Empirical research just published suggests that, whilst overall DDoS attack volumes are increasing steadily, new attack vectors are also constantly being used by cybercriminals. The analysis – entitled `NSFOCUS DDoS Threat Report 2013? – is based on more than 244,000 real-life distributed denial of service attacks observed at Tier 1 or Tier 2 ISPs by the research firm during the year. Researchers found that 79.8 percent of all attacks were 50 Mbps or less. In addition, although large size attacks get the most media attention, only 0.63 percent of all attack incidents were logged at 4 Gbps or more. Perhaps most interestingly of all is that more than 90 percent of the observed attacks lasted 30 minutes or less – and that 63.6 per cent of all targeted victims are attacked more than once. This figure is in line with earlier figures from Neustar whose second annual report, entitled `DDoS Attacks & Impact Report – 2014: The Danger Deepens’ – suggested that once attacked, there is an estimated 69 percent chance of a repeat attack. Delving into the report reveals that HTTP_FLOOD, TCP_FLOOD and DNS_FLOOD are the top three attack types – contributing to more than 87 percent of all attacks. DNS_FLOOD attacks, however, significantly increased from 13.1 percent during the first half of the 2013 to 50.1 percent in the second half. So why the short duration attacks? The report suggests that, after analysing almost a quarter million DDoS incidents, a clear trend emerges, namely that that majority of DDoS attacks seen were short in duration, small in total attack size, and frequently repeating against the same target. “These short and frequently repeating attacks often serve two purposes: First, to scout their victims’ defence capabilities before more tailored assaults are launched, and second, to act as smokescreens or decoys for other exploitation,” says the report. The analysis adds that that many companies are using a combination of traditional counter-measures like scripts, tools and access control lists (ACLs) to handle network layer attacks – as well as on-premise DDoS mitigation systems for more prompt and effective mitigation against hybrid attacks (defined as a combination of network-layer and application-layer attacks). The most interesting takeout from the report, SCMagazineUK.com notes, is that the `old guard’ attack vectors – including the use of SNMP – remain an evolving constant. According to Sean Power, security operations manager with DOSarrest, amplification attacks – such as SNMP – are not really that new. “Legitimate SNMP traffic has no need to leave your network and should be prevented from doing so. This attack exists because many organisations fail to prevent this,” he explained. Power went on to say that the effectiveness of the attack stems from the fact that any Web site can be targeted and requires very little effort to produce excessive traffic, since it relies on third party unsecured networks to do most of the heavy lifting for the attack. “Blocking these attacks is best done via your edge devices as far removed from the targets as possible,” he said, adding that if the attack is large enough that it is overwhelming your edge devices, then you need to look at cloud-based technology for cleaning the traffic. Also commenting on the report, Tom Cross, director of security research for Lancope, said that many people who launch attacks on the Internet do so using toolkits that make the process of launching attacks as easy as installing a software application and running it. “DDoS attacks have become increasingly popular, there are many ways to launch them and lots of different tools circulating that launch attacks in different ways. As a consequence, anyone providing service on the Internet should be prepared for volumetric traffic floods involving any kind of Internet traffic,” he explained. Cross says that it is also important that people do not allow their networks to serve as reflectors that attackers can use to amplify their denial of service attacks. “To that end, DNS, SNMP, NTP, and Voice over IP services in particular should be checked to make sure that they cannot be used by an anonymous third party as a reflector. Locking down these services is part of being a good citizen of the Internet,” he said. Source: http://www.scmagazineuk.com/repeat-attacks-hit-two-thirds-of-ddos-victims/article/348960/
Tag Archives: dos attacks
Detecting Constant Low-Frequency Appilication Layer Ddos Attacks Using Collaborative Algorithms
