Like something from the digital ice age, distributed denial-of-service (DDoS) attacks have thawed and are roaming the cyber planet again, according to data from Google in collaboration with Arbor Networks, which provides insight into the scale and geography of recent cyber strikes. Various other reports support the same theory. Verisign estimates that a third of downtime incidents stem from DDoS attacks. These attacks are costly for both businesses and consumers, and the costs are rising. The security firm Prolexic found that attacks became bigger and more frequent in 2013 vs. 2012. There was a 58% increase in total DDoS attacks; 101% increase in application layer (Layer 7) attacks; 48% increase in infrastructure (Layer 3 &4); and 12.4% increase in average attack duration. In addition to an increase in frequency and scale, Prolexic observed some interesting metrics that illustrate significant changes in DDoS attack methodologies. Most notably was a shift away from the bulky flat packet SYN floods to UDP-based attacks and the rapid adoption of Distributed Reflection Denial-of-Service (DrDoS) attacks. A “reflection attack” is a compromise of a server’s security caused by tricking it into giving up an authentication security code, allowing a hacker to access it. These attacks are made possible when servers use a simple protocol to authenticate visitors. It exploits a common security technique known as a challenge-response authentication, which relies on the exchange of secure information between authorized user and server. The hacker logs on and receives a challenge. The server is expecting an answer in the form of the correct response but instead, the hacker creates another connection and sends the challenge back to the server. In a weak protocol, the server will send back the answer, allowing the hacker to send the answer back along the original connection to access the server. Systems that use a challenge-response authentication approach to security can be vulnerable to reflection attacks unless they are modified to address the most common security holes. Reflection attacks use a different kind of bot and require a different type of server to spoof the target IP. Prolexic believes the adoption of DrDoS attacks is likely to continue, as fewer bots are required to generate a high volume of attack traffic due to reflection and amplification techniques. Such attacks also provide anonymity by spoofing IP addresses. Another interesting observation by Prolexic is that infrastructure-based attack protocols such as SYN floods remain in steady use and are often implemented in conjunction with the reflection attacks. The US and China are popular targets simply because these two countries have more internet users than any other country, and both countries are popular choices for ideologically based attacks. The top ten DDoS originating countries according to the Prolexic Quarterly Global DDoS Attack Report Q3 2013 are: China – 62% United States – 9.06% Republic of Korea – 7.09% Brazil – 4.46% Russia – 4.45% India – 3.45% Taiwan – 2.95% Poland – 2.23% Japan – 2.11% Italy – 1.94% So, what does the future hold for DDoS attacks? Future DDoS attacks will likely be conducted through the use of booter scripts, stressor services, and related Application Programming Interfaces (API). The increasing use of this attack method will result in much more effective attacks with fewer resources required. Since these attacks are easier to employ, DrDoS attacks will become more popular. In fact, according to Prolexic, script kiddies are graduating into digital crime and assembling DDoS-for-hire sites for as little as five dollars ($5). That $5 can buy you 600 seconds of DDoS and just $50 could put a credit union down for an afternoon. Remember, it costs far less to generate an attack than to mitigate an attack. Security professionals must promote cleanup efforts and make it difficult for hackers to send money to criminals offering DDoS for hire. The financial institutions with smaller security budgets become more lucrative targets because they cannot apply the resources to identify threats. Verizon’s Chris Novak agreed: “We are seeing where DDoS is used to distract a medium-size financial institution. While they are busy fighting off the DDoS, they don’t see that terabytes of data just walked out the door. That’s scary.” DDoS is not dead. In fact, it is alive and kicking. In addition to the foray of targets, many new government programs have become recent hacker targets using DDoS. As new software is developed, it is incumbent on IT security professionals to be cognizant of potential DDoS vulnerabilities and to initiate countermeasures as quickly as possible. Source: http://www.infosecurity-magazine.com/blog/2013/11/5/jurassic-ddos/1050.aspx
Read the original:
Jurassic DDoS?


