DDoS attacks are a way to keep corrupt corporations honest, according to an anonymous member of DerpTrolling, who gives us an inside look at the self-proclaimed gods of the Internet. The man behind the curtain One of the first things he says is that he absolutely cannot offer proof. This makes a disappointing amount of sense: he is a self-confessed DDoS troll, a member of the infamous group DerpTrolling. Since distributed denial-of-service attacks could be considered a federal crime under US law — and, indeed, are an offence in many locations around the globe, including the UK and Australia — he, understandably, won’t give a name, location or even rough age. As a corollary, we have no way of knowing that he is who he says he is. We’ll call him Incognito. To talk to him, we plug into a private chat session from opposite sides of the globe (as indicated by time zones) using an encrypted Chrome add-on. “I’ve seen Anonymous at its best,” he tells us. “I participated in their major DDoS attacks against Visa and PayPal, although the role DerpTrolling played in those attacks is pretty much unknown. I’ve seen the rise and fall of LulzSec. So let’s just say I am old enough to know how to stay hidden.” One thing is clear from the outset: Incognito believes that what DerpTrolling does is for the good of everyone. “DerpTrolling as a group shows the world, particularly the gaming community, how big companies and corporations such as Riot or Blizzard only care about money,” he explains. “Our methods are forcing big companies and corporations to upgrade their servers and make sure their clients are their top priority.” DerpTrolling has been around since around 2011 or so, and Incognito has been a member since the beginning. Its method of attack, as mentioned above, is DDoS — overloading servers with external communication requests, rendering the target systems unusable for a period of time. DerpTrolling has attacked several high-profile servers over the years, including those of League of Legends, World of Tanks, EVE Online, DoTA 2, Blizzard, RuneScape and, more recently, Xbox Live and the Nintendo Web store. Although their actions may appear inscrutably juvenile and unwarranted — done for, as the saying goes, the lulz — the team identifies rather strongly with Richard Stallman’s assessment of DDoS as a form of protest against what it perceives as a callous disregard for gamers on the part of games publishers. “A company that doesn’t care only for money would make the effort, which includes time and money, to make sure their servers aren’t able to be crippled by a simple DDoS attack,” Incognito said. “We decided to take action because, if we had the capability to stop corporate greed and we did nothing, that in itself is a crime. We thought DDoS attacks were appropriate because they do not affect customers in a monetary way, unlike leaking data — although we are not opposed to leaking data.” Lines in the sand He is careful to point out that DerpTrolling is against doxxing — that is, the leaking of information about a specific individual, such as address, phone number, Social Security number, credit card and bank account details — and swatting, a term for calling the police to the home of said doxxed individual for spurious reasons. In one of the most famous incidents involving the group, though, one particular individual was doxxed and swatted — Twitch streamer PhantomL0rd. While DerpTrolling was attacking Battle.net, EA.com, Club Penguin and Riot, it was allegedly because those were games PhantomL0rd was playing. At some point during the DDoS activities, PhantomL0rd was doxxed on several gaming websites — and then someone called the police to his home, accusing the streamer of holding five people hostage. Incognito is cagey about the incident, and won’t comment on why the group targeted PhantomL0rd or what precisely DerpTrolling did do — only saying that there is no hard evidence connecting DerpTrolling to the actions. “Yes, Phantoml0rd was doxxed and swatted,” he said. “But we never threatened to harm him physically and we have never taken credit for that attack.” “We decided to take action because, if we had the capability to stop corporate greed and we did nothing, that in itself is a crime.” Incognito He seems determined to impress that there are lines DerpTrolling won’t cross — that what the group does, it does for the good of all. As an example, he mentions that the group is sitting on what could have been a significant customer data leak. “We are currently in possession of over 800,000 usernames and passwords from the 2K gaming studio. As of right now, our members as a whole have decided that leaking data is not what we do, and therefore we will not leak such damaging data,” he said, adding that he had contacted 2K to inform the publisher of the vulnerability in its system — and received no response. “I personally contacted them over a month ago. I did not send them an anonymous letter, I made sure they understood exactly who I was. And offered plenty of proof.” Unless the data is actually leaked, he believes that gaming companies are unlikely to spend the money to issue a fix. CNET has contacted 2K for comment and will update when we receive a reply. Incognito also goes out of his way to dissociate DerpTrolling’s activities from those of LizardSquad, the group that claimed responsibility for calling a bomb threat on a plane carrying Sony Online Entertainment president John Smedley. “I want to make it absolutely clear that DerpTrolling is in no way affiliated with LizardSquad,” he said. Although LizardSquad had requested that the two groups work together, DerpTrolling had refused, he said. “LizardSquad is a run by an extremist hacker who has close ties to UGNazi. You could say that the ISISGang is the elite ‘leaders’ of LizardSquad. We have no wish to associate with any individual or group that has ties with such extremists.” ISISGang has been accused of making prank calls that see their targets swatted and posing as Middle Eastern terrorists, while UGNazi is allegedly responsible for several doxxings and data leaks. Incognito seems quite firm that DerpTrolling wishes to commit no actual harm. The end and the means DerpTrolling has more up its sleeve. Attacks on Xbox Live and the Nintendo Web store on Saturday, September 28 were “test fire” for “upcoming attacks”, Incognito