Abstract: — A DDoS (i.e., Distributed Denial of Service) attack is a large scale distributed attempt by malicious attackers to fill the users’ network with a massive number of packets. This exhausts resources like bandwidth, computing power, etc.; User can’t provide services to its clients and network performance get destroyed. The methods like hop count filtering; rate limiting and statistical filtering are used for recovery. In this paper, we explored two new information metrics which have generalized information about entropy metric and distance metric .They can detect low-rate of Distributed Denial of Service i.e., DDoS attacks by measuring difference between the legitimate traffic and the attack traffic. The generalized entropy metric information can detect the attacks on several hops before than the traditional Shannon metric. The proposed information about the distance metric outperforms the popular Kullback–Leibler divergence approach as it has the ability to perfectly enlarge the adjudication distance and gets the optimal detection sensitivity. Further the IP trace back algorithm can find all attackers as well as their attacks through local area networks (LANs) and will delete the attack traffic. Index Terms— Attack detection, information metrics, IP trace back, low-rate distributed denial of service (DDoS) attack. I. INTRODUCTION Present in networking we have to provide security to information while accessing and transmitting. Lots of hacking tools are available for getting the information that was transmitted in the network. A standard security mechanism is in need to overcome this thing. The information in the network have to be out of range to intruders. It impacts bandwidth, processing capacity, or memory of a network. It has huge occupying nature on wired and wireless networks. DDoS attack is an intelligent attack and considered as low rate attack. The attacker is capable of sending multiple numbers of attack packets to the user which is out bound to elude detection. Mostly combination of large-scale DDoS attacks and multiple Low-rate attacks are making user uncomfortable in the networking process. So it is becoming difficult to detect and getting solutions to such attacks. Nowadays, several Distributed Denial of Service attacking detection methods of metrics are in use, they are mainly separated into the following categories: i) the signature-based metric, and ii) anomaly-based metric. The signature-based method of metric depends on a technology that deploys a predefined set of attack-signatures like patterns or strings as signatures to match the incoming packets. This anomaly-based detection method of metric typically models the normal network (traffic) behavior and deploys it to compare the differences to incoming network behavior. Anomaly-based method of detection has many limitations: i) Attackers can train detection systems to gradually accept anomaly network behavior as normal . ii) The rate at which the false positives use the anomaly- based detection metric is generally higher than those using the signature-based detection metric. It is difficult to set a threshold that helps us to balance the rate of false positives and the false negatives. iii) Precisely the extraction of the features like normal and anomalous network behaviors is very difficult. An anomaly- based detection method of metric uses a predefined as well as specific threshold for example, an abnormal deviation of parameters related to some statistical characteristics that are considered from normal network traffic, to identify abnormal traffic amongst all normal traffic. Hence, it is important to utilize and to be decisive while choosing the statistical methods and tools respectively. It is an acceptable fact that the fractional Gaussian noise function and the Poisson distribution function can be used to simulate the can be used to simulate real network traffic in aggregation and the DDoS attack traffic in aggregation respectively. Many information theory based metrics have been proposed to overcome the above limitations. In information theory, information entropy is a measure of the uncertainty associated with a random variable. Information distance (or divergence) is a measure of the difference between different probability distributions. Shannon’s entropy and Kullback–Leibler’s divergence methods have both been regarded as effective methods based on IP address-distribution statistics for detecting the abnormal traffic. Time taken for detection as well as detection accuracy of DDoS attacks are the two most important criteria for rating a defense system. Through this paper, we make you aware of two new and effective anomaly-based detection method of metrics that not only identify attacks quickly, but also they reduce the rate of false positives as compared to the traditional Shannon’s entropy method and the Kullback–Leibler divergence method. Contributions Some of the main contributions made in this paper are as follows: 1) It highlights the advantages and also it analyses the generalized entropy and information distance compared with Shannon entropy and Kullback–Leibler distance, respectively. 2) It proposes a better technique to the generalized entropy and information distance metrics to perform better than the traditional Shannon entropy and Kullback–Leibler distance method of metrics at low-rate DDoS attack detection in terms of quick detection, low rate of false positives and stabilities. 