Hacktivist for Operation Hacking Cup #OpHackingCup took down the Brazil World Cup site and have targeted hundreds of other sites. This was not the first time a major event has been targeted nor will it be the last. Hacktivist have been actively leveraging Distribute Denial of Service (DDoS) attacks as a way to successfully highlight and protest against political, economic or ideological conflicts for quite some time. It has become so mainstream there was even a petition to the Obama administration to make DDoS legal. The FFIEC recently issued guidance to financial institutions with a quick guide on mitigation techniques. Techniques used by cybercriminals to conduct attacks have become increasingly sophisticated – from single point denial of service attacks on networks to distributed denial of service beyond focusing just on Layer 7. In fact, DDoS has become so commercial that we’ve seen DDoS for hire underground offerings for as low as $7 per hour with free one hour try before you buy option. Couple this with a recent Ponemon report which highlighted that one hour of downtime for a merchant would equate to an average loss of $500,000 – what an amazing ROI for cybercriminals considering for the same amount of money I spend on coffee a day they can impact an organization’s bottom line by over $500,000! Traditional DDoS attacks focused on things like UDP Flood, Syn Flood and ICMP Flood targeting network resource exhaustion . Modern day DDoS attacks such as Op Ababil, target the HTTP layer and above. In recent DDoS attacks, reflection and amplification have been the weakness of choice such as the Network Time Protocol (NTP) attacks this past February or the DNS lookup attacks late last year. Cybercriminals continue to develop even more sophisticated botnets which can remain active longer before being discovered and they are hosting a botnet’s command-and-control center in a Tor-based network (where each node adds a layer of encryption as traffic passes) obfuscates the server’s location and makes it much harder to take it down. Additionally, cybercriminals are building more resilient peer-to-peer botnets, populated by bots that talk to each other, with no central control point. If one bot (or peer) in a peer-to-peer botnet goes down, another will take over, extending the life of the botnet using business continuity techniques. This is exactly what we saw with the recent GameOver Zeus and CryptoLocker botnet disruption. These types of attacks make requests that are perceived to be legitimate; like attempting logins, performing search or downloading large files repeatedly which can easily bypass standard DDoS defenses such as firewalls, Intrusion Prevention Systems (IPS) and Web Application Firewalls (WAF). Additionally, modern day DDoS attacks are starting to abuse a business logic flaws rather than network resources on a more frequent basis as few organizations are focused on that aspect of their site for security detection. This is why it is becoming more critical to determine whether a request is legitimate or not and without understanding business logic used for processing the request this is incredibly challenging. In addition to what you are already doing today, you should consider focusing on the detection of business logic abuse by analyzing the behavior of users. You can achieve this by tracking every user/IP including pages accessed, the order of accesses, how quickly they moved between pages and other web paths taken by the same IP address. Further, if you analyze all web traffic it makes it possible to identify users or IP addresses displaying similar behavior. Users can then be clustered based on behavior enabling your administrators to find all endpoints involved in the attack. If this analysis happens in real-time you can identify more attackers as attacks happen. Take a look at what we saw with one of our Web Threat Detection customers. In a world where we will always have political, economic or ideological conflicts – and major sporting event, we should assume there will always be some type of cyber attack in parallel. What is your game plan to defeat your competition? Source: https://blogs.rsa.com/world-cup-ddos-attacks/?utm_source=rss&utm_medium=rss&utm_campaign=world-cup-ddos-attacks
Read this article:
The World Cup of DDoS Attacks


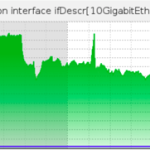 DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.
DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal. 
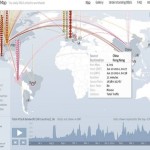 Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/
Just days before a citizen-led online referendum on voting rights, the technical platform that advocates had planned to use for the referendum suffered a massive DDoS attack. From June 20-22, citizens will be invited to vote on a referendum on constitutional reforms that would guarantee all citizens the right to vote in elections that determine who will be the city’s Chief Executive. To build a public consensus around a recent civil proposal on universal suffrage, the civic group “Occupy Central with Love and Peace” appointed the Public Opinion Programme at Hong Kong University and the Center for Social Policy Studies at the Hong Kong Polytechnic University to host the civil referendum on their servers. On June 13, 30 hours after HKU’s Public Opinion Programme (POP) tested their online system by accepting voter pre-registrations, the system endured the largest distributed denial of service attack in its history. Two of their hosting providers have since withdrawn their service for the project. The civil referendum has been criticized by pro-Beijing political groups, sparking controversy concerning channels for nomination. Many Hong Kongers feel that political party nomination and nomination by a nominating committee serve as a filtering mechanism for eliminating candidates who are undesirable for Beijing. According to a press release issued by HKU POP on June 16, the voting system is hosted by Amazon Web Services (AWS), Cloudflare and UDomain. All three web hosting services suffered from large scale DDoS attacks on June 14 and 15. AWS recorded 10 billion system requests with 20 hours, CloudFare recorded a 75Gb DDoS per second and UDomain 10Gb per second. As the scale of attack is tremendous, all three service providers were forced to temporarily suspend their services. An expert estimated that there could be at least 5,000 but possibly more than 10,000 computers involved in the attack. On June 16, Amazon decided to stop providing DNS hosting service to HKU POP and UDomain withdrew its security protection service. Cloudflare is now the only service provider to support the voting system. IT security expert Anthony Lai posted digital attack maps on his Facebook page, comparing the attack scale between June 10 and June 14 (see top), before and after HKU POP tested the voting system: Digital Attack Map on June 10. Destination Hong Kong. HKU POP is working on a solution to the voting system’s vulnerability. They are considering to using 125 telephone lines for voting, but this will not be able to accommodate the expected 70,000 votes in 12 hours. In 2012, the HKU POP was also attacked by DDoS when it hosted a mock universal suffrage poll for the chief executive election. Source: http://advocacy.globalvoicesonline.org/2014/06/17/hong-kong-voting-site-suffers-massive-ddos-attack-before-civil-referendum/