and Weil Gotshal & Manges, found themselves under cyberattack. A trio of hackers in China had snuck into the firms’ computer networks by tricking partners into revealing their email passwords. Once inside the partners’ accounts, the thieves snooped on highly sensitive documents about upcoming mergers. Then, from computers halfway around the world, the cybercrooks allegedly traded on the purloined information, netting $4 million in stock market gains. Like most other victims of corporate espionage, the firms preferred to keep mum about having been victimized. They feared antagonizing other digital thugs as well as damaging their reputations as keepers of clients’ secrets. Instead, word of the attack leaked in the press and then was confirmed by federal prosecutors and the firms themselves. The Feds made public their discoveries and trumpeted their efforts to bring the alleged perpetrators to justice. “This case of cyber meets securities fraud should serve as a wake-up call for law firms around the world,” said Preet Bharara, then the U.S. Attorney in Manhattan. “You are and will be the targets of cyberhacking because you have information valuable to would-be criminals.” It may have been a shock to the system for the legal community, but the incident only served to underscore a hard truth that CEOs, company directors, and network security experts have been grappling with for some time now: Business is under assault like never before from hackers, and the cost and severity of the problem is escalating almost daily. The latest statistics are a call to arms: According to Cisco, the number of so-called distributed denial-of-service (DDoS) attacks—assaults that flood a system’s servers with junk web traffic—jumped globally by 172% in 2016. Cisco projects the total to grow by another two and a half times, to 3.1 million attacks, by 2021. Indeed, the pace of cyberassaults is only increasing. Internet security firm Nexusguard reports that it observed a 380% increase in the number of DDoS attacks in the first quarter of 2017 compared with a year earlier. As the number and scale of network attacks grow, the toll on business is rising. The average total cost of a data breach in the U.S. in 2014 was $5.85 million, according to research from IBM and the Ponemon Institute, and this year it’s estimated to be $7.35 million. According to a report earlier this year from business insurer Hiscox, cybercrime cost the global economy more than $450 billion in 2016. The WannaCry ransomware attack alone, which crippled computers in more than 150 countries in May, could cost as much as $4 billion according to some estimates. What is slowly dawning on corporate hacking victims is how vulnerable and defenseless they really are, even when their opponents may be three guys in a room halfway around the world. Expensive data-security systems and high-priced information security consultants don’t faze today’s hackers, who have the resources to relentlessly mount assaults until they succeed. In the New York law-firm case, for example, prosecutors said the attackers attempted to penetrate targeted servers more than 100,000 times over seven months. It has become abundantly clear that no network is completely safe. Where once companies thought they could defend themselves against an onslaught, they’re now realizing that resistance is, if not futile, certainly less important than having a plan in place to detect and neutralize intruders when they strike. But there remains a gaping chasm between awareness of the threat and readiness to address it: A survey last fall by IBM and Ponemon of 2,400 security and IT professionals found that 75% of the respondents said they did not have a formal cybersecurity incident response plan across their organization. And 66% of those who replied weren’t confident in their organization’s ability to recover from an attack. Cybercrime is metastasizing for the same reason online services have become so popular with consumers and businesses alike: Ever-more-accessible technology. Hacking is easier than ever thanks to the ever-growing number of online targets and the proliferation of off-the-shelf attack software. The very Internet networks that were built for convenience and profit are exposing their users to a steady stream of new threats. What’s more, the tense state of affairs is a glaring example of how the entire nature of business has changed in the digital age. In most cases, technology is much more than just a supplement to a company’s core operations. For scores of the world’s most valuable companies—from Alphabet to Amazon to Facebook to Uber—the assets that live on their networks are their core operations. No sector of corporate America is safe. Hackers have plundered big retailers like Neiman Marcus and Home Depot for credit card and customer information. They’ve burrowed into banks like JPMorgan Chase. Even tech companies can’t seem to protect themselves. Yahoo’s ineptitude in repelling (or even being aware of) hackers forced it to reduce its sale price to Verizon. Google and Facebook recently fell victim to a hacker who conned their accountants into wiring him a total of more than $100 million. And OneLogin, a startup that bills itself as a secure password management service, recently lost certain customer data to hackers. In one survey, 66% of security and I.T. professionals replied that they weren’t confident that their organization could recover from a cyberattack. It’s not like companies aren’t trying to play defense. Accenture estimates that companies worldwide spent $84 billion in 2015 to protect against attacks. That spending is an acknowledgment that every company needs to safeguard its digital assets, which in turn requires knowing about the criminals that keep coming at them and what defenses they can build to minimize the damage. 