Sony’s PlayStation and Entertainment networks are back online after they were forced offline by a distributed denial-of-service (DDoS) attack, the company said late Sunday. “People can now enjoy the services on their PlayStation devices,” Sony spokesman Sid Shuman wrote in a blog post “We have seen no evidence of any intrusion to the network and no evidence of any unauthorized access to users personal information,” he said, also offering apologies for any inconvenience caused. Sony was hit by a large scale DDoS attack which struck upstream traffic routes over which Sony has no control, affecting players’ ability to log in, Sony Online Entertainment President John Smedley wrote on Twitter on Sunday. DDoS attacks attempt to crash a network by sending large amounts of data to a service provider. A group calling itself the “Lizard Squad” claimed on Twitter to be behind the attack. It said that it had “planted the ISIS flag on @Sony’s servers,” referring to the militant group that occupies parts of Syria and Iraq. Earlier on Sunday, the group tweeted directly to American Airlines writing that it had “received reports” that a flight carrying Smedley “has explosives on board.” This appeared to be a way to aggravate Sony further. Smedley had tweeted earlier that his flight had been diverted for reasons that had to do with “something about security and our cargo.” The Boeing 757, with 179 passengers and six crew which left from Dallas-Fort Worth for San Diego was diverted to Phoenix due to a “a security-related issue” and landed safely, according to American Airlines. Source: http://www.cio-asia.com/resource/networking/playstation-network-back-online-after-ddos-attack/
Tag Archives: rights
Eve Online Servers Knocked Offline Due to DDoS Attacks
Eve Online, the space-based videogame with over half a million active players, has been forced offline for more than 12 hours due to a series of cyber attacks against a cluster of its servers located in London. According to the Eve Online Status Twitter account, the first signs of trouble were seen at around 8pm on Thursday, 21 August, and by 11pm the Icelandic-based CCP Games which develops the game had confirmed the problem was due to a series of distributed denial of service (DDoS) attacks. DDoS attacks are a common tool used by criminals to flood servers with traffic in order to knock them offline and unavailable to anyone trying to access them. Some had apparently linked the offline status of the game to the recent activity of the Bardarbunga volcano in Iceland which is on the verge of erupting, however CCP Games explicitly ruled this out. The problem is affecting the Tranquility server cluster, which all Eve Online players connect to in order to play the game. This cluster of servers is based in London. Even the Eve Online wiki is inaccessible as it too is seemingly hosted on the Tranquility server. An update from CCP Games on Twitter at 8am on Friday, 22 August, simply saying: “Tranquility is currently under heavy load again” and pointing player to a forum thread. However this thread also appears to be offline at the time of publication. DDoS attacks are often used by unscrupulous companies in order to knock rivals offline for a sustained period of time, with many cyber-criminals renting out DDoS services for as little as £5-an-hour. Eve Online is a massively multiplayer online game set in the fictional world of New Eden where players pilot customisable spaceships through a galaxy of over 7,500 star systems. The game is also unique in that its developers create the structure of New Eden but then handed over control of what happens in the game to the players. The rest is a virtual world where corporations and alliances hold huge power and where huge battles can cost the equivalent of over $300,000 in real world money. Source: http://www.ibtimes.co.uk/eve-online-servers-knocked-offline-due-ddos-attacks-1462180
Continue Reading:
Eve Online Servers Knocked Offline Due to DDoS Attacks
Chinese Linux Trojan makes the jump to Windows – DDoS attacks largely aimed within China
A CHINESE TROJAN , one of the few to be written for the Linux operating system, has seemingly made the jump to Windows. First reported in May by Russian anti-malware software house Dr Web, the original malware known as “Linux.Dnsamp” is a Distributed Denial of Service (DDoS) Trojan, which, according to the company blog, transfers between Linux machines, altering the startup scripts, collecting and sending machine configuration data to the hackers’ server and then running silently waiting for orders. Now it appears that the same hackers have ported the Trojan to run in Windows as “Trojan.Dnsamp.1? The Windows version gains entry to the system under the guise of a Windows Service Test called “My Test 1?. It is then saved in the system folder of the infected machine under the name “vmware-vmx.exe”. When triggered, just like its Linux