3) It proposes an effective IP trace back scheme that is based on an information distance method of metric that can trace all the attacks made by local area networks (LANs) and drive them back in a short time. ALGORITHMS FOR DETECTION AND IP TRACEBACK ANALYSIS In this section, we propose and analyze two effective detection algorithms and an IP traceback scheme. In this paper, we make the following reasonable assumptions: 1) We will have full control of all the routers; 2) We will have extracted an effective feature of network traffic to sample its probability distribution; 3) We will have obtained and stored the average traffic of the normal, as well as the local thresholds and routers on their own in advance; 4) On all routers, the attack traffic obeys Poisson distribution and the normal traffic obeys Gaussian noise distribution. Our algorithm can not only detect DDoS attacks at router via single-point detection, but can also detect the attacks that are made using a collaborative detection at routers. Fig. 2 shows the processing flowchart of the collaborative detection algorithm. Compared with single- point detection, we can detect attacks even before by using a collaborative detection approaches if the traffic can be analyzed before them. The divergence and distance are increasing simultaneously. By increasing the divergence between legitimate traffic and attack traffic we can distinguish DDoS attacks easily and earlier. Therefore, in DDoS attack detection; we can take full advantage of the additive and increasing properties in of the information divergence and the information distance to enlarge the distance or gap between legitimate traffic and attack traffic. This means we can find and raise alarms for DDoS attacks quickly and accurately with a lower rate of false positives in upper stream routers instead of the victim’s router. In information theory, we know that both information divergence and information distance are nonnegative values and the sum of the divergences or distances is always greater C. IP Trace back Analysis IP trace back is the ability to find the source of an IP packet without relying on the source IP field in the packet, which is often spoofed. We combine our DDoS attacks detection metric with IP trace back algorithm and filtering technology together to form an effective collaborative defense mechanism against network security threats in Internet. In hop-by-hop IP tracing, the more hops the more tracing processes, thus the longer time will be taken. Listing 1. A collaborative DDoS attack detection algorithm 1. Set the sampling frequency as f , the sampling as T, and the collaborative detection threshold as 0. 2. In routers R1 and R2 of Fig. 1, sampling the network tra ?ic comes from the upstream routers R3, R4 , R5, R6 and LAN1, LAN; in parallel. 3. Calculate in parallel the numbers of packet which have various recognizable characteristics (e.g., the source IP address or the packet’s size, etc.) in each sampling time interval ‘r(‘r = 1/ f) within T. 4. Calculate the probability distributions of the network tra ?ic come from R3, R4, LAN 1 and R5, R6, LAN2 in parallel. 5. Calculate their distances on router R1 and R2, respectively, using the formula Da(Ps Q) = Da(PllQ) + D¢-(Q||P)- 6. Sum the distances. 7. If the summed distance is more than the collaborative detection threshold 0, then the system detects the DDoS attack, and begins to raise an alarm and discards the attack packets; otherwise the routers forward the packets to the downstream routers. In order to convenience for IP trace back algorithm analysis, we classify two types of traffic in Figs. 1 and 3 as local traffic and forward traffic, respectively. The local traffic of is the traffic generated from its LAN, the forward traffic of is the sum of its local traffic and the traffic forwarded from its immediate upstream routers. In this paper, we propose an IP trace back algorithm that can trace the source (zombies) of the attack up to its local administrative network; Listing 2 illustrates this algorithm. Listing 2. An IP traceback algorithm in DDoS attacks detection The proposed IP trace back algorithm based on a sample scenario of low-rate DDoS attacks on a victim. When the proposed attacks detection system detects an attack on a victim, the proposed IP traceback algorithm will be launched immediately. On router , the proposed traceback algorithm calculates information distances based on variations of its local traffic and the forward traffic from its immediate upstream routers; in this paper, we set LAN of router include the victim. If the information distance based on its local traffic is more than the specific detection threshold, the proposed detection system detects an attack in its LAN IP_Traceback_Algorithm () while(true) call Check_ForwardTraf ?c(0)//check attacks on router R0 (or victim) Check_ForwardTra ?ic (i) calculate infommtion distance D I-( R,-) i1°D:(Ri> > arm) call Check_LocalTra ?c for j = 1 to n k = the ID of the jth immediate upstream router of router Ri call Check_ForwardTra ?ic (Ic) end for end if I Check_LocalTra ?ic (xi) calculate infomlation distance D1,- if Du > 01¢ stop forwarding the attack tra ?c to downstream routers (or destination), label the zombie end if This means that the detected attack is an internal attack. If the information