In taking a stand and making a direct protest against the death sentence handed in 2012 to a 17-year old teenager Mohammed al-Nimr, Anonymous has crippled multiple Saudi Arabian government websites. It is a case described as “a possible breach of international law,” by a group of UN human rights experts. Ali Mohammed al-Nimr was arrested and sentenced to death after being accused of partaking in pro-democracy demonstrations during the Arab Spring of 2012. At the time, Nimr was 17. In joining the international outcry against the sentence of execution by beheading and crucifixion, hacktivist group Anonymous has taken down multiple Saudi Government websites with an operation called #OpNimr. The hashtag has since gone viral and adopted by activists around the world. #OpNimr Anonymous announced #OpNimr by inundating government websites with DDoS attacks and taking them offline, along with the following video that demanded the release of Nimr. The statement released on the video said: Ali Mohammed al-Nimr, an innocent young teenage boy has been sentenced to death in Saudi Arabia and we will not stand by and watch. “Hundreds of innocent people die each year because of the Saudi Government, and they (the Saudi Government) will now be punished for their actions,” Anonymous said. Nimr’s final appeal against his execution was dismisbsed by Saudi courts in September 2014 for his part in attending a rally during the Arab Spring. At the time, a Saudi court judgement read: “[Nimr] encouraged pro-democracy protests [using] a Blackberry.” “Naturally, the sentence was appealed but the appeal hearing was held in secret and apparently dismissed,” added Anonymous in their video message. A second video was released by Anonymous days after their first, this time directly addressing King Salman and the Saudi Arabian Government. “13 judges have already approved the death sentence of Ali Mohammed al-Nimr, meaning only King Salman bin Abdulaziz Al Saud has to approve it,” Anonymous said. We cannot and will not allow this to happen. The Ministry of Justice was taken offline a few days ago, and we will continue to do this to other government websites. Some of the websites taken down include: The Ministry of Justice (saudinf.com) The Ministry of Civil Service (mcs.gov.sa) The General Administration of Education (tabukedu.gov.sa) Saudi Airlines (saudiairlines.com) A complete list of the targeted websites has been published by Anonymous in Pastebin, here. “We hope you listen to us this time and release the young man. You will be treated as a virus, and we are the cure,” concluded Anonymous in their statement. Several activist groups and human rights groups including Amnesty International have claimed that Nimr was not granted the means to a lawyer and that he was forced into signing a “confession” after suffering torture by prison officers. At the time, a Saudi court judgement read: [Nimr] encouraged pro-democracy protests [using] a Blackberry. Amnesty International recently released a report that proclaims Saudi Arabia as “one of the most prolific executioners in the world.” Between January 1986 and June 2015, at least 2,200 known people were executed, half of whom were foreign nationals. Executions were carried out for “crimes” such as witchcraft, sorcery and adultery. According to news reports, Saudi Arabia will imminently behead and then crucify Al Nimr, now 20, today or later this week. Source: https://hacked.com/anonymous-attacks-several-saudi-arabian-websites-brings-focus-teens-execution-opnimr/
Tag Archives: dos attacks
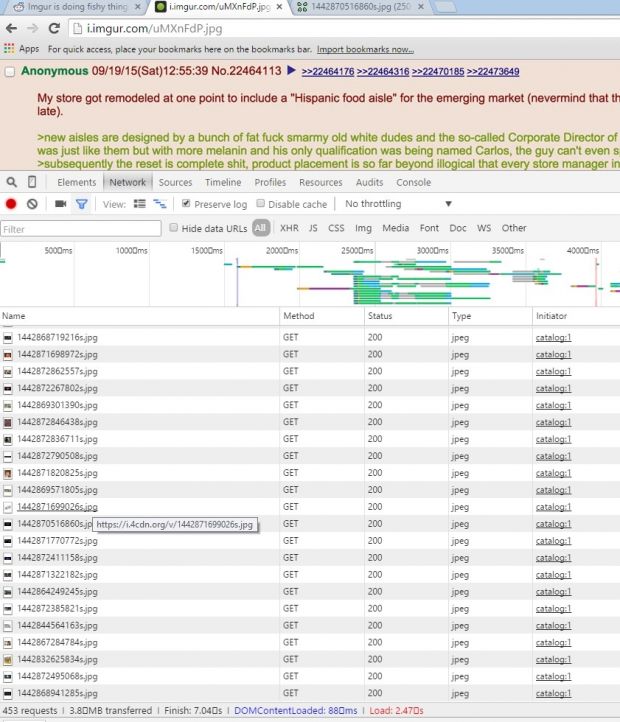
Hackers Used Imgur to Launch DDoS Attacks on 4chan
 A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml
A Reddit user has uncovered a covert method of carrying DDoS attacks on 4chan’s infrastructure using images hosted on Imgur, via Reddit. According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan’s CDN. Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan’s servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well. Malicious code was being loaded with Imgur images Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there. This code secretly stored the “axni” variable in the browser’s localStorage, which was set to load another JavaScript file from “4cdns.org/pm.js.” This is not 4chan’s official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime. When refreshing the original image that loaded the “axni” variable, the malicious code would not be loaded again, a measure taken to avoid detection. Additionally, also to avoid detection, the JS file stored on “4cdns.org/pm.js” could not be loaded directly in the browser. Loading 500+ 4chan images inside a hidden iframe Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user’s view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file. Imgur was contacted about this issue, and fixed it on the same day. “Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” said the Imgur team. “From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.” It’s a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways. Source: http://news.softpedia.com/news/hackers-used-imgur-to-launch-ddos-attacks-on-4chan-492433.shtml
