Thursday has turned out to be somewhat of a more busy day for social trading platform eToro than usual. According to a company statement, the company’s service has been under attack by a malicious group of attackers since 07:12 GMT. After numerous complaints by customers of the firm, a thorough statement has been provided by eToro’s CEO, Yoni Assia. “I am sure that by now, most of you are already aware of the fact that our platform was under attack by a malicious group of hackers. I realize that many of you may be frustrated, angry, or simply worried following the unusual service interruptions that happened on Thursday, July 3rd and I wanted to contact you personally to apologize and explain what happened. Since 07:12 GMT, July 3rd, eToro has been the target of a criminal DDoS attack – a technique used by hackers to take an internet service offline by overloading its servers. (To read more about DDoS attacks:http://en.wikipedia.org/wiki/Denial-of-service_attack). I believe the choice to attack today was not a random one, as both you and eToro have been gearing up for today for the better part of the week. We had everything in place for you to experience a great day of trading, with the NFP announcement. I speak for everyone at eToro when I say that we deeply regret that this experience was denied you. We have robust systems in place to deal with such instances; however the scale of this particular attack caused our platform to experience significant downtime. All your personal data, including billing information, financial information and personal details is secure. More than that, throughout today we offered several alternatives for those of you who wanted to close a position, in order to give you as much control as was possible with regard to your portfolio. The status right now is that we were successful in restoring all of our services. Regrettably, as with attacks such as this, we might see more interruptions in the next few days. It is my personal goal to make sure you receive the best experience possible and I guarantee that all of us here at eToro are working around the clock to make sure this is exactly what you get. Our technical and service teams are at your disposal and are working non-stop to help each and every one of you resolve any issue affecting your personal account.” Update: On Friday morning in Europe, users have been reporting troubles with website and app functionality, and issues with logging in. Around 9BST, the status of the website was updated by the company, with eToro stating that currently it’s up and running, despite still being under attack. According to a company spokesperson, the malicious attempts are now blocked before they can affect eToro’s community. Source: http://forexmagnates.com/etoros-website-down-due-to-malicious-ddos-attacks-restored-only-to-go-dark-again/#sthash.PWXi3f61.dpuf
Continued here:
eToro’s Website down Due to Malicious DDOS Attacks, Functionality Restored


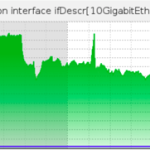 DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.
DOSarrest Internet Security had a run in with the notorious Brobot Botnet, if the name sounds familiar it’s because this bot was responsible for sporadic outages on a number of large US based financial institutions in 2013. Said to be operated by al-Qassam Cyber Fighters (AKA QCF). Botnets are born, die, grow, shrink, and morph on a daily basis, if not hourly. It’s hard to keep track of them all. Then there are particularly nasty ones that are large, powerful and sophisticated. These particular botnets have some of their zombies or bots corralled off for research purposes by a number of organizations including private Botnet hunters, government cyber surveillance departments and other large law enforcement agencies. On to the attack Why ? One of our customers is a large media outlet specializing in Middle Eastern news. With all the conflict over there these days, they must have written a few stories that the attackers were not in agreement with. How ? Using Brobot, the attackers threw millions of TCP port 80 requests at the website. Unlike a SYN attack that tries to exhaust your TCP open sessions table buffers, this attack would open and close each session/request: 1) Request a TCP connection 2) Once established they would send one character 3) Then request the TCP session to close. The problem arises when you are receiving approximately 50 million of these per second. Where ? This botnet is comprised of infected webservers using PHP, hosted on various webhosting companies around the globe. Some hosting companies seem to be represented a little more than others. One notable observation of the Brobot is that it’s very US centric, not all of the bots are based in the US but approximately 40% are, which makes filtering based on countries very difficult. When under a large TCP port 80 attack, usually it is not evenly divided across our scrubbing nodes in the US and Europe. This was different, virtually all of our upstream links in every city had pretty much the same amount of Packets Per Second and Bandwidth. I can’t ever remember seeing that in the last 7 years All links had a graph like the one above Who cares ? Within a couple of hours of the attack starting we were contacted by a private Botnet hunter that knew we were dealing with Brobot. Soon followed by visits to our website from two US federal Law enforcement agencies. Hence the title, not all botnets are equal.