distances based on the forward traffic from its immediate upstream routers and are both more than the specific detection threshold and, respectively, the proposed detection system has detected attacks in routers and , then on and the proposed trace back algorithm calculates information distances based on variations of their local traffic and the forward traffic from their immediate upstream routers, and Will find that there are no attacks in LAN and LAN and ; therefore, on routers , and the proposed algorithm calculates continually information distances based on variations of their local traffic and the forward traffic from their immediate upstream routers, then can find there is an attack (zombie) in LAN so the router will stop forwarding the traffic from the zombie immediately. RELATED WORK The metrics of an anomaly-based detection have been the focusing on the intense study years together in an attempt to detect the intrusions and attacks done on the Internet. Recently, this information theory is being used as one of the statistical metrics that are being increasingly used for anomaly detection. Feinstein et al present methods to identify DDoS attacks by computing entropy and frequency-sorted of selected packet attributes. These Distributed Denial of Service attacks show their characteristics of the selected packet attributes to its anomalies, and its detection accuracy and performance can be analyzed with the help of live traffic traces among a variety of network environments. However, because of the proposed detector and responder there will be a coordination lack with each other, then the impact of its responses on legitimate traffic and expenses for computational analysis may increase. Yu and Zhou applied a special technique for information theory parameter to discriminate the Distributed Denial of Service attack against the surge legitimate accessing. That technique is based on the shared regularities along with different Distributed Denial of Service attack traffic, which differentiates it from real surging accessing over a short period of time. However, the proposed detection algorithm will be helpful to us in predicting a single directions or a limited number of directions but the real problem comes when these attackers adopt a multiple attack package generation function in one attack to fool us. Lee and Xiang used various information-theoretic measures like entropy, conditional entropy, relative conditional entropy, information gain, and information cost for anomaly detection, etc. yes it is true that for some extent measures like mentioned above can be used to evaluate the quality of anomaly detection methods and to build the appropriate anomaly detection models but we find a tough time to build an adaptive model that can dynamically adjust itself to different sequence lengths or time windows that are based on run-time information. A low-rate Distributed Denial of Service attack is substantially different from a high-rate Distributed Denial of Service attack which is considered to be the traditional type of Distributed Denial of Service attack. A few number of researchers have proposed several detection schemes against Distributed Denial of Service type of attack. Sun et al. proposed a distributed detection mechanism that is used as a dynamic time warping method for identifying the presence of the low-rate attacks, then a fair resource for the allocation mechanism will be used to minimize the affected flows in number. However, this method can lose the legitimate traffic to some extent Shevtekar et al. gave a light-weight data structure to store the necessary flow history at edge routers to detect the low-rate TCP DoS attacks. Although this method can detect any periodic pattern in the flows, it may not be scalable and can be deceived by the IP address spoofing. Chen et al. Present a collaborative detection of DDoS attacks. While focusing on detection rate, it is difficult for this scheme to differentiate the normal flash crowds and real attacks. As it heavily relies on the normal operation of participating routers, the false positives will increase if the routers are compromised. Zhang et al. propose to use self-similarity to detect low-rate DDoS attacks. While the approach is claimed to be effective, the paper does not use real scenario data to evaluate it.Kullback– Leibler divergence, as a well-known information divergence, has been used by researchers to detect abnormal traffic such as DDoS attacks. The difference between previous work and our research is that we are the first to propose using information divergence for DDoS attack detection. Information divergence, as the generalized divergence, can deduce many concrete divergence forms according to different values of order. For example, when, it can decipher the Kullback–Leibler divergence. It is very important and significant that we can obtain the optimal value of divergence between the attack traffic and the legitimate traffic in a DDoS detection system by adjusting the value of order of information n divergence. In addition to this, we also study the