counterpart, the Trojan sends system information back to the hackers’ central server and then awaits the signal to start a DDoS attack or start downloading other malicious programs. Fortunately, the vast majority of the attacks using this method were aimed at other Chinese websites, which were attacked 28,093 times, but Dr Web warns that US websites came second with nine percent of attacks. Although the threat of malware is an everyday hazard to most computer users, to find an attack on Linux is much rarer, and to find any kind of malware that has been ported from one operating system to another is almost unheard of. In June, RSS reader service Feedly, note app Evernote and streaming music service Deezer all suffered DDoS attacks. Google is working on Project Shield, an initative designed to help smaller web servers fight off DDoS attacks. Source: http://www.theinquirer.net/inquirer/news/2361245/chinese-linux-trojan-makes-the-jump-to-windows
Follow this link:
Chinese Linux Trojan makes the jump to Windows – DDoS attacks largely aimed within China
Popcorn Time Hit By Massive DDoS Attack
A major fork of the popular Popcorn Time project is currently being subjected to a massive DDoS attack. The whole project has been hit, from the site hosting its source through to its CDN, API and DNS servers. The team tells TorrentFreak that the attack amounts to 10Gbps across their entire network. Every year sees periods when sites in the file-sharing sector are subjected to denial of service attacks. The attackers and their motives are often unknown and eventually the assaults pass away. Early in 2014 many torrent sites were hit, pushing some offline and forcing others to invest in mitigation technology. In May a torrent related host suffered similar problems. Today it’s the turn of the main open source Popcorn Time fork to face the wrath of attackers unknown. TorrentFreak spoke with members of the project including Ops manager XeonCore who told us that the attack is massive. “We are currently mitigating a large scale DDoS attack across our entire network. We are currently rerouting all traffic via some of our high bandwidth nodes and are working on imaging and getting our remaining servers back online to help deal with the load,” the team explain. The attack is project-wide with huge amounts of traffic hitting all parts of the network, starting with the site hosting the Popcorn Time source code. Attack on the source code site – 980Mbps Also under attack is the project’s CDN and API. The graph below shows one of the project’s servers located in France. The green shows the normal traffic from the API server, the blue represents the attack. Attack on the France API server – 931Mbps Not even the project’s DNS servers have remained untouched. At one point two of three DNS servers went down, with a third straining under almost 1Gbps of traffic. To be sure, a fourth DNS server was added to assist with the load. Attack on the Dutch DNS server – peaking at 880Mbps All told the whole network is being hit with almost 10Gbps of traffic, but the team is working hard to keep things operational. “We’ve added additional capacity. Our DNS servers are currently back up and running but there is still severe congestion around Europe and America. Almost 10Gbps across the entire network. Still working on mitigating. API is still online for most users!” they conclude. Nobody has yet claimed responsibility for the attack and it’s certainly possible things will remain that way. Only time will tell when the attack will subside, but the team are determined to keep their project online in the meantime. Source: http://torrentfreak.com/popcorn-time-hit-by-massive-ddos-attack-140814/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Torrentfreak+%28Torrentfreak%29
Read More:
Popcorn Time Hit By Massive DDoS Attack
Attacker could use default defibrillator password to launch DDoS attack
Jay Radcliffe freaked out the medical community in 2011 when he revealed how insulin pumps could be hacked to deliver a fatal dose of insulin (pdf). Yet at a medical device security and privacy roundtable discussion at Black Hat, Radcliffe said “it would be far easier and more likely for an attacker to sneak up behind him and deliver a fatal blow to his head with a baseball bat,” than hack his insulin pump to kill him. He did discuss hacking implantable medical devices. There are no known cases of hacking a pacemaker in anything other than fiction, but if an attacker remotely hacked a pacemaker, no one is going to dig into the death. It would be called a heart attack and that would be the end of it because “there’s no process in place right now that checks these implanted medical devices for failure or malicious activity.” Rapid7 point out, “Security often just isn’t on the radar at all for the manufacturers, the pharmaceutical regulators, or even the medical professionals that work with them.” The term “medical device” could mean a broad range of things from pacemakers to “MRI machines and echo-cardiograms and computers in the hospital running Windows XP. Mobile apps and health-related consumer-focused applications could also be considered under this broad umbrella.” John Pescatore, who previously worked at the NSA and at the U.S. Secret Service before joining SANS, released a whitepaper based on a survey about Internet of Things security. Medical machinery and personal implanted medical devices are considered to be part of the IoT. After all, people can use SHODAN to find fetal heart monitors if they are so inclined. Pescatore wrote: Internet-connected computing capabilities related to smart building and industrial control systems and medical devices were the most commonly cited concerns after consumer devices. While these type of devices don’t receive much hype with respect to the IoT in the press, the use of embedded computing in those devices (versus layered operating systems and applications in PCs and servers that IT is accustomed to managing and securing) will cause major breakage in existing IT management and IT security visibility, vulnerability assessment, configuration management and intrusion prevention processes and controls. SANS also looked at cyberthreat intelligence provided by Norse and then published a whitepaper about “Widespread Compromises Detected, Compliance Nightmare on Horizon.” Norse analyzed over 100 terabytes of daily traffic and determined there were 49,917 unique malicious events, 723 unique malicious source IP addresses and 375 U.S.-based compromised health care-related organizations. “There are many reasons why these findings are cause for alarm,” wrote Barbara Filkins. One example was: “The sheer volume of IP addresses detected in this targeted sample can be extrapolated to assume that there are, in fact, millions of compromised health care organizations, applications, devices and systems sending malicious packets from around the globe.” Those aren’t the only threats. If a person was in cardiac arrest, a defibrillator could be used to save that person’s life. But what if someone who was not authorized to use or to tweak the defibrillator settings, did so? That may be unlikely, but not impossible. Default usernames and passwords for medical devices are problematic and are “often overlooked endpoints;” they “can be easily procured by an Internet search on ‘type of device’ plus ‘default password’.” Yesterday, the National Vulnerability Database published two advisories regarding ZOLL Defibrillators. The accompanying documents from the manufacturer describe how to change default configurations on the devices. CVE-2013-7395 states: “ZOLL Defibrillator / Monitor X Series has a default (1) supervisor password and (2) service password, which allows physically proximate attackers to modify device configuration and cause a denial of service (adverse human health effects).” CVE-2007-6756 states: “ZOLL Defibrillator / Monitor M Series, E Series, and R Series have a default password for System Configuration mode, which allows physically proximate attackers to modify device configuration and cause a denial of service (adverse human health effects).” So who is responsible for deploying the fix? The FDA guidance suggests that both hospitals and manufacturers are responsible for vulnerability management. Yet Radcliffe said that makes the problem of deploying patches even more murky. He explained that “if there is a bug in an MRI machine, the hospital will have to pay to have the manufacturer come in and update all the affected machines. Of course, the hospital could install the updates themselves, but they run the risk of losing their warranty. The hospital could also decide they don’t have the budget available to pay to have the patches installed and merely wait.” Those defibrillators are not the only machines that with default passwords that potentially pose a risk. “Most devices have no security applications on them at all. Anyone can just get in and manipulate whatever they want,” stated an unnamed hospital chief information security officer in a McKinsey Report. Forbes looked into how a network-attached printer using the defaults of “admin” and “12345” for a password could be a “near perfect and silent entry point” for hackers. Lastly, Radcliffe addressed how more security on medical devices could cause patients to have less privacy. For example, if a person with an implantable medical device were to die, then “who can look at a log of his or her health before death? That’s a serious privacy concern, but what if it helps doctors find issues with IMDs, or detect evidence of foul play such as hacking?” Source: http://www.networkworld.com/article/2464010/microsoft-subnet/attacker-could-use-default-defibrillator-password-to-launch-denial-of-service.html
View post:
Attacker could use default defibrillator password to launch DDoS attack
