Threats, risks and dangers related to cyber-security are changing. CIOs must respond with a well-defined strategy and the right mix of processes and tools. Over the past few years, digital technologies have rippled through the business world and unleashed unprecedented innovation and disruption. Yet today’s technology framework also has put businesses in the crosshairs and created new levels of risk. No longer are cyber-threats thwarted by clearly defined perimeters such as firewalls. No longer are malware and cyber-attacks blocked by traditional security tools designed to identify specific viruses and code. “It’s an entirely different landscape,” observes Oswin Deally, vice president of cyber-security at consulting firm Capgemini. To be sure, mobility, clouds, the internet of things (IoT) and the increasingly interconnected nature of business and IT systems have radically changed the stakes. There’s a growing need for security transformation. Yet, at the same time, attacks are becoming more insidious and sophisticated. Phishing, spear-phishing, whaling, ransomware, hacking, hacktivism and corporate espionage are now mainstream problems. Data breaches and DDoS attacks are a daily concern. “Cyber-security has moved from a compliance and regulatory topic to front-page headline news,” says Dan Logan, director of enterprise and security architecture for Tata Consultancy Services (TCS). No Space Is Safe The scope of today’s cyber-security challenge is mind-boggling. Gartner predicts that more than 8.4 billion IoT devices will be used in 2017, and the number will swell to more than 20 billion by 2020. Meanwhile, 74 percent of organizations now store some, if not all, sensitive data in the public cloud, according to a February 2017 Intel Security study. Not surprisingly, the stakes are growing, and achieving digital transformation while ensuring security is not a simple task. An October 2016 Ponemon Institute study found that the average cost of cyber-crime to a large organization in the United States rose to more than $17 million in 2016. An interconnected world with intertwined data means that threats can come from anywhere at any time. Business disruption, information loss, a diminished brand image and revenue, and damage to equipment are constant risks. Nevertheless, organizations are struggling to keep up. Ponemon points out that only 39 percent of companies deploy advanced backup and recovery operations, though it reduces the average cost of cyber-crime by nearly $2 million. Similarly, only 28 percent of companies have a formal information governance program, though this typically reduces the cost of cyber-crime by nearly $1 million. Capgemini’s Deally says that a starting point for dealing with today’s threat landscape is to recognize that there are two primary areas to focus on: business-driven events and threat-driven events. The former revolves around things like digital commerce, innovation, intellectual property, products and supply chains that present targets and create risks for the enterprise. The latter encompasses attack methods and vectors, including email, mobile devices, the IoT, and other systems and software. “It is becoming more and more of a borderless world where the devices that drive productivity also represent risk,” he points out. CIOs and other enterprise leaders must understand business and technology intersection points and how they introduce risks at various levels—from application security to APIs and network design to clouds. It’s also important to clearly understand business and data assets and identify priorities in terms of value, sensitivity and risk. Not all data is created equal and not all systems require equal protection. This approach, when layered over specific industry risks, begins to deliver some clarity about how and where to focus a cyber-security strategy and select the right protections and processes. o be sure, cyber-security must take a multilayered approach, and it must focus on defense-in-depth. One of today’s challenges is that intruders may gain entry to a network through a vulnerability or breach and worm their way through systems and files over a period of weeks, months or years. These advanced persistent threats (APTs) use multiple tools, technologies and methods to take intrusions to a deeper and more dangerous level. In some cases, the intruders may never make their presence known. They simply pull information—everything from employee or customer data to intellectual property—to perpetuate attacks that monetize their efforts. Secure Horizons CIOs and other enterprise leaders must ultimately focus on strategies that rely on multiple tools, technologies and methods to address the problem on several fronts. This may include everything from reviewing privileges and reexamining authentication methods to analyzing coding practices and reviewing the way encryption is used for data at rest and in transit. It could also address everything from vendor relationships to coding practices. For example, as organizations migrate to DevOps, it’s possible to use automated code scanning to detect vulnerabilities before software goes live. In addition, emerging cyber-security tools use artificial intelligence (AI), machine learning or deep learning, along with analytics, to detect unusual behavior and patterns. If an employee logs in at an unusual time from an unknown device or IP address, the system may require re-authentication. However, TCS’ Logan also stresses the urgency of employee education and training. Many of today’s breaches are caused by inattentive employees, sometimes even those in the C-suite, who click a link and infect a system