properties of Kullback– Leibler divergence and information divergence in theory and overcome their asymmetric property when used in real measurement. We successfully convert the information divergence into an effective metric in DDoS attack (including both low-rate and high-rate) detection. V. CONCLUSION In this paper we described different techniques which are for the prevention of the denial of service attacks. A new methodology along with the existing packet marking technique was proposed. The information contains the lifetime of the packet. The traceback process an accurate one. As the proposed metrics can increase the information distance among attack traffic and legitimate traffic. Those lead to detect low-rate DDoS attacks fast and reduce the false positive rate accurately. This information distance metric overcomes the properties of asymmetric of both Kullback-Leibler and information divergences. IP traceback scheme based on information metrics can effectively trace all attacks including LANs (zombies). Our proposed information metrics improve the performance of low-rate DDoS attacks detection and IP traceback over the traditional approaches. Source: http://www.scribd.com/doc/226717154/Detecting-Constant-Low-Frequency-Appilication-Layer-Ddos-Attacks-Using-Collaborative-Algorithms
Taken from:
Detecting Constant Low-Frequency Appilication Layer Ddos Attacks Using Collaborative Algorithms
DDoS attacks using SNMP amplification on the rise
Attackers are increasingly abusing devices configured to publicly respond to SNMP (Simple Network Management Protocol) requests over the Internet to amplify distributed denial-of-service attacks. This amplification technique, which is also known as reflection, can theoretically work with any protocol that is vulnerable to IP (Internet Protocol) address spoofing and can generate large responses to significantly smaller queries. Attackers can craft requests that appear to originate from the IP address of their intended victim in order to trick servers that accept requests over such protocols from the Internet to flood the victim with data. Many DDoS attacks in the past year have used misconfigured DNS (Domain Name System) and NTP (Network Time Protocol) servers for amplification. However, devices that support SNMP, a protocol designed to allow the monitoring of network-attached devices by querying information about their configuration, can also be abused if the SNMP service is directly exposed to the Internet. SNMP-enabled devices with such configurations can be found both in home and business environments and include printers, switches, firewalls and routers. Since April 11, the Prolexic Security Engineering Response Team (PLXsert), which is now part of Akamai Technologies, has identified 14 separate DDoS campaigns that used SNMP reflection. Almost half of the malicious SNMP reflected traffic came from IP addresses in the U.S. and 18 percent from China, PLXsert said in a threat advisory published Thursday. “The attacks targeted clients in the following industry verticals: consumer goods, gaming, hosting, non-profits and software-as-a-service (SaaS).” One of the tools used to launch the recent attacks was created in 2011 by a hacker group called Team Poison and can send spoofed SNMP GetBulk requests to publicly accessible SNMP-enabled devices to trigger responses that can be more than 1,700 times larger than the requests, the Prolexic team said. The attackers crafted their requests to have a source port of 80—usually assigned to HTTP—so that vulnerable devices return their SNMP responses to the victims on the same port, flooding their HTTP services. “Until approximately three years ago, SNMP devices were manufactured using SNMP version 2 and were commonly delivered with the SNMP protocol openly accessible to the public by default,” PLXsert said. “Devices using SNMP v3 are more secure. To stop these older devices from participating in attacks, network administrators need to check for the presence of this protocol and turn off public access.” Information over SNMP is controlled by a so-called community string, which in the case of SNMP v2c is “public” by default, PLXsert said. SNMP amplification attacks are not really new, said Sean Power, security operations manager at DDoS protection vendor DOSarrest Internet Security, Friday via email. “Legitimate SNMP traffic has no need to leave your network and should be prevented from doing so. This attack exists because many organizations fail to prevent this.” It’s important for network owners to lock down services that can be used for DDoS reflection and amplification like DNS, SNMP, NTP and voice over IP. This “is part of being a good citizen of the Internet,” said Tom Cross, director of security research for network security and performance monitoring vendor Lancope, via email. Source: http://www.pcworld.com/article/2159060/ddos-attacks-using-snmp-amplification-on-the-rise.html
View original post here:
DDoS attacks using SNMP amplification on the rise
Australian Labor Party and the Bob Brown Foundation hit by DDoS attack