says — although he won’t go into any further detail about that. Nor is it easy to guess who the targets might be. DerpTrolling allows the community to select targets much of the time, Incognito said, via text or tweet. The fact that sometimes the attacks achieve a result justifies the work in his view; Incognito says that League of Legends and Xbox Live have both upgraded their servers in response to DerpTrolling DDoS attacks — in spite of negative public opinion. “Children do not know what is best for them. We are basically the Gods of the Internet, we know what is best for them.” Incognito “The public will always have an opinion that is based on what the media feeds them,” he says. “Children do not know what is best for them. We are basically the Gods of the Internet, we know what is best for them.” When asked if DDoS is a snake chasing its own tail — that is, if no one engaged in DDoS attacks, then companies would not have to dedicate resources to protecting against them — he once again pleads no comment. There is a condition under which DerpTrolling will cease operations: “If the presidents of Sony and Microsoft will wear a shoe on their heads, then DerpTrolling will disband and we will not attack any more servers.” As for Incognito himself, we suspect he might be around for a long time. When asked if he himself would ever hang up his hat, he seems baffled by the question. “Why would I want to stop?” Source: http://www.cnet.com/au/news/the-gods-of-the-internet/
Read More:
Interview with a DDoS troll: Meet ‘the Gods of the Internet’


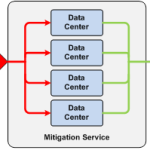 Various defense strategies can be invoked to defend against DDoS attacks. Many of these depend upon the intensity of the attack. We discuss some of these in this article. Mitigation Strategies Some protection from DDoS attacks can be provided by firewalls and intrusion-prevention systems (systems that monitor for malicious activity). When a DDoS attack begins, it is important to determine the method or methods that the attacker is using. The web site’s front-end networking devices and the server’s processing flow may be able to be reconfigured to stop the attack. UDP Attacks UDP (User Datagram Protocol) attacks send a mass of UDP requests to a victim system, which must respond to each request. One example is a ping attack. It is an enormous influx of ping requests from an attacker that requires the victim server to respond with ping responses. Another example of a UDP attack is when the Internet Control Message Protocol (ICMP) must be used by the server to return error messages. The messages may indicate that a requested service is unavailable or that a host or router cannot be reached. An attacker may send UDP messages to random ports on the victim server, and the server must respond with a “port unreachable” ICMP message. Mitigation Strategy In the case of a UDP attack, the firewall could be configured to reject all UDP messages. True, this would prevent legitimate use of UDP messages, such as pings sent by monitoring services to measure the uptimes and response times of the web site. However, to be shown as failed by a monitoring service is much better than actually being down. SYN Attacks In a SYN attack, a mass of connection requests are sent to the victim server via SYN messages. Typically, the victim server will assign connection resources and will respond with SYN ACK messages. The server expects the requesting client to complete the connections with ACK messages. However, the attacker never completes the connections; and the server soon runs out of resources to handle further connection requests. Mitigation Strategy In this case, the server connection facility could be reconfigured so that it did not assign connection resources until it received the ACK from the client. This would slightly extend the time required to establish a connection but would protect the server from being overwhelmed by this sort of an attack. DNS Reflection Attack A DNS reflection attack allows an attacker to send a massive amount of malicious traffic to a victim server by generating a relatively small amount of traffic. DNS requests with a spoofed victim address are sent to multiple DNS systems to resolve a URL. The DNS servers respond to the victim system with DNS responses. What makes this sort of attack so efficient is that the DNS response is about 100 times as large as the DNS request. Therefore, the attacker only needs to generate 1% of the traffic that will be sent to the victim system. DNS reflection attacks depend upon DNS open resolvers that will accept requests from anywhere on the Internet. DNS open resolvers were supposed to have been removed from the Internet, but 27 million still remain. Mitigation Strategy A defense against DNS reflection attacks is to allow only DNS responses from the domain of the victim server to be passed to the server. Mitigation Services Given a sufficiently large DDoSattack, even the steps mentioned here may not protect a system. If nothing else, the attack can overwhelm the bandwidth of the victim’s connection to the Internet. In such cases, the next step is to use the services of a DDoS mitigation company with large data centers that can spread the attack volume over multiple data centers and can scrub the traffic to separate bad traffic from legitimate traffic. Prolexic, Tata Communications, AT&T, Verisign, CloudFare, and others are examples of DDoS mitigation providers. These services will also monitor the nature of the attack and will adjust their defenses to be effective in the face of an attacker that modifies its strategies as the attack progresses. Legality DDoS attacks are specifically outlawed by many countries. Violators in the U.K. can serve up to ten years in prison. The U.S. has similar penalties, as do most major countries. However, there are many countries from which DDoS attacks can be launched without penalty. With respect to the Spamhaus attack described in Part 1, the CEO of CyberBunker, a Dutch company, was arrested in Spain and was returned to the Netherlands for prosecution. Summary Companies must prepare for the likelihood of losing their public-facing web services and must make plans for how they will continue in operation if these services are taken down. This should be a major topic in their Business Continuity Plans. For instance, in the case of the bank attacks described in Part 1, many banks made plans to significantly increase their call center capabilities to handle customer services should their web sites be taken down by a DDoS attack. DDoS attacks are here to stay. They are motivated by too many factors – retaliation, political statements, aggressive competitors, ransom – and are fairly easy to launch. Botnets can be rented inexpensively. There are even sophisticated tools available on the darknet to launch significant attacks. The defenses against DDoS attacks are at best limited. The ultimate defense is to subscribe to a DDoS mitigation service that can be called upon when needed. Source: http://www.techproessentials.com/ddos-attacks-can-take-down-your-online-services-part-3-defending-against-ddos-attacks/