DOSarrest Adds New DDoS Protection Node in Singapore
DOSarrest Internet Security announced today that they have expanded their DDoS protection cloud into Asia, with a new DDoS mitigation node in Singapore. The new node will work in conjunction with their existing nodes in New York, Los Angeles and London and will have the same connectivity as the others, including multiple 10 Gb/Sec uplinks to multiple carriers. Jag Bains, CTO at DOSarrest states “Having a presence in Asia allows our existing client base to cache and serve traffic closer to Asian visitors for increased performance as well as enabling us to provide excellent web performance and DDoS protection to customer’s servers located in Asia.” Bains adds “The system is incredibly scalable; this also allows us to offer a higher level of protection to all customers due to the added firepower of a new node in the region. Also the additional nodes will allow us to introduce new features and services in the coming month.” Mark Teolis, GM at DOSarrest says “We have a number of initiatives underway in the region and this will help cement these opportunities” Source: http://www.marketwired.com/press-release/dosarrest-adds-new-ddos-protection-node-in-singapore-1937355.htm
See more here:
DOSarrest Adds New DDoS Protection Node in Singapore
Irish Domains hit with denial of service attack
Web-hosting company Irish Domains was the target of a distributed denial of service (DDoS) attack on Friday, incapacitating numerous websites of its client companies. The company said that it had seen “a significant slowdown” on several services following the DDoS attack, whereby an online service is made unavailable by overwhelming it with traffic from multiple sources. The company said the slowdown was affecting email and web for some sites, adding that it “had experienced a 30x increase in inbound network connections”. “We are implementing some countermeasures to divert unwanted traffic but we expect disruption to service to continue for another while,” Irish Domains said. Brightwater Recruitment and Sherry Fitzgerald were among the companies that use the web hosting services services of Irish Domains and thus experienced issues with their sites. There are two types of DDoS attacks: a network-centric attack which overloads a service by using up bandwidth and an application-layer attack which overloads a service or database with application calls. Source: http://www.irishtimes.com/business/sectors/technology/irish-domains-hit-with-denial-of-service-attack-1.1891838
Continue reading here:
Irish Domains hit with denial of service attack

Israel-Hamas conflict sparks surge in DDoS attacks
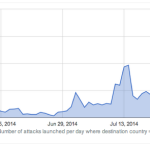 As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9
As conflict between Israel and the Palestinian militant Islamist organisation Hamas escalates, new research has revealed the impact politics has had on cyberattack trends. Tension between countries and changing political landscapes can now often be linked to cybercrime campaigns worldwide. From constant spats between the US and China to increased targeting of Syrian and Thai targets during political unrest, digital weaponry is now a key tool for groups to broadcast their own political messages, spy on governmental agencies and steal valuable data. In a new report released by Arbor Networks, anonymized traffic and DDoS attack data from over 290 ISPs that have deployed Arbor’s Peakflow SP product — collated and analyzed as part of Arbor’s ATLAS initiative — it appears that DDoS attacks are rising in number and volume as a result of the Israel-Hamas conflict. The graph below depicts the number of reported DDoS attacks initiated against Israel daily over the 1 June to 3 August period this year: Distributed Denial of Service (DDoS) attacks are used to flood a website or service with traffic to the point systems cannot cope, denying other users access to the website. Arbor detected a rise in the number of DDoS attacks targeting Israel in the first week of July, going from an average of 30 attacks per day to an average of 150 attacks initiated per day in July — peaking at 429 attacks on July 21st. Linking these cyberattacks to political situations, 30 June is when Israel publicly attributed the deaths of three kidnapped Israeli teenagers to Hamas, and on 7 July, “Operation Protective Edge” was launched by the country. As the political conflict raged on, so did the frequency of DDoS attacks until a drop occurred on 28 July lasting through 2 August. Arbor says the drop in attacks roughly correlates with cease fire talks which began 27 July. From 28 July through 2 August, there were 192 attacks recorded in total. On 3 August, the number of DDoS attacks rose sharply, with 268 attacks in total. In addition to the number of DDoS attacks over these time periods, the security researchers also noticed an increase in the peak