Inadvertent victims of “politically motivated” hack. A politically motivated DDoS attack on a US-based web hosting service has delivered global repercussions affecting a number of Australian websites including the homepages of the Australian Labor Party and the Bob Brown Foundation. Both organisations use the services of NationBuilder, a cloud-based web hosting and customer relationship management platform designed specifically for nonprofits, political parties and politicians. The ALP.org.au website was down for a few hours yesterday morning, its Canberra HQ confirmed. The Bob Brown Foundation site was also down yesterday and then again last night, said organiser Steven Chaffer, who had been contacted by a NationBuilder account rrepresentative. The state branches of the Labor Party also use NationBuilder, as does Victorian independent MP Cathy McGowan and the community services union United Voice. United Voice said it was not aware of any disturbance to its web presence. Yesterday NationBuilder was hit by a DDoS attack it believes to have been in protest against the political stance of one of its clients. “We are reasonably certain the attack is directed at one of our customers for their political beliefs, and is meant to disrupt upcoming elections,” wrote CEO Jim Gilliam on the NationBuilder website early this morning Australian time. He said the attack has caused “intermittent service outages” for the company’s clients but assured users that data and financial information was never exposed. “We know the impact is immeasurable and we are very, very sorry,” he said. “We are fiercely committed to serving all of our customers. Everyone has the right to organise – in fact, this is the very reason NationBuilder exists.” NationBuilder has not responded to iTnews’ requests to confirm the identity of the targeted client. However posts on the Anonymous hackers forum and from the self-professed antagonist on Twitter claim that the attack is targeting the British political party UKIP, which is taking its anti-immigration policy platform to elections for the UK membership of the European Union next week. The party’s leader Nigel Farage has been a controversial figure, branded as a racist by the UK Labor party. UKIP has been the subject of DDoS attacks before, and its website was one of many down intermittently yesterday and into today. Australian clients told iTnews that their services have now resumed. Source: http://www.itnews.com.au/News/386077,alp-bob-brown-sites-downed-by-ddos.aspx?utm_source=feed&utm_medium=rss&utm_campaign=editors_picks
View the original here:
Australian Labor Party and the Bob Brown Foundation hit by DDoS attack
SNMP could be the future for DDoS attacks
DNS amplification and NTP reflection are two big buzz-terms in the modern world of distributed denial-of-service (DDoS) attacks, but when successful defensive measures force those wells to run dry, a lesser-used reflection attack vector, known as Simple Network Management Protocol (SNMP), could take the forefront. Johannes Ullrich, dean of research with the SANS Technology Institute, told SCMagazine.com in a Monday email correspondence that SNMP, a UDP-based protocol used to read and set the configurations of network devices, hasn’t posed as big a threat as DNS and NTP attacks because there are not as many reflectors available as there are for other protocols. Ullrich said that most network-connected devices support SNMP in some form and, in a Thursday post, opined that it could be the next go-to vector for attackers after he observed a DDoS reflection attack taking advantage of an unnamed video conferencing system that was exposing SNMP. In this instance, the attacker spoofed a SNMP request to appear to originate from 117.27.239.158, Ullrich said, explaining that the video conferencing system receives the request and then replies back to the IP address with a significant reply. An 87 byte “getBulkRequest” resulted in a return of 60,000 bytes of fragmented data, Ullrich wrote in the post, adding that the individual reporting the attack observed roughly five megabits per second of traffic. “The requests are pretty short, asking for a particular item, and the replies can be very large,” Ullrich said. “For example, SNMP can be used to query a switch for a list of all the devices connected to it. SNMP provides replies that can be larger than DNS or NTP replies.” As people improve configurations, effectively causing those DNS and NTP reflectors to dry up, SNMP could be the attack vector of choice, Ullrich said – a point that John Graham-Cumming, a programmer with CloudFlare, agreed with in a Monday email correspondence with SCMagazine.com. “I think that attackers will turn to SNMP once other attack methods are thwarted,” Graham-Cumming said. “At the moment it’s easy to use NTP and DNS for attacks, so there’s no need for SNMP.” To get a jumpstart defending against this DDoS vector, Graham-Cumming suggested that network operators limit access to the SNMP devices on their networks. Ullrich went so far as to say that SNMP devices should not be exposed to the internet at all. Both experts added that the “community string,” which serves as a password for accepting requests, should not be so obvious. Source: http://www.scmagazine.com/snmp-could-be-the-future-for-ddos-attacks/article/346799/