2. A new breed of criminal Hacking is particularly frustrating for corporate executives who don’t understand their enemy. Embezzlers or extortionists? Sure. But faceless gangs of nasty nerds? It’s often harder for CEOs to wrap their brains around the motivation of their antagonists—or their audacity. “At the C-level they feel violated,” says Jay Leek, a venture capitalist pursuing cybersecurity investments and a former chief information security officer at private equity giant Blackstone. “I witness this emotional ‘What just happened?’ You don’t walk in physically to a company and violate it.” The brazenness Leek describes is a hallmark of hackers who—despite their mystique in popular culture—are basically everyday thieves, like bank robbers. Where hackers are different, however, is that they rarely meet in person. Instead, they convene in online forums on the “dark web,” an anonymous layer of the Internet that requires a special browser to access. Deep in the forums, crooks hatch hacking plots of all sorts: breaking into corporate databases or selling stolen Social Security numbers or purchasing inside information from unscrupulous employees. Cybercriminals have proved adept at adopting successful corporate strategies of their own. A recent development has seen the cleverest crooks selling hacking tools to criminal small-fry. It’s analogous to semiconductor companies licensing their technology to device manufacturers. According to a report from security software giant Symantec, gangs now offer so-called ransomware as a service, a trick that involves licensing software that freezes computer files until a company pays up. The gangs then take their cut for providing the license to their criminal customers. If it weren’t all blatantly illegal, the practices would be laudably corporate. “Cybercriminals no longer need all the skills to complete any particular crime,” says Nicole Friedlander, a former assistant U.S. Attorney in charge of the key Southern District of New York’s complex fraud and cybercrime unit. “Instead, they can hire other cybercriminals online who have those skills and do it together.” In that sense, hackers have become service providers like doctors or lawyers or anyone else, says Friedlander, who joined the New York office of law firm Sullivan & Cromwell last year. Graphic by Nicolas Rapp But the bad guys aren’t all freelancers. In fact, some of the most sinister hacking outfits operating today are “state-sponsored” groups supported, or at least loosely supervised, by governments. That includes the Russians who are believed to have hacked into the Democratic National Committee last year and the North Korean team credited with unleashing the WannaCry malware as a moneymaking scheme. 3. Playing defense In early March, the information security team at ride-hailing giant Uber leaped into action: An Uber employee had reported a suspicious email message, and similar reports were flooding in from all over the company. Uber’s databases contain the email addresses and personal information of millions of riders around the world, making security a particularly pressing issue. And the company has had its share of problems as a caretaker of sensitive data. In 2014, Uber suffered a breach that exposed the insurance and driver’s license information of tens of thousands of drivers; it took the mega-startup months to discover and investigate the incident and fully notify its drivers. As soon as the alarm was raised in March, Uber established an “incident commander” to manage the developing situation. The job of the incident commander—a term of art in cybersecurity circles—is to keep the company informed about potential attacks. It turned out that the attack was targeting users of Google’s Gmail service, not Uber itself. But anyone with a Gmail address was vulnerable. Later that same day Google fixed the vulnerability in its Gmail service, allowing Uber’s incident commander to stand down. Uber’s reaction is an example of the vigilance with which companies must treat the torrent of threats coming at them every day. John “Four” Flynn, a former Facebook executive who now is chief information security officer for Uber, says the key to cybersecurity incidents—which he defines as everything from a data breach to a stolen laptop—is to have a clear communication strategy. “During an incident, the role of executives is to give support,” says