See the original post:
Hackers Used Imgur to Launch DDoS Attacks on 4chan
Prepare a new dossier! Pakistan’s cyber Mujahideen hit India
A month before Pakistan’s ceasefire violation on the eve of Independence Day, a silent battle was raging in Mumbai’s financial district. Two large private banks, a retail brokerage and a state-owned lender faced a cyberattack from hackers across the border that seriously slowed down all online customer transactions. In the world of cybercrime, such attacks, which could be mistaken as normal traffic overload on the Net, are known as ‘distributed denial of service’ or DDoS. Spread across the world, hackers, either sympathetic to lost causes or indulging in the game of extortion, virtually ‘take over’ thousands of computers in diverse destinations before unleashing a DDoS strike. As computers that are hacked into start behaving as robots – or, ‘botnet’ in cyberparlance, the hackers divert traffic from these terminals to clog the systems of targets like banks and even e-commerce firms. A bank that is invaded may be unaware of the attack and even take a while to sense that customers are struggling to put through a simple net banking fund transfer or credit card payment. The July attack On that day in July, it was no different. The financial institutions received advisory on the DDoS attack from the government’s Computer Emergency Response Team (CERT). Also, there were alerts that more attacks could follow over the next few hours, said a cybercrime expert. Speaking to ET on condition of anonymity , one of the senior most officials in the government’s cybersecurity establishment said, “There was an attack but this was effectively countered. Often these things are done with the intention to blackmail … But we have the systems to handle it. There have been finance ministry and RBI instructions to banks for taking necessary measures to protect against DDoS strikes.” According to cybersecurity head in one of the largest Indian banks, since April there have been several advisories from government agencies like CERT and National Critical Information Infrastructure Protection Centre on DDoS. “In a DDoS attack, if a bank can block the bogus traffic diverted by a hacker for the first 15 minutes, then the attacker typically moves away to a weaker target. But if an institution is unable to resist, then the attacker may demand ransom. Rogue hackers in places like Nigeria and East Europe want to be paid in Bitcoin. Since Bitcoin is based on what is known as block-chain technology, fund transfers leave no trail.” Safety measures As precaution, no bank, to begin with, should depend on a single internet service provider (ISP), he said. “Besides, banks are beginning to invest in anti-DDOS high-end appliances. Some are carrying out mock drills to test the technology. Here, a flood of traffic is diverted to banks’ own websites to figure out whether the ISP and banks’ internal cybersecurity teams are adequately alert,” said the banker who refused to be named. Until a hack attack is obvious, companies in India typically keep such incidents under wrap as regulators do not insist on mandatory reporting of security breach. Some of the US-listed Indian entities are even more reticent: Since a cyberattack is rarely disclosed due to fear that it could scare away customers, it becomes more difficult to admit the breach later. In DDoS attack, including the current one, there is no data compromise or cash theft. “The timing of the event suggests that it could be handiwork of some of the Pakistani hackers who may be located in the US and Europe. Typically, they are active before big festivals or in the run up to Independence Day or Republic Day. They have a specific point to prove,” said an ethical hacker, who advises several companies and agencies on cybersecurity . Types of hackers According to him, there are three broad types of hackers, differentiated by motives. First, the financially motivated cybercriminal, who are usually from Eastern Europe and are interested in stealing credit card information, or engage in identity theft etc. They are highly organized, infect thousands of systems across the globe in order to achieve their objectives, and even ‘rent’ access to an infected computer for an hourly fee for conducting DDoS. The second type are hacktivists or politically motivated hackers whose sole interest is in furthering a political agenda by defacing a site, or bringing a site down through DDoS attacks. Pakistani hackers fall in this category . The third and the most serious type are nation state attackers involved in corporate espionage. They gain access to competing companies in order to steal business strategy and intellectual property. Chinese hackers are well-known for this. Source: http://timesofindia.indiatimes.com/tech/tech-news/Prepare-a-new-dossier-Pakistans-cyber-Mujahideen-hit-India/articleshow/48739013.cms?
