Alongside the report, Trustwave is reporting the discovery of DIY DDoS kits for sale from just US$ 200 (£118) and which give users – apart from a high bandwidth connection – all they need to stage a wide-scale attack. The analysis – from Prolexic Technologies, now part of Akamai – claims to show that distributed denial of service activity has surged by 22 percent over the last quarter, putting levels close to those seen in Q1 of this year, when existing DDoS volume and allied records were broken. Delving into the report reveals there was a 72 percent increase in the average bandwidth of attacks during the second quarter, along with a shift to reflection-based attacks that undermine common web protocols, as well as the arrival of server-side botnets that exploit web vulnerabilities in Windows and Linux-based systems. The analysis concludes that there have been shifts in the industry targets compared with last quarter’s DDOS activity. The difference in these numbers, says the report, may be due to the different types of malicious actors on the Internet that may be active at any particular time. “It is clear that the majority of malicious actors preferred to use of volumetric attacks in Q2 – this trend was seen across all verticals. A significant variant in attack vectors by industry was the use of a very sophisticated botnets against financial and media sites,” notes the report, adding that these attacks do not seem to fit the previous patterns and motives of the DDoS criminal ecosystem. According to Trustwave, meanwhile, its research has revealed that hackers are now selling the Neutrino Bot malware kit, which it can be used to infect a large number of computers, create a botnet, and launch DDoS attacks against websites and services at will. For US$ 500 (£294), meanwhile, hackers will sell all comers BetaBot 1.6, which Trustwave says is a remote access Trojan that can run DDoS attacks, and steal sensitive data, passwords and files from infected systems. Karl Sigler, Trustwave’s threat intelligence manager, said he was unsurprised by the findings. “Supply and demand affects malware markets like they do any market. Even though demand is high, there is an increasing amount of malware competing with each other and this helps drive down the cost. There is also a cost-benefit issue. Criminals look at how much they can make by selling stolen data acquired using the malware. Finally, age plays a role. The longer malware is on the market, the cheaper it tends to get,” he said. Rob Bamforth, a principal analyst with Quocirca, the business analysis and research house, said that the surge in volumes and incidences of DDoS attacks in the second quarter identified by Akamai suggests a larger number of servers being infected by cyber-criminals – coupled with the fact that that many systems `out there’ are Windows XP-based, which has become a legacy operating system since it reached end-of-life with Microsoft back in April. “It also suggests there is a degree of complacency in the business sector, with many managers saying they do not want to invest extra money in IT security, as they do not see a return. Many businesses are suffering an ongoing squeeze on costs, so a failure to invest in security is understandable, even if it is not the correct approach to take,” he told SCMagazineUK.com . Nick Mazitelli, a senior consultant with Context Information Security, meanwhile, said that Akamai’s analysis that the widespread dissemination of increasingly capable attacker toolsets is a trend we see right across the threat landscape, from cyber-crime through to state-sponsored attacks and everything in between. “On the one hand this trend is fuelled by the on-going professionalisation and commoditisation of criminal marketplaces, and on the other by increasing levels of interconnection between threat groups of all stripes. Not only does this mean that existing threat groups have access to improved capability, but it also lowers the barrier of entry for newcomers thereby increasing the number of malicious parties active in the landscape – both factors that unavoidably increase the tempo of what is effectively an arms race between attacker and defender,” he said. “With this increased tempo as background it is important to highlight the necessity of a flexible and adaptable approach to security based on a sound understanding of the threat landscape. In particular those aspects of security concerned with network security monitoring as well as incident response are areas that have often been overlooked in the past, but are critical components of effectively managing the risk and minimising the potential impact of these constantly evolving threats,” he added. Source: http://www.scmagazineuk.com/ddos-attacks-grow-as-first-diy-kits-emerge/article/362573/
Excerpt from:
DDoS attacks grow as first DIY kits emerge


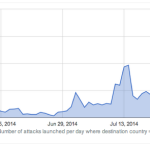 As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9
As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9 