Flynn. “There’s no room for confusion about who’s in charge.” Graphic by Nicolas Rapp Flynn has every right to sound confident in his authority. The chief information security officer, or CISO, is possibly the hottest job in the C-suite today. Cybercrime is so serious that these formerly little-known and unloved executives now typically have a direct line to boards of directors—a big break from the past. Before, the CISO would report to the chief information officer, who was responsible for buying and operating computers, not obsessing over flies in the ointment. If the CISO sounded the alarm over a breach, too often he or she ended up being the one sacrificed to appease top management. “It was my job to tell my boss his baby was ugly,” one former information security executive laments. These days, though, smart companies treat hacking threats like other existential risks to their business—recessions, terrorist attacks, and natural disasters come to mind—and plan accordingly. The CISO is pivotal in maintaining readiness. “If you’re a Fortune 500 company, you already have a response,” says Leek, the former executive at Blackstone, which had several portfolio companies that suffered breaches, including arts-and-crafts merchant Michaels Stores. “But people forget to take it out, blow the dust off, and recall: ‘Let’s do what we decided when we had a sound mind.’ ” Having a clear line of authority and a good action plan take a company only so far. At some point it has to call the cops, specifically the Federal Bureau of Investigation or the U.S. Secret Service. Both agencies have reach and power that allow them to take the fight to foreign cybercrooks. On several occasions, U.S. law enforcement agents working undercover on the dark web have managed to lure presumed offenders out of hiding with phony deals, and then had them apprehended in and extradited to the U.S. During the incident, the role of executives is to give support,” says Uber’s chief information officer. “There’s no room for confusion about who’s in charge.” Calling law enforcement has downsides, however. The likely outcome—an investigation—imposes burdens on the victim company in terms of money and time. And it increases the chance that sensitive details about the hack will leak publicly. That’s why the best course of action is for companies to avoid FBI-level hacking incidents in the first place. A new, multibillion-dollar industry has sprung up to help. 4. An industry is born The videoconference camera looked like any other. But unbeknownst to its corporate owner, the device was working overtime: Hackers had captured the microphone remotely and were using it to spy on every meeting that took place in the boardroom. The company, which does not want to be identified, finally got wise to the spying scheme thanks to Darktrace, a global cybersecurity company that uses artificial intelligence to detect aberrant activity on client networks. Darktrace CEO Nicole Eagan says her company noticed the camera had been gobbling abnormal amounts of data. This raised a red flag, enabling Darktrace to notify its client that something was amiss. Darktrace is just one of hundreds of firms that offer help to combat the hacking epidemic. Once a stodgy corner of enterprise software, cybersecurity has become a hot sector for venture capitalists. Investors put some $3.5 billion into a total of 404 security startups last year, according to New York research firm CB Insights. That’s up from $1.8 billion for 279 investments in 2013. Graphic by Nicolas Rapp For executives, all of this entrepreneurial activity translates into a dizzying array of security options. There are newcomers like Tanium, for instance, which offers a service that lets companies see who is on their network. Publicly traded Palo Alto Networks makes a kind of intelligent firewall that uses machine learning to thwart intruders. There are also a host of niche security firms such as Area 1 (which specializes in defending against phishing scams) and Lookout (which is a mobile-phone-focused security service). With all of this firepower arrayed against it, how can cybercrime continue to grow so fast? One answer is that some of the glitzy defense systems don’t work as advertised. Security insiders grumble about firms bamboozling clients with “blinky lights” in order to sell “scareware”—software that plays to customers’ insecurities but doesn’t protect them. At the end of the day, though, humans are as much to blame as software. “The weak underbelly of security is not tech failure but poor process implementation or social engineering,” says Asheem Chandna, an investor with Greylock Partners and a Palo Alto Networks director. Chandna notes that most hacking attacks come about in two ways, neither of which involves a high level of technical sophistication: An employee clicks on a booby-trapped link or attachment—perhaps in an email that appears to be from her boss—or someone steals an employee’s log-in credentials and gets access to the company network. While cyberdefense tools can mitigate such attacks, some will always succeed. Humans are curious creatures and, in a big organization, there will always be someone who clicks on a message like, “Uh-oh. Did you see these pictures of you from the office party?” When it comes to hacking, a penny of offense can defeat a dollar’s worth of defense. That’s why the fight against hacking promises to be a never-ending battle. Source: https://fortune.com/2017/06/22/cybersecurity-business-fights-back/
