DOSarrest has begun offering a Cloud based Layer 7 local and global Load balancing solution to its DDoS protection services customer base. The Load balancing service is a fully managed solution, whereby customers can create pools of servers; a pool can be 1 or many servers and can be located in multiple locations. Load balancing types available include: Round Robin, IP Hash, least connections, weighted. Other options include: By Domain or Host Header, allows customers to direct our servers to pick-up and cache content based on the domain name or host header that is being requested by the visitor. By Resource, allows customers to direct our servers to pick-up and cache content based on the resource being requested by the visitor. Mydomain.com goes to one server(s) mydomain.com/images goes to another server(s) and/or location. The load balancing solution also can be used as Active/Active -All servers are is use Or Active/Passive -some servers are only used when one or more have a failure. Health checks are all part of the service to determine if a particular server or instance is active or not. Jag Bains, CTO at DOSarrest comments “I used to be in the hosting game and when I see the advantages of our cloud based solution over a hardware based solution, this is definitely the way to go.” Bains also adds “There is no capital required, no technical expertise is needed, no single point of failure, it’s able to handle 100?s of millions of requests and can be setup in 5 minutes…top that.” General Manager at DOSarrest, Mark Teolis states “It’s a natural add-on to our DDoS protection services, which already incorporates extensive caching of customers content, this way customers can leverage any combination and location of VPS’s, Instances, private cloud and dedicated servers. I can’t see why anyone would want to buy or manage a Load balancing device again, it just doesn’t make sense anymore.” Details on this service can be found here: www.dosarrest.com/solutions/load-balancing/
See original article:
DOSarrest Rolls Out Cloud Based Layer 7 Load Balancing


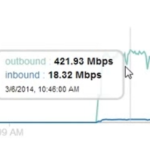 A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/
A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/