size of these attacks. In the graph below, we can see that in June, no attacks exceeded 12Gbps. In July, seven DDoS attacks exceeded this size, with the largest peaking at 22.56Gbps on 12 July. When cease-fire talks fell apart on 3 August, the largest DDoS attack was recorded at a size of 29Gbps. The duration of DDoS attacks has also increased. In June, the average duration was 20 minutes — with a peak duration of 24 hours — and in July, the average duration was 1 hour 39 minutes. “As the intensity of the Israeli-Hamas conflict has increased, so has the number, size and duration of the DDoS attacks targeting Israel,” the researchers say. “Additionally, it even appears as if the attackers have made an effort to adhere to the “real world” calls for a cease-fire, resuming their attacks when the cease fire fell through.” Source: http://www.zdnet.com/israel-hamas-conflict-sparks-surge-in-ddos-attacks-7000032375/#ftag=RSS14dc6a9
Original post:
Israel-Hamas conflict sparks surge in DDoS attacks
RIA Novosti Website Hit by DDoS Attack
RIA Novosti’s website has fallen foul of a distributed denial-of-service (DDoS) attack by hackers, the agency’s IT specialists reported on Sunday. The mobile version of the website is currently inaccessible. Problems with the website’s full version were also reported for a short period of time. The agency’s terminal for clients has not been hampered. Unidentified hackers first attacked the website of InoSMI. When the attack was neutralized, they attempted to disrupt the work of RIA Novosti’s website. IT specialists are now working to eliminate the disruption that has caused by the attack. This is not the first cyber attack on the news agency. In May 2012, the RIA Novosti website was hit by a DDoS attack from some 2,500 IP-addresses. Another DDoS attack on the agency’s website was carried out in July 2013. Source: http://en.ria.ru/russia/20140803/191676816/RIA-Novosti-Website-Hit-by-Cyber-Attack.html
View the original here:
RIA Novosti Website Hit by DDoS Attack
Amazon cloud infested with DDoS botnets
Security researchers have found yet another exploit on the Amazon cloud computing platform through the Elasticsearch distributed search engine tool. According to analysis, hackers are able to gain access to the search engine to deploy a battalion of botnets on Amazon cloud. The vulnerability should be a cause of alarm and, therefore, merits the attention of enterprises because it could manipulate Amazon cloud platforms in an attempt to launch distributed denial of service attacks against hundreds of thousands of websites. Amazon cloud users can a representational state transfer API to search various documents through Elasticsearch, an open-source search engine server built based on Java. It is more popular among cloud environments for its distributed architecture that enables multiple nodes. Researchers found security issues on the versions 1.1.x of Elasticsearch because its API scripting lacks a mechanism to authenticate access and a sandbox security infrastructure. Therefore, anyone, including hackers, can penetrate Elasticsearch just so easy. After that, attackers could carry out several malicious activities using Elasticsearch’s scripting capability such as carrying out arbitrary code on the server. As of now there is no patch coming from the developers of Elasticsearch. Nonetheless, versions 1.2.0 and up are safe from being exploited by hackers. New offshoots of Mayday Trojan for Linux has been spotted over the past week and the malware already launched DDoS attacks against targets DNS amplification. A Mayday variant was reported to be running on an Amazon server that has been compromised through the Elasticsearch exploit, though there are other platforms that could have been potentially manipulated. However, the Mayday variant did not resort to DNS amplification on the compromised EC2 instances. Instead it was used to launch attacks by flooding several websites with UDP traffic. As a result, many regional banking institutions in the United States and electronics companies in Japan had to transfer their IP addresses to DDoS mitigation service vendors. The Amazon EC2-run virtual machines were also reported to have been attacked by hackers through a CVE-2014-3120 exploit in the 1.1.x versions of Elasticsearch. Researchers observed that many commercial enterprises still use those versions. According also to security researchers, attackers have changed proof-of-concept exploit code for CVE-2014-3120 to install a Web shell developed based on Perl. A Web shell is a script that enables hackers to deploy Linux shell commands backdoor through the Web. The script was then further manipulated to download a fresh variant of the Mayday DDoS botnet. Amazon has already notified its customers about the issue. Source: http://www.techwalls.com/amazon-cloud-infested-ddos-botnets/
See more here:
Amazon cloud infested with DDoS botnets