Business is under assault from cybercriminals like never before, and the cost to companies is exploding. Here’s what you need to know about safeguarding your digital assets. 1. Under attack In the summer of 2015, several of New York’s most prestigious and trusted corporate law firms, including Cravath Swaine & Moore and Weil Gotshal & Manges, found themselves under cyberattack. A trio of hackers in China had snuck into the firms’ computer networks by tricking partners into revealing their email passwords. Once inside the partners’ accounts, the thieves snooped on highly sensitive documents about upcoming mergers. Then, from computers halfway around the world, the cybercrooks allegedly traded on the purloined information, netting $4 million in stock market gains. Like most other victims of corporate espionage, the firms preferred to keep mum about having been victimized. They feared antagonizing other digital thugs as well as damaging their reputations as keepers of clients’ secrets. Instead, word of the attack leaked in the press and then was confirmed by federal prosecutors and the firms themselves. The Feds made public their discoveries and trumpeted their efforts to bring the alleged perpetrators to justice. “This case of cyber meets securities fraud should serve as a wake-up call for law firms around the world,” said Preet Bharara, then the U.S. Attorney in Manhattan. “You are and will be the targets of cyberhacking because you have information valuable to would-be criminals.” It may have been a shock to the system for the legal community, but the incident only served to underscore a hard truth that CEOs, company directors, and network security experts have been grappling with for some time now: Business is under assault like never before from hackers, and the cost and severity of the problem is escalating almost daily. The latest statistics are a call to arms: According to Cisco, the number of so-called distributed denial-of-service (DDoS) attacks—assaults that flood a system’s servers with junk web traffic—jumped globally by 172% in 2016. Cisco projects the total to grow by another two and a half times, to 3.1 million attacks, by 2021. Indeed, the pace of cyberassaults is only increasing. Internet security firm Nexusguard reports that it observed a 380% increase in the number of DDoS attacks in the first quarter of 2017 compared with a year earlier. As the number and scale of network attacks grow, the toll on business is rising. The average total cost of a data breach in the U.S. in 2014 was $5.85 million, according to research from IBM and the Ponemon Institute, and this year it’s estimated to be $7.35 million. According to a report earlier this year from business insurer Hiscox, cybercrime cost the global economy more than $450 billion in 2016. The WannaCry ransomware attack alone, which crippled computers in more than 150 countries in May, could cost as much as $4 billion according to some estimates. What is slowly dawning on corporate hacking victims is how vulnerable and defenseless they really are, even when their opponents may be three guys in a room halfway around the world. Expensive data-security systems and high-priced information security consultants don’t faze today’s hackers, who have the resources to relentlessly mount assaults until they succeed. In the New York law-firm case, for example, prosecutors said the attackers attempted to penetrate targeted servers more than 100,000 times over seven months. It has become abundantly clear that no network is completely safe. Where once companies thought they could defend themselves against an onslaught, they’re now realizing that resistance is, if not futile, certainly less important than having a plan in place to detect and neutralize intruders when they strike. But there remains a gaping chasm between awareness of the threat and readiness to address it: A survey last fall by IBM and Ponemon of 2,400 security and IT professionals found that 75% of the respondents said they did not have a formal cybersecurity incident response plan across their organization. And 66% of those who replied weren’t confident in their organization’s ability to recover from an attack. Cybercrime is metastasizing for the same reason online services have become so popular with consumers and businesses alike: Ever-more-accessible technology. Hacking is easier than ever thanks to the ever-growing number of online targets and the proliferation of off-the-shelf attack software. The very Internet networks that were built for convenience and profit are exposing their users to a steady stream of new threats. What’s more, the tense state of affairs is a glaring example of how the entire nature of business