View post:
Prepare a new dossier! Pakistan’s cyber Mujahideen hit India
DDoS attacks are getting much more powerful and the Pentagon is scrambling for solutions
No wonder the Pentagon has announced it’s working on a plan to fund tools and researchers to help organizations defend themselves against the pervasive threat of cyber assaults known as distributed denial-of-service (DDoS) attacks. In recent days, the agency said it’s looking to fund researchers who can come up with tools as part of a program starting next April that would, among other things, help organizations recover from DDoS attacks in a maximum of 10 seconds. And the acknowledgement of that hunt for researchers for the program, called Extreme DDoS Defense, arguably comes not a moment too soon. A few new industry reports are out that show the number of DDoS attacks is trending upward, even hitting new highs. Their provenance and targets take many forms – from organized, malicious hackers targeting sophisticated organizations to more isolated incidents where, experts say, the intent is to just find a weakness somewhere, anywhere. But the result is a kind of cyber blitz that’s growing in number and aggressiveness. New York Magazine was among those organizations recently hit by a DDoS attack, and at a critical moment. After publishing the blockbuster results of an interview with 35 women who’ve accused Bill Cosby of sexually assaulting them, the magazine’s website was knocked offline by what appeared to be a DDoS attack. Attacks like those, said Incapsula co-founder Marc Gaffan, are not only on the rise but “have essentially been going up for the last two years, quarter over quarter.” His company is a cloud-based application delivery service. According to another cloud services provider, Akamai Technologies, DDoS attacks were up 132% in the second quarter compared to the same period in 2014. During the period between April and June this year, Akamai’s research also found 12 attacks it described as “mega attacks” – which peaked at more than 100 gigabits per second and 50 million packets per second. What’s more, the company said, few organizations are able to mount a strong enough defense to keep attacks like that at bay. “The threat posed by distributed denial of service (DDoS) and web application attacks continues to grow each quarter,” said John Summers, vice president of Akamai’s cloud security business unit. “Malicious actors are continually changing the game by switching tactics, seeking out new vulnerabilities and even bringing back old techniques that were considered outdated.” Once upon a time, Gaffan said, the attacks were largely the work of hackers looking to make a name for themselves, to make some larger point or to go after a controversial target to inflict some degree of discomfort. “They’re also about extortion and ransom,” Gaffan said. “They can be used to stoke competitive feuds, as well as a diversion for a larger attack. When it comes to extortion, attackers are looking online for businesses who’d suffer significantly if their website is down. Most companies don’t pay the ransom. “Often, we also see ransom numbers so small, they try to make it low enough that it’s a no-brainer for organizations to pay. Companies also hire DDoS gangs to take competitors down. There was one organization that came to us and said, ‘We were attacked.’ Two minutes later, a competitor put on Twitter that they were going out of business, and that’s why their site was down.” Such attacks continue to be a costly problem for the organizations that end up as targets. The Q2 2015 Global DDoS Threat Landscape from Incapsula showed, of network layer DDoS attacks, the longest during the quarter lasted 64 days. A little more than 20% of all attacks lasted over five days. The report based its data on 1,572 network layer and 2,714 application layer DDoS attacks on websites using Incapsula services from March 1st through May 7th. According to the organization’s DDoS Impact Survey, an attack on average costs a business $40,000 per hour. Implications include the loss of consumer trust, data theft, intellectual property loss, and more, according to the report. The report went on to note the longest application layer attack it found lasted for eight straight days. The average duration stretched for just over two and a half hours. And in the second quarter, almost 15% of all application layer DDoS traffic came from China, followed by Vietnam, the U.S., Brazil and Thailand. “What is most disconcerting is that many of these smaller assaults are launched from botnets-for-hire for just tens of dollars a month,” the organization’s threat landscape report reads. “This disproportion between attack cost and damage potential is the driving force behind DDoS intrusions for extortion and vandalism purposes.” Meanwhile, Arbor