France Getting Battered By DDoS Attacks
France is seeing massive amounts of DDoS traffic going through its networks, thanks to sizeable hits on the country’s popular hosting providers As the UK enjoys a relatively low volume of distributed denial of service (DDoS) attacks, France is seeing deluges of traffic hitting organisations frequently, according to research. Major hosting providers, including the hugely-polular, OVH have attracted DDoSers to France, which was only outdone by the US in terms of the amount of DDoS traffic passing through the countries’ networks, according to Arbor Networks. A record 325Gbps attack hit France this year, but it is not known who was involved. DDoS threat getting bigger and bigger Darren Anstee, director of solutions architects at Arbor, said France was being attacked largely because of the popularity of those hosting providers. “They’ve got a lot of big hosting providers and some of those are used by the gaming industry [which is subject to significant sized attacks],” he told TechWeekEurope . Arbor spotted an unprecedented rise in DDoS attacks over the first quarter of 2014. It saw 72 attacks larger than 100Gbps and 1.5 times the number of attacks over 20Gbps as in the whole of 2013. The epic increase in attack size has come as a result of what’s known as amplification. Protocols such as Network Time Protocol can be used to generate massive DDoS attacks with relatively little effort on behalf of the offenders. They can abuse vulnerable NTP servers by spoofing the IP address of a target, sending small requests and getting massive responses. The target IP is then flooded with that traffic. Even protocols used by popular gaming services, from Quake to the Steam protocol, can be abused for amplification purposes. Source: http://www.techweekeurope.co.uk/news/ddos-france-gaming-hosting-companies-144777
View the original here:
France Getting Battered By DDoS Attacks

How to abuse Facebook feature to conduct powerful DDoS attack
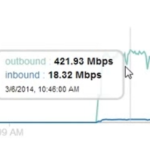 A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/
A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/
Follow this link:
How to abuse Facebook feature to conduct powerful DDoS attack
Researcher reveals how Facebook Notes can be used to DDoS sites
A programmer has divulged how the Facebook Notes feature can be used to launch distributed denial-of-service (DDoS) attacks against websites. In a blog post this weekend, researcher Chaman Thapa said that the DDoS abuse is possible due to Facebook’s protocol of allowing HMTL image tags in notes. “Facebook Notes allows users to include tags,” Thapa wrote in the Sunday blog post. “Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once, however, [and by] using random GET parameters the cache can be bypassed and the feature can be abused to cause a huge HTTP GET flood.” By creating a list of unique image tags, and using m.facebook.com to create notes, Thapa was able to create several notes, which were each responsible for sending an influx of HTTP request to the target server, he wrote. In only a couple of seconds, he was able to send thousands of GET requests to the designated server. Thapa disclosed the issue to Facebook’s bug bounty program on March 3, but after being alerted to the issue, the company ultimately said that the attack scenario was “interesting/creative,” – but one the company didn’t intend to fix due to the logistics involved. Thapa posted the email correspondence with Facebook (which occurred April 11) in his blog post. “In the end, the conclusion is that there’s no real way to us fix this that would stop ‘attacks’ against small consumer grade sites without also significantly degrading the overall functionality,” Facebook told Thapa. “Unfortunately, so-called ‘won’t fix’ items aren’t eligible under the bug bounty program, so there won’t be a reward for this issue. I want to acknowledge, however, both that I think your proposed attack is interesting/creative and that you clearly put a lot of work into researching and reporting the issue last month. That IS appreciated and we do hope that you’ll continue to submit any future security issues you find to the Facebook bug bounty program.” In a Friday email to SCMagazine.com, a Facebook spokesperson further explained the company’s decision on addressing the bug. “Ultimately, we decided against making changes to avoid disrupting intended and desirable functions,” the spokesperson wrote. Via his blog, Thapa also revealed that similar DDoS abuse can be carried out using Google’s Feedfetcher tool. According to a Google support page, Feedfetcher allows Google to grab RSS or Atom feeds when users add them to their Google homepage or Google Reader. Source: http://www.scmagazine.com/researcher-reveals-how-facebook-notes-can-be-used-to-ddos-sites/article/344271/
Continue Reading:
Researcher reveals how Facebook Notes can be used to DDoS sites