has changed in the digital age. In most cases, technology is much more than just a supplement to a company’s core operations. For scores of the world’s most valuable companies—from Alphabet to Amazon to Facebook to Uber—the assets that live on their networks are their core operations. No sector of corporate America is safe. Hackers have plundered big retailers like Neiman Marcus and Home Depot for credit card and customer information. They’ve burrowed into banks like JPMorgan Chase. Even tech companies can’t seem to protect themselves. Yahoo’s ineptitude in repelling (or even being aware of) hackers forced it to reduce its sale price to Verizon. Google and Facebook recently fell victim to a hacker who conned their accountants into wiring him a total of more than $100 million. And OneLogin, a startup that bills itself as a secure password management service, recently lost certain customer data to hackers. In one survey, 66% of security and I.T. professionals replied that they weren’t confident that their organization could recover from a cyberattack. It’s not like companies aren’t trying to play defense. Accenture estimates that companies worldwide spent $84 billion in 2015 to protect against attacks. That spending is an acknowledgment that every company needs to safeguard its digital assets, which in turn requires knowing about the criminals that keep coming at them and what defenses they can build to minimize the damage. 2. A new breed of criminal Hacking is particularly frustrating for corporate executives who don’t understand their enemy. Embezzlers or extortionists? Sure. But faceless gangs of nasty nerds? It’s often harder for CEOs to wrap their brains around the motivation of their antagonists—or their audacity. “At the C-level they feel violated,” says Jay Leek, a venture capitalist pursuing cybersecurity investments and a former chief information security officer at private equity giant Blackstone. “I witness this emotional ‘What just happened?’ You don’t walk in physically to a company and violate it.” The brazenness Leek describes is a hallmark of hackers who—despite their mystique in popular culture—are basically everyday thieves, like bank robbers. Where hackers are different, however, is that they rarely meet in person. Instead, they convene in online forums on the “dark web,” an anonymous layer of the Internet that requires a special browser to access. Deep in the forums, crooks hatch hacking plots of all sorts: breaking into corporate databases or selling stolen Social Security numbers or purchasing inside information from unscrupulous employees. Cybercriminals have proved adept at adopting successful corporate strategies of their own. A recent development has seen the cleverest crooks selling hacking tools to criminal small-fry. It’s analogous to semiconductor companies licensing their technology to device manufacturers. According to a report from security software giant Symantec, gangs now offer so-called ransomware as a service, a trick that involves licensing software that freezes computer files until a company pays up. The gangs then take their cut for providing the license to their criminal customers. If it weren’t all blatantly illegal, the practices would be laudably corporate. “Cybercriminals no longer need all the skills to complete any particular crime,” says Nicole Friedlander, a former assistant U.S. Attorney in charge of the key Southern District of New York’s complex fraud and cybercrime unit. “Instead, they can hire other cybercriminals online who have those skills and do it together.” In that sense, hackers have become service providers like doctors or lawyers or anyone else, says Friedlander, who joined the New York office of law firm Sullivan & Cromwell last year. Graphic by Nicolas Rapp But the bad guys aren’t all freelancers. In fact, some of the most sinister hacking outfits operating today are “state-sponsored” groups supported, or at least loosely supervised, by governments. That includes the Russians who are believed to have hacked into the Democratic National Committee last year and the North Korean team credited with unleashing the WannaCry malware as a moneymaking scheme. 3. Playing defense In early March, the information security team at ride-hailing giant Uber leaped into action: An Uber employee had reported a suspicious email message, and similar reports were flooding in from all over the company. Uber’s databases contain the email addresses and personal information of millions of riders around the world, making security a particularly pressing issue. And the company has had its share of problems as a caretaker of sensitive data. In 2014, Uber suffered a breach that exposed the insurance and driver’s license information of tens of thousands of drivers; it took the mega-startup months to discover and investigate the incident and fully notify its drivers. As soon as the alarm was raised in March, Uber established an “incident commander” to manage the developing situation. The job of the incident commander—a term of art in cybersecurity circles—is to keep the company informed about potential