Networks Inc., a provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, found similar results. Its just-released Q2 2015 global DDoS attack data shows growth in the average size of attacks, with 21 percent of attacks during the quarter topping 1 gigabit per second. “One thing we see a lot of is just probing, just hitting the network as hard as they can to see where it will fall down,” said Gary Sockrider, principal security technologist at Arbor. “Another is where this is used for extortion. Where the business model is ok, now we’ve done this – pay us money.” Sockrider continued, “The lesson to take is this isn’t just a service provider problem. It’s no longer sufficient to leave it to deal with upstream. It’s everybody’s problem. You have to understand that threat, that you are a potential target, and bake that into your business resiliency planning.” Source: http://bgr.com/2015/08/31/ddos-attacks-report-2015-trends/
View post:
DDoS attacks are getting much more powerful and the Pentagon is scrambling for solutions
Six teens arrested in UK for using hacking group’s paid DDoS service
Six teenagers were arrested by British police on suspicion of attacking websites, the country’s National Crime Agency (NCA) announced on Friday. The teenagers were users of the hacking group Lizard Squad and used the Lizard Stresser tool, software that allowed them to pay to take websites offline for up to eight hours at a time, according to an NCA statement. The tool works by using Distributed Denial of Service (DDoS) attacks, which flood web servers or websites with massive amounts of data, leaving them inaccessible to users. Those arrested in the operation coordinated by NCA were all teenage boys aged from 15 to 18, while two other suspected users of Lizard Stresser were arrested earlier this year, the NCA said. The suspects are thought to have maliciously deployed Lizard Stresser, having bought the tool using alternative payment services such as Bitcoin in a bid to remain anonymous, the NCA also said. Organizations believed to have been targeted by the suspects include a leading national newspaper, a school, gaming companies, and a number of online retailers, according to the NCA. Lizard Squad became a well-known hacking group last year after it claimed responsibility for taking down the PlayStation Network and Xbox Live. The group later launched the Lizard Stresser tool. “By paying a comparatively small fee, tools like Lizard Stresser can cripple businesses financially and deprive people of access to important information and public services,” said Tony Adams, head of investigations at the NCA’s National Cyber Crime Unit. Officers are also visiting some 50 addresses linked to individuals registered on the Lizard Stresser website, but who are not currently believed to have carried out attacks. A third of the individuals identified are under the age of 20, according to the NCA. “One of our key priorities is to engage with those on the fringes of cyber criminality to help them understand the consequences of cyber crime, and how they can channel their abilities into productive and lucrative legitimate careers,” said Adams. Source: http://www.globalpost.com/article/6638281/2015/08/28/six-teens-arrested-uk-using-hacking-groups-paid-ddos-service
See the original article here:
Six teens arrested in UK for using hacking group’s paid DDoS service
BitTorrent patches reflective DDoS attack security vulnerability
A vulnerability which could divert traffic to launch cyberattacks has been mitigated two weeks after public disclosure. BitTorrent has taken rapid steps to mitigate a flaw which could divert user traffic to launch reflective DDoS attacks. The flaw, reported by Florian Adamsky at the USENIX conference in Washington, D.C., affects popular BitTorrent clients such as uTorrent, Mainline and Vuze, which were known to be vulnerable to distributed reflective denial-of-service (DRDoS) attacks. According to the researchers from City University London, BitTorrent protocols could be exploited to reflect and amplify traffic from other users within the ecosystem — which could then be harnessed to launch DRDoS attacks powered up to 120 times the size of the original data request. Successful distributed denial-of-service (DDoS) and DRDoS attacks launched against websites flood domains with traffic, often leaving systems unable to cope with the influx and resulting in legitimate traffic being denied access to Web resources. The team said in a paper (.PDF) documenting the vulnerability that BitTorrent protocols Micro Transport Protocol (uTP), Distributed Hash Table (DHT), Message Stream Encryption (MSE) and BitTorrent Sync (BTSync) are exploitable. On Thursday, Vice President of Communications at BitTorrent Christian Averill said in a blog post no attack using this method has been