with malware, including ransomware. In other cases, employees circumvent policies because they interfere with their work, or they turn to shadow IT and rogue applications to complete work easier or faster. “Ongoing employee education about phishing—and the use of anti-phishing campaigns that send test emails to users and then respond to clicks with just-in-time education—is an effective addition to employee security awareness efforts,” Logan says. Likewise, intelligence sharing services can help organizations identify new risks quickly. In the end, Logan says that a simple mnemonic is useful for security transformation: ARM. This translates to assess, remediate and monitor. Best-practice organizations embed cyber-security into the foundation of day-to-day IT operations. They have robust backup and recovery systems in place to guard against ransomware and other problems. They handle basic blocking and tackling but also examine how more advanced tools, technologies and practices can boost protection. To be sure, the road to security transformation is long and winding. “A world-class organization must excel at the basics of identity management, vulnerability management, configuration management, incident management, incident response, backup and recovery,” Logan explains. Capgemini’s Deally adds: “From a CIO’s perspective, it’s essential to look at what are you doing from a business perspective and build security protections from there. The most important question—and the one to work backward from in every case—is, ‘How can I best mitigate risk?’ Source: http://www.cioinsight.com/security/recognizing-the-new-face-of-cyber-security.html
Read More:
Recognizing the New Face of Cyber-Security


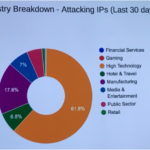 TAIPEI (Taiwan News)—Most denial-of-service (DDoS) attacks launched by hackers from Feb. 15 to March 14, 2017 in Taiwan targeted the high-tech industry, according to statistics compiled by leading global content delivery network provider Akamai Technologies. Industries in Taiwan that were most severely attacked by hackers were the high technology industry (61.8 percent), manufacturing industry (17.6 percent) and the financial services industry (7 percent), according to statistics compiled by Akamai’s intelligent platform that delivers 30 percent of the global Internet traffic. Industries in Taiwan under DDoS attacks from February 15 to March 14, 2017. (Taiwan News) The majority of the hacks were launched from IP addresses in Taiwan, followed by Alabama in the U.S., and Brazil. “It is often a misconception that most attacks are launched from abroad,” said Akamai’s Security Business Unit director Amol Mathur. “Attacks are coming both domestic and outside.” The premium CDN provider works customizes solutions for clients from different industries in Taiwan, including hospitality, banking, travel and airline services. Taiwan’s financial institutes are still recovering from a cybersecurity scare last month, in which 15 banks received threats from an anonymous hacker group to shell out 10 Bitcoins each (equivalent to US$10,466), or brace themselves for DDoS attacks that would compromise their server systems. DDoS attacks launched by hackers often compromise institute’s servers data processing capacity by delivering a sudden deluge of data that overtakes bandwidth resources, for instance if the company server bandwidth only allows 10 Gigabyte per second (Gbps) of capacity it can be paralyzed by a 100 Gbps attack. Hackers might use DDoS as a distraction to conceal other malign operations, such as stealing personal information or credential theft, added Mathur. Industries affected by hacker attacks vary monthly, depending on whether there is a major geopolitical event, said Mathur. For instance global hacker group Anonymous took down the London Stock Exchange system for two hours as part of its campaign against global central banks in June 2016. Mathur advised banks should not heed hacker demands to pay ransom. “In real life you would not pay ransom, so why would you pay hackers,” he said. The cybersecurity expert noted a rise in DDoS attacks globally during the fourth quarter of 2016, and pointed out DDoS attacks data size was increasing exponentially every quarter. Globally, attacks over 100 Gbps jumped 140 percent year-on-year during 4Q16, with the largest-size attack recorded reaching 517 Gbps, according to the Akamai “Fourth quarter 2016 State of the Internet/Security Report.” Mathur noted the cause of increased DDoS attacks was partly due to easy access for people to rent bots online, for as cheap as US$10 by going to a site and simply keying in the website address. Hackers can generate a monthly income of US$180,000 to US$200,000 from bot rentals. It remains extremely difficult for law enforcement agencies from a single country to track down hackers that spread the attacks launched by rented bots around the globe, and hide behind the protection of anonymity offered by the dark web. Additionally, the preferred Bitcoin currency used for business transactions by hackers is hard to trace to an IP address, explained Mathur. Introduction of mobile devices, mobile payment, IP surveillance cameras and emerging Internet of Things (IoT) trends introduce new cybersecurity vulnerabilities as hackers can utilize attacks through large number of connected devices. The Mirai bot for instance exposed vulnerabilities in the default user administrator name and passwords used by thousands of connected IP surveillance cameras and their DVR worldwide, said Mathur. He urged the IoT industry to form a joint standard, and for countries to start implementing regulations that set