attacks. It turned out that the attack was targeting users of Google’s Gmail service, not Uber itself. But anyone with a Gmail address was vulnerable. Later that same day Google fixed the vulnerability in its Gmail service, allowing Uber’s incident commander to stand down. Uber’s reaction is an example of the vigilance with which companies must treat the torrent of threats coming at them every day. John “Four” Flynn, a former Facebook executive who now is chief information security officer for Uber, says the key to cybersecurity incidents—which he defines as everything from a data breach to a stolen laptop—is to have a clear communication strategy. “During an incident, the role of executives is to give support,” says Flynn. “There’s no room for confusion about who’s in charge.” Graphic by Nicolas Rapp Flynn has every right to sound confident in his authority. The chief information security officer, or CISO, is possibly the hottest job in the C-suite today. Cybercrime is so serious that these formerly little-known and unloved executives now typically have a direct line to boards of directors—a big break from the past. Before, the CISO would report to the chief information officer, who was responsible for buying and operating computers, not obsessing over flies in the ointment. If the CISO sounded the alarm over a breach, too often he or she ended up being the one sacrificed to appease top management. “It was my job to tell my boss his baby was ugly,” one former information security executive laments. These days, though, smart companies treat hacking threats like other existential risks to their business—recessions, terrorist attacks, and natural disasters come to mind—and plan accordingly. The CISO is pivotal in maintaining readiness. “If you’re a Fortune 500 company, you already have a response,” says Leek, the former executive at Blackstone, which had several portfolio companies that suffered breaches, including arts-and-crafts merchant Michaels Stores. “But people forget to take it out, blow the dust off, and recall: ‘Let’s do what we decided when we had a sound mind.’ ” Having a clear line of authority and a good action plan take a company only so far. At some point it has to call the cops, specifically the Federal Bureau of Investigation or the U.S. Secret Service. Both agencies have reach and power that allow them to take the fight to foreign cybercrooks. On several occasions, U.S. law enforcement agents working undercover on the dark web have managed to lure presumed offenders out of hiding with phony deals, and then had them apprehended in and extradited to the U.S. During the incident, the role of executives is to give support,” says Uber’s chief information officer. “There’s no room for confusion about who’s in charge.” Calling law enforcement has downsides, however. The likely outcome—an investigation—imposes burdens on the victim company in terms of money and time. And it increases the chance that sensitive details about the hack will leak publicly. That’s why the best course of action is for companies to avoid FBI-level hacking incidents in the first place. A new, multibillion-dollar industry has sprung up to help. 4. An industry is born The videoconference camera looked like any other. But unbeknownst to its corporate owner, the device was working overtime: Hackers had captured the microphone remotely and were using it to spy on every meeting that took place in the boardroom. The company, which does not want to be identified, finally got wise to the spying scheme thanks to Darktrace, a global cybersecurity company that uses artificial intelligence to detect aberrant activity on client networks. Darktrace CEO Nicole Eagan says her company noticed the camera had been gobbling abnormal amounts of data. This raised a red flag, enabling Darktrace to notify its client that something was amiss. Darktrace is just one of hundreds of firms that offer help to combat the hacking epidemic. Once a stodgy corner of enterprise software, cybersecurity has become a hot sector for venture capitalists. Investors put some $3.5 billion into a total of 404 security startups last year, according to New York research firm CB Insights. That’s up from $1.8 billion for 279 investments in 2013. Graphic by Nicolas Rapp For executives, all of this entrepreneurial activity translates into a dizzying array of security options. There are newcomers like Tanium, for instance, which offers a service that lets companies see who is on their network. Publicly traded Palo Alto Networks makes a kind of intelligent firewall that uses machine learning to thwart intruders. There are also a host of niche security firms such as Area 1 (which specializes in defending against phishing scams) and Lookout (which is a mobile-phone-focused security service). With all of this firepower arrayed against it, how can cybercrime continue to grow so fast? One answer is that some of the glitzy defense systems don’t work as advertised. Security insiders grumble about firms bamboozling clients with “blinky lights” in order to sell “scareware”—software that plays to customers’ insecurities