observed in the wild and as the researchers informed the BitTorrent team of the vulnerability ahead of public disclosure, this has given BitTorrent the opportunity to “mitigate the possibility of such an attack.” Francisco De La Cruz, a software engineer from the uTorrent and BitTorrent team, wrote a detailed analysis of the attack and the steps the company has taken to reduce the risk of this vulnerability. The vulnerability lies within libµTP, a commonly used tool which can detect network congestion and automatically throttle itself — a useful feature when BitTorrent clients are being used on home networks. However, the way libµTP handles incoming connections allows reflectors to accept any acknowledgement number when receiving a data packet, which opens the doorway to traffic abuse. The success of a DRDoS relies on how much traffic an attacker can direct towards a victim, known as the Bandwidth Amplification Factor (BAF). The higher the BAF, the more successful the attack. In order to reduce the BAF ratio and mitigate the security issue, BitTorrent engineers have ensured a unique acknowledgement number is required when a target is receiving traffic. While this can still be guessed, it would be difficult and time-consuming to do so for a wide pool of victims. De La Cruz said: “As of August 4th, 2015 uTorrent, BitTorrent and BitTorrent Sync clients using libµTP will now only transition into a connection state if they receive valid acknowledgments from the connection initiators. This means that any packets falling outside of an allowed window will be dropped by a reflector and will never make it to a victim. Since the mitigation occurs at the libµTP level, other company protocols that can run over libµTP like Message Stream Encryption (MSE) are also serviced by the mitigation.” Regarding BTSync, BitTorrent says the severity of the vulnerability — even before recent updates were applied to the protocol — mitigated the risk of this vulnerability. In order to exploit the security weakness, an attacker would have to know the Sync user, identifiers would have to be made public, and the protocol’s design ensures that peers in a share are limited — keeping the potential attack scale down. According to the BitTorrent executive, the protocol therefore would “not serve as an effective source to mount large-scale attacks.” Averill commented: “This is a serious issue and as with all security issues, we take it very seriously. We thank Florian for his work and will continue to both improve the security of these protocols and share information on these updates through our blog channels and forums.” Source: http://www.zdnet.com/article/bittorrent-patches-reflective-ddos-attack-security-vulnerability/
Read the original post:
BitTorrent patches reflective DDoS attack security vulnerability
Teen nabbed after attacks on UK government and FBI sites
His lawyers claim that their client was only on the “periphery” of a conspiracy to take down UK government and FBI sites, but a UK teen who didn’t mind boasting online about those crimes now faces the possibility of jail time. Charlton Floate, 19, of Solihull, England, already admitted to three counts of computer misuse under the Computer Misuse Act and three counts of possessing prohibited images at Birmingham Crown Court. The attacks took place in January 2013, when Floate and a team of other cyber criminals crippled government sites with deluges of digital traffic sent from malware-infected computers. Such computers are often called zombie computers, and they’re widely used in botnets to gang up on sites with what’s known as a distributed denial of service (DDoS) attack. The gang managed to knock out the UK’s Home Office site – a heavily used site that provides information on passports and immigration among other things – for 83 minutes. The group also took down an FBI site – that allowed users to report crime – for over five hours. The prosecutor, Kevin Barry, reportedly said that in November 2012, Floate carried out two test runs, remotely attacking the computers of two men in the US. Floate uploaded a sexually explicit video to YouTube to “mock and shame” one of his victims, and he “taunted” the other victim about having control of his computer. Modest, he was not – Floate also reportedly bragged about the government site attacks on Twitter and on a forum frequented by hackers. Judicial officer John Steel QC rejected Floate’s legal team’s contention that he was on the “periphery” of the cyber gang, saying that evidence pointed to his actually being central to the crimes, including organizing the attacks. He said Floate was “clearly a highly intelligent young man”, who had become an expert in computer marketing, had written a book on the subject, and succeeded in taking down an FBI.gov website – what he called the “Holy