cybersecurity standards for connected devices. Hackers are also finding ways to target vulnerabilities in smartphone application programming interface (API) to obtain credentials, and data from mobile transactions. Apple Pay and some other mobile payment technologies periodically publish white papers announcing how it is securing data, but are mostly for tech savvy readers, said Mathur. One way consumers can safeguard credit card transactions is to check if the online shopping sites or App they use have The Payment Card Industry Data Security Standard (PCI DSS), noted Mathur. The proprietary information security standard launched nearly a decade ago by major credit card companies Visa, MasterCard, American Express, JCB and others follows a stringent standard and heavily fines companies that do not follow its compliance. Source: http://www.taiwannews.com.tw/en/news/3117326
TAIPEI (Taiwan News)—Most denial-of-service (DDoS) attacks launched by hackers from Feb. 15 to March 14, 2017 in Taiwan targeted the high-tech industry, according to statistics compiled by leading global content delivery network provider Akamai Technologies. Industries in Taiwan that were most severely attacked by hackers were the high technology industry (61.8 percent), manufacturing industry (17.6 percent) and the financial services industry (7 percent), according to statistics compiled by Akamai’s intelligent platform that delivers 30 percent of the global Internet traffic. Industries in Taiwan under DDoS attacks from February 15 to March 14, 2017. (Taiwan News) The majority of the hacks were launched from IP addresses in Taiwan, followed by Alabama in the U.S., and Brazil. “It is often a misconception that most attacks are launched from abroad,” said Akamai’s Security Business Unit director Amol Mathur. “Attacks are coming both domestic and outside.” The premium CDN provider works customizes solutions for clients from different industries in Taiwan, including hospitality, banking, travel and airline services. Taiwan’s financial institutes are still recovering from a cybersecurity scare last month, in which 15 banks received threats from an anonymous hacker group to shell out 10 Bitcoins each (equivalent to US$10,466), or brace themselves for DDoS attacks that would compromise their server systems. DDoS attacks launched by hackers often compromise institute’s servers data processing capacity by delivering a sudden deluge of data that overtakes bandwidth resources, for instance if the company server bandwidth only allows 10 Gigabyte per second (Gbps) of capacity it can be paralyzed by a 100 Gbps attack. Hackers might use DDoS as a distraction to conceal other malign operations, such as stealing personal information or credential theft, added Mathur. Industries affected by hacker attacks vary monthly, depending on whether there is a major geopolitical event, said Mathur. For instance global hacker group Anonymous took down the London Stock Exchange system for two hours as part of its campaign against global central banks in June 2016. Mathur advised banks should not heed hacker demands to pay ransom. “In real life you would not pay ransom, so why would you pay hackers,” he said. The cybersecurity expert noted a rise in DDoS attacks globally during the fourth quarter of 2016, and pointed out DDoS attacks data size was increasing exponentially every quarter. Globally, attacks over 100 Gbps jumped 140 percent year-on-year during 4Q16, with the largest-size attack recorded reaching 517 Gbps, according to the Akamai “Fourth quarter 2016 State of the Internet/Security Report.” Mathur noted the cause of increased DDoS attacks was partly due to easy access for people to rent bots online, for as cheap as US$10 by going to a site and simply keying in the website address. Hackers can generate a monthly income of US$180,000 to US$200,000 from bot rentals. It remains extremely difficult for law enforcement agencies from a single country to track down hackers that spread the attacks launched by rented bots around the globe, and hide behind the protection of anonymity offered by the dark web. Additionally, the preferred Bitcoin currency used for business transactions by hackers is hard to trace to an IP address, explained Mathur. Introduction of mobile devices, mobile payment, IP surveillance cameras and emerging Internet of Things (IoT) trends introduce new cybersecurity vulnerabilities as hackers can utilize attacks through large number of connected devices. The Mirai bot for instance exposed vulnerabilities in the default user administrator name and passwords used by thousands of connected IP surveillance cameras and their DVR worldwide, said Mathur. He urged the IoT industry to form a joint standard, and for countries to start implementing regulations that set cybersecurity standards for connected devices. Hackers are also finding ways to target vulnerabilities in smartphone application programming interface (API) to obtain credentials, and data from mobile transactions. Apple Pay and some other mobile payment technologies periodically publish white papers announcing how it is securing data, but are mostly for tech savvy readers, said Mathur. One way consumers can safeguard credit card transactions is to check if the online shopping sites or App they use have The Payment Card Industry Data Security Standard (PCI DSS), noted Mathur. The proprietary information security standard launched nearly a decade ago by major credit card companies Visa, MasterCard, American Express, JCB and others follows a stringent standard and heavily fines companies that do not follow its compliance. Source: http://www.taiwannews.com.tw/en/news/3117326