Various defense strategies can be invoked to defend against DDoS attacks. Many of these depend upon the intensity of the attack. We discuss some of these in this article. Mitigation Strategies Some protection from DDoS attacks can be provided by firewalls and intrusion-prevention systems (systems that monitor for malicious activity). When a DDoS attack begins, it is important to determine the method or methods that the attacker is using. The web site’s front-end networking devices and the server’s processing flow may be able to be reconfigured to stop the attack. UDP Attacks UDP (User Datagram Protocol) attacks send a mass of UDP requests to a victim system, which must respond to each request. One example is a ping attack. It is an enormous influx of ping requests from an attacker that requires the victim server to respond with ping responses. Another example of a UDP attack is when the Internet Control Message Protocol (ICMP) must be used by the server to return error messages. The messages may indicate that a requested service is unavailable or that a host or router cannot be reached. An attacker may send UDP messages to random ports on the victim server, and the server must respond with a “port unreachable” ICMP message. Mitigation Strategy In the case of a UDP attack, the firewall could be configured to reject all UDP messages. True, this would prevent legitimate use of UDP messages, such as pings sent by monitoring services to measure the uptimes and response times of the web site. However, to be shown as failed by a monitoring service is much better than actually being down. SYN Attacks In a SYN attack, a mass of connection requests are sent to the victim server via SYN messages. Typically, the victim server will assign connection resources and will respond with SYN ACK messages. The server expects the requesting client to complete the connections with ACK messages. However, the attacker never completes the connections; and the server soon runs out of resources to handle further connection requests. Mitigation Strategy In this case, the server connection facility could be reconfigured so that it did not assign connection resources until it received the ACK from the client. This would slightly extend the time required to establish a connection but would protect the server from being overwhelmed by this sort of an attack. DNS Reflection Attack A DNS reflection attack allows an attacker to send a massive amount of malicious traffic to a victim server by generating a relatively small amount of traffic. DNS requests with a spoofed victim address are sent to multiple DNS systems to resolve a URL. The DNS servers respond to the victim system with DNS responses. What makes this sort of attack so efficient is that the DNS response is about 100 times as large as the DNS request. Therefore, the attacker only needs to generate 1% of the traffic that will be sent to the victim system. DNS reflection attacks depend upon DNS open resolvers that will accept requests from anywhere on the Internet. DNS open resolvers were supposed to have been removed from the Internet, but 27 million still remain. Mitigation Strategy A defense against DNS reflection attacks is to allow only DNS responses from the domain of the victim server to be passed to the server. Mitigation Services Given a sufficiently large DDoSattack, even the steps mentioned here may not protect a system. If nothing else, the attack can overwhelm the bandwidth of the victim’s connection to the Internet. In such cases, the next step is to use the services of a DDoS mitigation company with large data centers that can spread the attack volume over multiple data centers and can scrub the traffic to separate bad traffic from legitimate traffic. Prolexic, Tata Communications, AT&T, Verisign, CloudFare, and others are examples of DDoS mitigation providers. These services will also monitor the nature of the attack and will adjust their defenses to be effective in the face of an attacker that modifies its strategies as the attack progresses. Legality DDoS attacks are specifically outlawed by many countries. Violators in the U.K. can serve up to ten years in prison. The U.S. has similar penalties, as do most major countries. However, there are many countries from which DDoS attacks can be launched without penalty. With respect to the Spamhaus attack described in Part 1, the CEO of CyberBunker, a Dutch company, was arrested in Spain and was returned to the Netherlands for prosecution. Summary Companies must prepare for the likelihood of losing their public-facing web services and must make plans for how they will continue in operation if these services are taken down. This should be a major topic in their Business Continuity Plans. For instance, in the case of the bank attacks described in Part 1, many banks made plans to significantly increase their call center capabilities to handle customer services should their web sites be taken down by a DDoS attack. DDoS attacks are here to stay. They are motivated by too many factors – retaliation, political statements, aggressive competitors, ransom – and are fairly easy to launch. Botnets can be rented inexpensively. There are even sophisticated tools available on the darknet to launch significant attacks. The defenses against DDoS attacks are at best limited. The ultimate defense is to subscribe to a DDoS mitigation service that can be called upon when needed. Source: http://www.techproessentials.com/ddos-attacks-can-take-down-your-online-services-part-3-defending-against-ddos-attacks/