but doesn’t protect them. At the end of the day, though, humans are as much to blame as software. “The weak underbelly of security is not tech failure but poor process implementation or social engineering,” says Asheem Chandna, an investor with Greylock Partners and a Palo Alto Networks director. Chandna notes that most hacking attacks come about in two ways, neither of which involves a high level of technical sophistication: An employee clicks on a booby-trapped link or attachment—perhaps in an email that appears to be from her boss—or someone steals an employee’s log-in credentials and gets access to the company network. While cyberdefense tools can mitigate such attacks, some will always succeed. Humans are curious creatures and, in a big organization, there will always be someone who clicks on a message like, “Uh-oh. Did you see these pictures of you from the office party?” When it comes to hacking, a penny of offense can defeat a dollar’s worth of defense. That’s why the fight against hacking promises to be a never-ending battle. Source: https://fortune.com/2017/06/22/cybersecurity-business-fights-back/ 
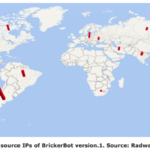 Canada is among the countries that have been stung by a mysterious botnet infecting Internet-connected devices using the Linux and BusyBox operating systems that essentially trashes the hardware, according to a security vendor. Called a Permanent Denial of Service attack (PDoS) – also called “plashing” by some – the attack exploits security flaws or misconfiguration and goes on to destroy device firmware and/or basic functions of a system, Radware said in a blog released last week. The first of two versions has rendered IoT devices affected into bricks, which presumably is why the attack has been dubbed the BrickerBot. A second version goes after IoT devices and Linux servers. “Over a four-day period, Radware’s honeypot recorded 1,895 PDoS attempts performed from several locations around the world,” the company said in the blog. “Its sole purpose was to compromise IoT devices and corrupt their storage.” After accessing a device by brute force attacks on the Telnet login, the malware issues a series of Linux commands that will lead to corrupted storage, followed by commands to disrupt Internet connectivity, device performance, and the wiping of all files on the device. Vulnerable devices have their Telnet port open. Devices tricked into spreading the attack — mainly equipment from Ubiquiti Networks Inc. including wireless access points and bridges with beam directivity — ran an older version of the Dropbear secure shell (SSH) server. Radware estimates there are over 20 million devices with Dropbear connected to the Internet now which could be leveraged for attacks. Targets include digital video cameras and recorders, which have also been victimized by the Mirai or similar IoT botnets. According to Radware, the PDoS attempts it detected came from a limited number of IP addresses in Argentina, the U.S., Canada, Russia, Iran, India, South Africa and other countries. Two versions of the bot were found starting March 20: Version one, which was short-lived and aimed at BusyBox devices, and version two, which continues and has a wider number of targets. While the IP addresses of servers used to launch the first attack can be mapped, the more random addresses of servers used in the second attack have been obscured by Tor egress nodes. The second version is not only going after IoT devices but also Unix and Linux servers by adding new commands. What makes this botnet mysterious is that it wipes out devices, rather than try to assemble them into a large dagger that can knock out web sites – like Mirai. “BrickerBot 2 is still ongoing,” Pascal Geenens, a Radware security evangelist based in Belgium, said in a phone interview this morning. “We still don’t have an idea who it is because it’s still hiding behind the Tor network.” “We still have a lot of questions like where was it originating from, what is the motivation? One of them could be someone who’s angry at IoT manufacturers for not solving that [security] problem, maybe somebody who suffered a DDoS attack and wants to get back at manufacturers by bricking the devices. That way it solves the IoT problem and gets back at manufacturers. “Another idea that I have is maybe its a hacker that is running Windows-based botnets, which are more costly to maintain.” It’s easy to inspect and compromise an IoT device through a Telnet command, he explained, so IoT botnet are easy to assemble. That lowers the cost for a botnet-for-hire. By comparison Windows devices have to be compromised through phishing campaigns that trick end users into downloading binaries that evade anti-virus software. It’s complex. So Geenens wonders if a hacker’s goal here is to get into IoT botnets and destroy the devices, which then raises the value of his Windows botnet. Another theory is the attacker is searching for Linux-based honeypots — traps set by infosec pros — with default passwords. He also pointed out Unix or Linux-based servers with default credentials are vulnerable to the BrickerBot 2 attack. However, he added, there wouldn’t be many of those because during installation process Linux ask for creation of a root password, so there isn’t a default credential. The exception, he added, is a pre-installed image downloaded from the Internet. Administrators who have these devices on their networks are urged to change factory default credentials and disable Telnet access. Network and user behavior analysis can detect anomalies in traffic, says Radware. Source: http://www.itworldcanada.com/article/canada-one-of-sources-for-destructive-iot-botnet/392242
