One of the hot topics at the Infosecurity Europe show – held in London this week – is the scale and complexity of the latest attacks against corporates. Whilst several research operations and vendors competed with each other to come up with reports on how bad the attack landscape is at the moment, the real question that C level executives attending the event want to know is: how bad are the attacks really – and what can I do to defend against the threat? According to Ian Pratt, the co-founder of Bromium Labs, the threats situation is potentially quite serious, as his research team has uncovered a new type of attack vector called the Kernel Kracker, which is what some experts call a layered attack. The attack exploits a vulnerability in the Windows operating system kernel and allows the attacker to gain admin/system level privileges on the host system, so allowing them effectively peel away the various layers of security the company has installed. Having said this, Pratt says that the use of multiple layers of security to protect an organisation’s IT resources is still a very viable defence approach, as, although no set of security layers is ever going to reach 100 percent protection, the use of multiple layers is still a lot better than the old single-suite option of yesteryear. “The underlying problem is that all commodity operating systems are now too big to protect in their entirety,” he said, adding that – as an example – Windows XP had more than 100 patches applied to it last year by Microsoft. Against this backdrop, Pratt argues that the best solution is create virtual instances of a given operating system environment, taking the concept of virtual machines to its logical conclusion. This means, he says, that even if the defences fail and an attack succeeds, its effects are severely limited to the privileges assigned to the given Web browser session. After the session on a given Web resource finishes, the virtual machine collapses the session and a fresh one is started for the set Web site. “You can let the exploit happen, and its effects are limited,” he explained, adding that he fully expects cybercriminals to come up with new attack vectors on a constant basis. Will there ever come a time when it ceases to become viable for the cybercriminals to develop new attack vectors to attack corporate IT systems, we asked him. That time, he replied, is still a very long way off, as new methodologies will arrive all the time. “Over the last 18 months, it’s all been about Java. That is going to change, and you will see a new set of security threats being used,” he said. Jag Bains, CTO of DOSArrest, agreed that the threat landscape will continue to evolve from its current mix of DDoS attacks and operating system-specific vectors. “Today you’re seeing customised Javascript DDoS attacks – I think this attack vector is going to continue to evolve, as hackers continue to have the motivation to attack a corporate system,” he explained. David Gibson, vice president of Varonis Systems, agreed that cybercriminal attack vectors are evolving, but cautioned that the fundamental problem remains the volume of data to which users of IT systems have access. “We had a meeting with a client recently where users had the same levels of access rights [to data] as their high level management. As a result, we discovered that volumes of company data were being exfiltrated from the system, despite their use of multiple layers of security,” he said. It’s against this backdrop, he told SCMagazineUK.com , that he fully expects attacks to evolve for the foreseeable future, but he adds that the inside attacker is likely to be the “next big thing” in the security attacks arena. “For this reason, I am of the opinion that companies must continue to develop the technical controls required to protect the data in their organisation, as well as evolving the security being used to defend the IT resource,” he concluded. Source: http://www.scmagazineuk.com/infosecurity-europe-are-cybercriminals-winning-the-security-game/article/344740/
View post:
Infosecurity Europe: Are cybercriminals winning the security game?


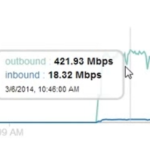 A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/
A researcher discovered a flaw in the section “notes” of the social network Facebook that could be exploited by anyone to conduct a powerful DDoS attack. The Security researcher Chaman Thapa, also known as chr13, discovered a vulnerability in the section ‘Notes’ of the popular social network Facebook that could be exploited by anyone to launch the distributed denial-of-service (DDoS) attack of more than 800 Mbps Bandwidth on any website. Chaman Thapa demonstrated that simply reading a ‘Note’ created by anyone on the Facebook platform an attacker could automatically generate malicious traffic against a target. The researcher published a blog post to describe the vulnerability, he exploited the possibility to include tags inside the post to allow the creation of notes that have images from any source. The attack scenario is very simple, Facebook downloads external images from the original source for the first time only, to improve the performance it stores them in the cache for successive uses. If the image url has dynamic parameters, Facebook is not able to store the image in cache and practically it download all the images included in a note each time whenever anybody view the note. “Facebook Notes allows users to include tags. Whenever a tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood.” Let’s see the DDoS attack scenario described by Chaman Thapa, let’s chose the target website “ target.com” which include a large image on its server (e.g. 1Mb). The researcher creates a Facebook Note which includes the above image multiple times with dynamic parameters, and some text. Facebook servers are forced to download 1 MB of file 1000 times in one page view (It has been estimated that each note is now responsible for 1000+ http requests). If 100 Facebook users are reading the same note at the same time, then Facebook servers will be forced to download 1 x 1000 x 100 = 100,000 Mb or 97.65Gb bandwidth within few seconds from the targeted servers. In the image below is reported the graph for the 400 Mbps traffic generated from 127 Facebook servers in the proof-of-concept made by Thapa by attacking on his own web server. Following the description provided in the post by the Chaman Thapa. Steps to re-create the bug as reported to Facebook Bug Bounty on March 03, 2014. Step 1. Create a list of unique img tags as one tag is crawled only once .. Step 2. Use m.facebook.com to create the notes. It silently truncates the notes to a fixed length. Step 3. Create several notes from the same user or different user. Each note is now responsible for 1000+ http request. Step 4. View all the notes at the same time. The target server is observed to have massive http get flood. Thousands of get request are sent to a single server in a couple of seconds. Total number of facebook servers accessing in parallel is 100+. The researcher explained that the amplification factor of the DDoS attack depends on the dimension of the image downloaded, it could be even higher if the attacker includes in the note a pdf or a video. “A scenario of traffic amplification: when the image is replaced by a pdf or video of larger size, Facebook would crawl a huge file but the user gets nothing.” “Each Note supports 1000+ links and Facebook blocks a user after creating around 100 Notes in a short span. Since there is no captcha for note creation, all of this can be automated and an attacker could easily prepare hundreds of notes using multiple users until the time of attack when all of them is viewed at once.” noted Chaman Thapa. There is the concrete risk that a bad actor creates hundreds of notes with specially crafted script using multiple users at the same time, resulting a powerful DDoS attack. The alarming news is that the flaw is still unpached and Facebook has no plans to fix it. “ In the end, the conclusion is that there’s no real way to us fix this that would stop attacks against small consumer grade sites without also significantly degrading the overall functionality, ” replied Facebook to the researcher. Click here to read the entire article. Source: http://www.arie.co.za/how-to-abuse-facebook-feature-to-conduct-powerful-ddos-attack/