 Anonymous hackers, more precisely the ones who hacked a couple of Syrian government websites last week, have announced the start of a new campaign called Operation Throwback. ~ SoftPedia The goal of the operation is “to strike back against the oppressors of our freedom.” The hackers say they will launch distributed denial-of-service (DDOS) attacks against several high-profile websites. Today, on October 28, they plan on launching a cyberattack against the main website of T-Mobile. On October 31, they plan on attacking the website of the FBI, the NSA, Verizon, Microsoft and AT&T. The hacktivists urge their supporters to download DDOS tools and VPNs. The initiators of the operation are providing download links and instructions on how to use them. Earlier today, the hackers tested their “firepower” against the official website of the American Nazi Party. At the time of publishing NCB Interpol web site was down, apparantly from Ddos attack. Source: http://revolution-news.com/opthrowback-anonymous-to-launch-ddos-attacks-against-fbi-nsa/
Anonymous hackers, more precisely the ones who hacked a couple of Syrian government websites last week, have announced the start of a new campaign called Operation Throwback. ~ SoftPedia The goal of the operation is “to strike back against the oppressors of our freedom.” The hackers say they will launch distributed denial-of-service (DDOS) attacks against several high-profile websites. Today, on October 28, they plan on launching a cyberattack against the main website of T-Mobile. On October 31, they plan on attacking the website of the FBI, the NSA, Verizon, Microsoft and AT&T. The hacktivists urge their supporters to download DDOS tools and VPNs. The initiators of the operation are providing download links and instructions on how to use them. Earlier today, the hackers tested their “firepower” against the official website of the American Nazi Party. At the time of publishing NCB Interpol web site was down, apparantly from Ddos attack. Source: http://revolution-news.com/opthrowback-anonymous-to-launch-ddos-attacks-against-fbi-nsa/ 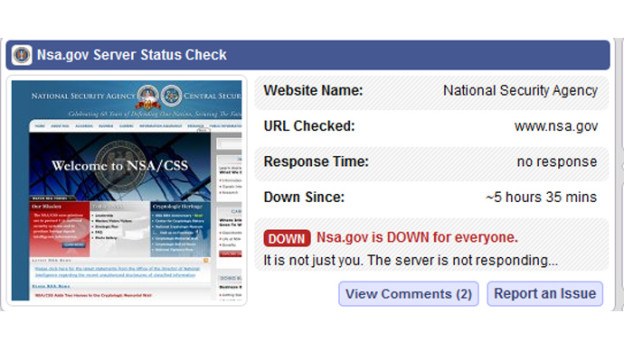
 The website for the United States National Security Agency suddenly went offline Friday. NSA.gov has been unavailable globally as of late Friday afternoon, and Twitter accounts belonging to people loosely affiliated with the Anonymous hacktivism movement have suggested they are responsible. Twitter users @AnonymousOwn3r and @TruthIzSexy both were quick to comment on the matter, and implied that a distributed denial-of-service attack, or DDoS, may have been waged as an act of protest against the NSA Allegations that those users participated in the DDoS — a method of over-loading a website with too much traffic — are currently unverified, and @AnonymousOwn3r has previously taken credit for downing websites in a similar fashion, although those claims have been largely contested. The crippling of NSA.gov comes amid a series of damning national security documents that have been disclosed without authorization by former intelligence contractor Edward Snowden. The revelations in the leaked documents have impassioned people around the globe outraged by evidence of widespread surveillance operated by the NSA, and a massive “Stop Watching Us” rally is scheduled for Saturday in Washington, DC. DDoS attacks are illegal in the United States under the Computer Fraud and Abuse Act, or CFAA, and two cases are currently underway in California and Virginia in which federal judges are weighing in on instances in which members of Anonymous allegedly used the technique to take down an array of sites during anti-copyright campaigns waged by the group in 2010 and 2011. In those cases, so-called hacktivsits are reported to have conspired together to send immense loads of traffic to targeted websites, rendering them inaccessible due to the overload.
The website for the United States National Security Agency suddenly went offline Friday. NSA.gov has been unavailable globally as of late Friday afternoon, and Twitter accounts belonging to people loosely affiliated with the Anonymous hacktivism movement have suggested they are responsible. Twitter users @AnonymousOwn3r and @TruthIzSexy both were quick to comment on the matter, and implied that a distributed denial-of-service attack, or DDoS, may have been waged as an act of protest against the NSA Allegations that those users participated in the DDoS — a method of over-loading a website with too much traffic — are currently unverified, and @AnonymousOwn3r has previously taken credit for downing websites in a similar fashion, although those claims have been largely contested. The crippling of NSA.gov comes amid a series of damning national security documents that have been disclosed without authorization by former intelligence contractor Edward Snowden. The revelations in the leaked documents have impassioned people around the globe outraged by evidence of widespread surveillance operated by the NSA, and a massive “Stop Watching Us” rally is scheduled for Saturday in Washington, DC. DDoS attacks are illegal in the United States under the Computer Fraud and Abuse Act, or CFAA, and two cases are currently underway in California and Virginia in which federal judges are weighing in on instances in which members of Anonymous allegedly used the technique to take down an array of sites during anti-copyright campaigns waged by the group in 2010 and 2011. In those cases, so-called hacktivsits are reported to have conspired together to send immense loads of traffic to targeted websites, rendering them inaccessible due to the overload.