A number of Swedish government websites and major media outlets were knocked offline for hours over the weekend, police say. No one has taken responsibility for the cyberattacks, which silenced at least seven of Sweden’s most prominent news organizations for hours amid growing tension with Russia. A flood of web traffic Saturday night either crippled or totally shut down the news sites Dagens Nyheter, Svenska Dagbladet, Expressen, Aftonbladet, Dagens Industri, Sydsvenskan and Helsingborgs Dagblad for roughly three hours. Police launched an investigation Sunday, Agence France-Presse reported, with investigators telling many of the same sites the traffic appears to have originated in Russia. Cyberattackers, ranging from Anonymous to state hacking groups, often use distributed denial of service, or DDoS, attacks to direct a wave of falsified web traffic at a single or small number of sites, overwhelming them with traffic for hours or days. This attack was “extremely dangerous and serious,” Jeannette Gustafsdotter, the head of the Swedish Media Publishers’ Association, told the news agency TT, as quoted by the Local.se. “To threaten access to news coverage is a threat to democracy.” The onslaught came after an anonymous Twitter account, using the handle @_notJ, warned of imminent attacks against sites that posted “propaganda.” Aftonbladet, one of the sites mentioned in the tweets, has published a number of stories on the Russian plane crash that killed 62 people and other topics that don’t portray Russia in a positive light. This is what happends when you spread false propaganda. Aftonbladet.se #offline@Aftonbladet — J (@_notJ) March 19, 2016 The following days attacks against the Swedish goverment and media spreading false propaganda will be targetted. — J (@_notJ) March 19, 2016 The attacks also came after a Swedish government report cited Russian “extreme movements, information operations and misinformation campaigns” aimed at Swedish lawmakers and the public as Sweden’s most formidable intelligence threat. The Swedish government asked Russian Embassy staff to leave Sweden in 2015, though the report noted that suspected spies were still working as diplomats, airline employees and business executives. Source: http://m.ibtimes.com/ddos-attacks-cripple-swedish-news-sites-amid-russia-tension-2340079
Original post:
DDoS Attacks Cripple Swedish News Sites Amid Russia Tension


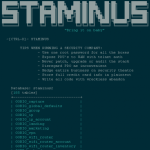 Staminus Communications Inc ., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data. Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday. “Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.” Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages. Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks. The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards. Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online. I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them. It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services. Source: https://krebsonsecurity.com/2016/03/hackers-target-anti-ddos-firm-staminus/
Staminus Communications Inc ., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s entire network was down for more than 20 hours until Thursday evening, leaving customers to vent their rage on the company’s Facebook and Twitter pages. In the midst of the outage, someone posted online download links for what appear to be Staminus’s customer credentials, support tickets, credit card numbers and other sensitive data. Newport Beach, Calif.-based Staminus first acknowledged an issue on its social media pages because the company’s Web site was unavailable much of Thursday. “Around 5am PST today, a rare event cascaded across multiple routers in a system wide event, making our backbone unavailable,” Staminus wrote to its customers. “Our technicians quickly began working to identify the problem. We understand and share your frustration. We currently have all hands on deck working to restore service but have no ETA for full recovery.” Staminus now says its global services are back online, and that ancillary services are being brought back online. However, the company’s Web site still displays a black page with a short message directing customers to Staminus’s social media pages. Meanwhile, a huge trove of data appeared online Thursday, in a classic “hacker e-zine” format entitled, “Fuck ’em all.” The page includes links to download databases reportedly stolen from Staminus and from Intreppid, another Staminus project that targets customers looking for protection against large DDoS attacks. The authors of this particular e-zine indicated that they seized control over most or all of Staminus’s Internet routers and reset the devices to their factory settings. They also accuse Staminus of “using one root password for all the boxes,” and of storing customer credit card data in plain text, which is violation of payment card industry standards. Staminus so far has not offered any additional details about what may have caused the outage, nor has it acknowledged any kind of intrusion. Several Twitter accounts associated with people who claim to be Staminus customers frustrated by the outage say they have confirmed seeing their own account credentials in the trove of data dumped online. I’ve sent multiple requests for comment to Staminus, which is no doubt busy with more pressing matters at the moment. I’ll update this post in the event I hear back from them. It is not unusual for attackers to target Anti-DDoS providers. After all, they typically host many customers whose content or message might be offensive — even hateful — speech to many. For example, among the company’s many other clients is kkk-dot-com, the official home page of the Ku Klux Klan (KKK) white supremacist group. In addition, Staminus appears to be hosting a large number of internet relay chat (IRC) networks, text-based communities that are often the staging grounds for large-scale DDoS attack services. Source: https://krebsonsecurity.com/2016/03/hackers-target-anti-ddos-firm-staminus/