DOSarrest Releases Latest Generation DDoS Mitigation System Software
VANCOUVER, BRITISH COLUMBIA–(Marketwired – Apr 23, 2014) – DOSarrest has just released its latest generation of proprietary backend software that incorporates an all-new customer-facing portal. This new release will enable DOSarrest to implement changes to customer configurations in seconds, enabling them to apply custom made DDoS mitigation modules extremely quickly. It is also equipped with an Intrusion Detection System (IDS), allowing the security team to pinpoint sophisticated layer 7 attacks as well as provide cloud based Web Application Firewall (WAF) services for its customers. Mark Teolis, GM at DOSarrest said: “This upgrade is by far our largest project to date, it has taken us over 2 years of development and testing to get here. This latest generation of software is extremely powerful, and can stop the next generation of sophisticated layer 7 attacks.” DOSarrest is now able to offer additional services, including: Cloud Based Web Application Firewall (WAF) Cloud based layer 7 load balancing, Local, Global with health checks Enhanced reporting on traffic types, status codes, cache performance, etc Create virtual servers, to have us pick-up, cache and deliver content from multiple customer servers IDS engine to detect and help stop any malicious traffic “We recognised our customers’ requirements to have comprehensive security related services, rather than disparate point solutions; this new system has all the features that we need to accommodate them. The best part about this new generation of software is its flexibility at the core. What used to take days and weeks to develop and implement, can now be measured in minutes and hours,” added Jag Bains, CTO at DOSarrest. Bains went on to say: “The best part of this new release is that it enables us to quickly react and stop sophisticated attacks that have not even been created yet!” Source: http://www.reuters.com/article/2014/04/23/idUSnMKWNkbj9a+1e0+MKW20140423
See the original article here:
DOSarrest Releases Latest Generation DDoS Mitigation System Software
Bahrain Telecom Teams Up With DOSarrest to Offer DDoS Protection Services
VANCOUVER, BRITISH COLUMBIA–(Marketwired – April 16, 2014) – Bahrain Telecom realized the threat of DDoS attacks on their customer base and set out to explore the various options available for their business customers’ enterprise websites. After evaluating the options available, BATELCO chose the fully managed DDoS Protection service offered by DOSarrest Internet Security. The service will be offered by BATELCO to its business customers as part of its cloud portfolio. Batelco Enterprise General Manager Adel Daylami said that DOSarrest came as an answer to the increased threats in cyber space, as cyber-attacks have become a major security concern for organizations of all sizes. “The DDoS Mitigation solution is designed to protect customers’ networks against any malicious attempts by containing the harm of such attacks, thus ensuring the operational status of the organisation. The introduction of this service is in line with our repeated commitments to providing our valued customers with the most advanced products and services that meet their dynamic demands,” added Mr. Daylami. “We are honored to be providing DDoS protection services for Batelco’s business customers. We have been providing DDoS protection for a number of Bahrain-based enterprises, for over 4 years now, this announcement just cements the business association,” states Mark Teolis, General Manager of DOSarrest. About Batelco: Batelco Group is headquartered in the Kingdom of Bahrain and listed on the Bahrain Bourse. Batelco has played a pivotal role in the country’s development as a major communications hub and today is the leading integrated communications’ provider, continuing to lead and shape the local consumer market and the enterprise ICT market. Batelco has been growing overseas via investing in other market-leading fixed and wireless operators. Batelco Group has evolved from being a regional Middle Eastern operation to become a major communications company with direct and indirect investments across 14 geographies, namely Bahrain, Jordan, Kuwait, Saudi Arabia, Yemen, Egypt, Guernsey, Jersey, Isle of Man, Maldives, Diego Garcia, St. Helena, Ascension Islands and Falklands. (www.batelcogroup.com) About DOSarrest Internet Security: DOSarrest, founded in 2007 in Vancouver, BC, Canada, is one of only a couple of companies worldwide to specialize in only cloud based DDoS protection services. Their global client base includes mission critical ecommerce websites in a wide range of business segments including financial, health, media, education and government. Their innovative systems, software and exceptional service have been leading edge for over 7 years now. Source: http://www.marketwired.com/press-release/bahrain-telecom-teams-up-with-dosarrest-to-offer-ddos-protection-services-1900083.htm
See the original article here:
Bahrain Telecom Teams Up With DOSarrest to Offer DDoS Protection Services