Grail” of computer crime: A successful attack on the FBI.gov website is regarded by hackers as the Holy Grail of hacking. It was this which he attempted and, indeed, achieved. He was the person who instituted such attacks and assembled the tools and personnel for doing so. The Holy Grail it may be but in this case I beg to differ about how successful Floate was in getting his hands on it. A DDoS attack isn’t a form of sophisticated lock picking, it’s just a noisy way to board the door shut from the outside. Floate may well be bright but he stumbled once, and that’s all that investigators needed. Namely, he used his own IP address – he worked out of his mother’s home – to check up on how the attacks had gone. Police traced the address to Floate’s mother’s home, where they seized Floate’s computer and mobile phone. They also found evidence that he’d tried to recruit others into the gang and that he’d discussed possible weaknesses in certain websites as well as potential future targets – including the CIA and The White House. Sentencing was adjourned until 16 October, pending a psychiatric report. Floate is currently remanded on conditional bail. Steel said he hadn’t yet made up his mind about sentencing but added there’s “clearly potential for an immediate custodial sentence” and that Floate “should be mentally prepared for it.’ Source: https://nakedsecurity.sophos.com/2015/08/24/teen-nabbed-after-attacks-on-uk-government-and-fbi-sites/
Read more here:
Teen nabbed after attacks on UK government and FBI sites
Ziggo suffers new DDoS attack
Dutch cable operator Ziggo has experienced network problems for a second time in a week, following a DDoS attack. Service disruptions were experienced throughout the country, and Ziggo said around 60 percent of its customers were affected, NU.nl reports. A Ziggo spokesman said the latest attack was worse than the first. The attack targeted Ziggo’s DNS servers, leaving many customers without internet access. At around 04.00 hours 20 August the company brought the attack under control. The company said it’s started an investigation into the attack and measures it can take to prevent future incidents. In a notice to customers, the company said it was doing everything it could to put an end to the problems and it would be implementing changes to its network as a result of the attack. This will result in a restart of customer modems, which may be without service for several minutes while the changes are implemented. The company said in a statement that it was also working with the National Cybersecurity Centre and Ministry of Justice after several videos with threats against Ziggo’s office were placed on social media. Ziggo said it was taking the threats very seriously and had filed a complaint with the police. Meanwhile the Dutch mobile operators KPN, Vodafone and T-Mobile reported a sharp increase in data traffic during both Ziggo attacks. A spokesman for Vodafone said data traffic doubled both times on its network. Source: http://www.telecompaper.com/news/ziggo-suffers-new-ddos-attack–1098223
Originally posted here:
Ziggo suffers new DDoS attack
RPC Portmapper Abused for DDoS Attack Reflection, Amplification
Malicious actors have started abusing the Portmapper service to amplify their distributed denial-of-service (DDoS) attacks and hide their origin, Colorado-based telecommunications company Level 3 Communications has warned. RPC Portmapper, also referred to as rpcbind and portmap, is an Open Network Computing Remote Procedure Call (ONC RPC) service designed to map RPC service numbers to network port numbers. When RPC clients want to make a call to the Internet, Portmapper tells them which TCP or UDP port to use. When Portmapper is queried, the size of the response varies depending on the RPC services present on the host. In their experiments, Level 3 researchers obtained responses of between 486 bytes (amplification factor of 7.1) and 1,930 bytes (amplification factor of 28.4) for a 68 byte query. The average amplification size obtained by Level 3 in tests conducted across its network was 1,241 bytes (18.3 amplification factor), while in the actual DDoS attacks seen by the company the value was 1,348 (19.8x amplification). Malicious actors can use Portmapper requests for DDoS attacks because the service runs on TCP or UDP port 111. Since UDP allows IP spoofing, attackers can send small requests to Portmapper using the target’s IP address and the server sends a larger response to the victim. Level 3 has observed an increasing number of DDoS attacks leveraging this vector over the summer, with the largest attacks taking place in August 10-12. The attacks were mainly aimed at the gaming, hosting, and Internet infrastructure sectors. Organizations are advised to keep an eye out for potentially malicious Portmapper