 Hacker collective Anonymous has announced that it has taken down over a thousand of crucial Israeli websites in a huge new coordinated cyber-attack called #OpSaveGaza on 11 July and 17 July, in support of the people of Palestine. Some of the websites, such as the Tel Aviv Police Department’s online presence, are still offline two days after the distributed denial of service (DDoS) attacks, and numerous Israeli government homepages have been replaced by graphics, slogans, and auto-playing audio files made by AnonGhost, the team of hackers who coordinated the attack. The official Israeli government jobs website has had its homepage replaced by a graphic titled “Akincilar”, which is Turkish for the Ottoman Empire’s troops. Akincilar: A graphic and message protesting against the treatment of Palestinians is still replacing the homepage of certain Israeli government websites A message written in English and Turkish – presumably by Turkish hackers – and accompanied by pictures of Palestinians suffering says: “The Jerusalem cause is Muslims’ fight of honour” and says that people who fight for Palestine are “on the side of Allah”. Another Israeli government website now bears an AnonGhost graphic and lists the usernames of 38 hackers. An audio file that auto-plays when the page loads plays music and a synthesized newsreader clip, together with a message beseeching human rights organisations, hackers and activists to attack Israeli websites to become the “cyber shield, the voice for the forgotten people”. AnonGhost’s #OpSaveGaza message has been displayed on many Israeli websites Many of the websites have since been restored. The hackers have also leaked lists of Israeli government email addresses obtained by hacking websites of the Ministry of Immigrant Absorption, the Ministry of Justice, the Ministry of Culture and Sport, the Ministry of Housing and Construction and much more. Israeli websites belonging to restaurants, local businesses, associations, societies, academic foundations and even a symphony orchestra were also attacked, as well as a subdomain belonging to MSN Israel. A message on the main Pastebin page and some of the hacked websites reads : “The act of launching rockets from Gaza sector to Israhell is an acceptable and normal reaction against those pigs, it’s called Resistance and not terrorism. “Israhell never existed its only Palestine, it’s our home. If you are a Hacker, Activist, a Human Right Organisation then hack israel websites and expose to the world their crimes, show to the world how much blood is on their hands, blood of innocent children and women.” Anonymous has previously run another campaign in April targeting Israeli websites, although on a smaller scale. About 500 websites went offline during the OpIsrael campaign and the hackers released the phone numbers and email addresses of some Israeli officials. Source: http://www.ibtimes.co.uk/opsavegaza-anonymous-takes-down-1000-israeli-government-business-websites-1457269
Hacker collective Anonymous has announced that it has taken down over a thousand of crucial Israeli websites in a huge new coordinated cyber-attack called #OpSaveGaza on 11 July and 17 July, in support of the people of Palestine. Some of the websites, such as the Tel Aviv Police Department’s online presence, are still offline two days after the distributed denial of service (DDoS) attacks, and numerous Israeli government homepages have been replaced by graphics, slogans, and auto-playing audio files made by AnonGhost, the team of hackers who coordinated the attack. The official Israeli government jobs website has had its homepage replaced by a graphic titled “Akincilar”, which is Turkish for the Ottoman Empire’s troops. Akincilar: A graphic and message protesting against the treatment of Palestinians is still replacing the homepage of certain Israeli government websites A message written in English and Turkish – presumably by Turkish hackers – and accompanied by pictures of Palestinians suffering says: “The Jerusalem cause is Muslims’ fight of honour” and says that people who fight for Palestine are “on the side of Allah”. Another Israeli government website now bears an AnonGhost graphic and lists the usernames of 38 hackers. An audio file that auto-plays when the page loads plays music and a synthesized newsreader clip, together with a message beseeching human rights organisations, hackers and activists to attack Israeli websites to become the “cyber shield, the voice for the forgotten people”. AnonGhost’s #OpSaveGaza message has been displayed on many Israeli websites Many of the websites have since been restored. The hackers have also leaked lists of Israeli government email addresses obtained by hacking websites of the Ministry of Immigrant Absorption, the Ministry of Justice, the Ministry of Culture and Sport, the Ministry of Housing and Construction and much more. Israeli websites belonging to restaurants, local businesses, associations, societies, academic foundations and even a symphony orchestra were also attacked, as well as a subdomain belonging to MSN Israel. A message on the main Pastebin page and some of the hacked websites reads : “The act of launching rockets from Gaza sector to Israhell is an acceptable and normal reaction against those pigs, it’s called Resistance and not terrorism. “Israhell never existed its only Palestine, it’s our home. If you are a Hacker, Activist, a Human Right Organisation then hack israel websites and expose to the world their crimes, show to the world how much blood is on their hands, blood of innocent children and women.” Anonymous has previously run another campaign in April targeting Israeli websites, although on a smaller scale. About 500 websites went offline during the OpIsrael campaign and the hackers released the phone numbers and email addresses of some Israeli officials. Source: http://www.ibtimes.co.uk/opsavegaza-anonymous-takes-down-1000-israeli-government-business-websites-1457269