Canada is among the countries that have been stung by a mysterious botnet infecting Internet-connected devices using the Linux and BusyBox operating systems that essentially trashes the hardware, according to a security vendor. Called a Permanent Denial of Service attack (PDoS) – also called “plashing” by some – the attack exploits security flaws or misconfiguration and goes on to destroy device firmware and/or basic functions of a system, Radware said in a blog released last week. The first of two versions has rendered IoT devices affected into bricks, which presumably is why the attack has been dubbed the BrickerBot. A second version goes after IoT devices and Linux servers. “Over a four-day period, Radware’s honeypot recorded 1,895 PDoS attempts performed from several locations around the world,” the company said in the blog. “Its sole purpose was to compromise IoT devices and corrupt their storage.” After accessing a device by brute force attacks on the Telnet login, the malware issues a series of Linux commands that will lead to corrupted storage, followed by commands to disrupt Internet connectivity, device performance, and the wiping of all files on the device. Vulnerable devices have their Telnet port open. Devices tricked into spreading the attack — mainly equipment from Ubiquiti Networks Inc. including wireless access points and bridges with beam directivity — ran an older version of the Dropbear secure shell (SSH) server. Radware estimates there are over 20 million devices with Dropbear connected to the Internet now which could be leveraged for attacks. Targets include digital video cameras and recorders, which have also been victimized by the Mirai or similar IoT botnets. According to Radware, the PDoS attempts it detected came from a limited number of IP addresses in Argentina, the U.S., Canada, Russia, Iran, India, South Africa and other countries. Two versions of the bot were found starting March 20: Version one, which was short-lived and aimed at BusyBox devices, and version two, which continues and has a wider number of targets. While the IP addresses of servers used to launch the first attack can be mapped, the more random addresses of servers used in the second attack have been obscured by Tor egress nodes. The second version is not only going after IoT devices but also Unix and Linux servers by adding new commands. What makes this botnet mysterious is that it wipes out devices, rather than try to assemble them into a large dagger that can knock out web sites – like Mirai. “BrickerBot 2 is still ongoing,” Pascal Geenens, a Radware security evangelist based in Belgium, said in a phone interview this morning. “We still don’t have an idea who it is because it’s still hiding behind the Tor network.” “We still have a lot of questions like where was it originating from, what is the motivation? One of them could be someone who’s angry at IoT manufacturers for not solving that [security] problem, maybe somebody who suffered a DDoS attack and wants to get back at manufacturers by bricking the devices. That way it solves the IoT problem and gets back at manufacturers. “Another idea that I have is maybe its a hacker that is running Windows-based botnets, which are more costly to maintain.” It’s easy to inspect and compromise an IoT device through a Telnet command, he explained, so IoT botnet are easy to assemble. That lowers the cost for a botnet-for-hire. By comparison Windows devices have to be compromised through phishing campaigns that trick end users into downloading binaries that evade anti-virus software. It’s complex. So Geenens wonders if a hacker’s goal here is to get into IoT botnets and destroy the devices, which then raises the value of his Windows botnet. Another theory is the attacker is searching for Linux-based honeypots — traps set by infosec pros — with default passwords. He also pointed out Unix or Linux-based servers with default credentials are vulnerable to the BrickerBot 2 attack. However, he added, there wouldn’t be many of those because during installation process Linux ask for creation of a root password, so there isn’t a default credential. The exception, he added, is a pre-installed image downloaded from the Internet. Administrators who have these devices on their networks are urged to change factory default credentials and disable Telnet access. Network and user behavior analysis can detect anomalies in traffic, says Radware. Source: http://www.itworldcanada.com/article/canada-one-of-sources-for-destructive-iot-botnet/392242