requests, but Level 3 has pointed out that for the time being the global volume of Portmapper-based traffic is still small compared to other UDP services abused in DDoS attacks, such as DNS, NTP and SSDP. “Portmapper is so small it barely registers as the red line at the bottom of the graph. This shows, despite its recent growth, it is a great time to begin filtering requests and removing reflection hosts from the Internet before the attack popularity grows larger and causes more damage,” Level 3 said in a blog post. “We recommend disabling Portmapper along with NFS, NIS and all other RPC services across the open Internet as a primary option. In situations where the services must remain live, firewalling which IP addresses can reach said services and, subsequently, switching to TCP-only are mitigations to avoid becoming an unknowing participant in DDoS attacks in the future,” experts advised. There are several services that malicious actors can abuse for DDoS attack reflection and amplification. Researchers revealed at the USENIX conference last week that vulnerable BitTorrent protocols can also be leveraged for DDoS attacks. Source: http://www.securityweek.com/rpc-portmapper-abused-ddos-attack-reflection-amplification
Originally posted here:
RPC Portmapper Abused for DDoS Attack Reflection, Amplification
Mumsnet founder targeted in ‘Swatting attack’
A group callings itself @Dadsecurity claims it was responsible for the cyber and swatting attacks on the Mumsnet site Internet trolls have targeted the founder of the Mumsnet website launching a so-called ‘Swatting attack’, which resulted in armed police being called to her home. Justine Roberts, who set up the hugely influential parenting forum in 2000, claimed the site had to be temporarily shut down last week after a group calling itself @DadSecurity unleashed a cyberattack which overloaded its server. But then in a more sinister twist she said those responsible had made a malicious report to the Metropolitan Police, claiming an armed man had been seen prowling outside her home. As a result she claimed an armed police unit was scrambled to her address in the early hours of August 12. She alleged that the same thing had also happened to another Mumsnet user in which police were told gunshots had been fired at her home. Swatting attacks have become common in the United States, and take their name from the militarised Special Weapons and Tactics (SWAT) units called to deal with armed incidents. The Metropolitan Police said it was unable to provide details of the resources deployed in the incidents, but Ms Roberts, who is married to the Newsnight editor, Ian Katz, said it had left those on the receiving end “shaken up”. The group that claimed responsibility for the cyberattack used the Twitter account @DadSecurity, to brag about its actions, but the user has since been suspended. Describing what happened Ms Roberts wrote on the Mumsnet site: “On the night of Tuesday 11 August, Mumsnet came under attack from what’s known as a denial of service (DDoS) attack. “Our servers were bombarded with requests, which required our Internet service provider to massively increase server capacity to cope. “We were able to restore the site at 10am on Wednesday 12 August. Meanwhile a Twitter account, @DadSecurity, claimed responsibility, saying in various tweets, ‘Now is the start of something wonderful’, ‘RIP Mumsnet’, ‘Nothing will be normal anymore’ and ‘Our DDoS attacks are keeping you offline’.” But she said later that night they appeared to have taken one step further by making a malicious call to the police. She wrote: “An armed response team turned up at my house last week in the middle of the night, after reports of a gunman prowling around.” She explained that another Mumsnet user who challenged @DadSecurity on Twitter was warned to ‘prepare to be swatted by the best’ in a tweet that included a picture of a SWAT team. Ms Roberts wrote: “Police arrived at her house late at night following a report of gunshots. Needless to say, she and her young family were pretty shaken up. “It’s worth saying that we don’t believe these addresses were gained directly from any Mumsnet hack, as we don’t collect addresses. The police are investigating both instances.” Mumsnet is currently reviewing its online security and is asking all users to change their passwords in order to reduce the risk of any other hacks. Mumsnet has come in from criticism in the past from father’s groups, including Fathers4Justice, which claim it has an “anti-male agenda”. In 2012 Fathers4Justice launched a campaign which included a naked protest at companies that advertised with the website. Source: http://www.telegraph.co.uk/news/uknews/crime/11810790/Mumsnet-founder-targeted-in-Swatting-attack.html
Original post:
Mumsnet founder targeted in ‘Swatting attack’
