In the first two weeks of April, sudden spikes of traffic started hitting gaming and gambling sites in Hong Kong. The increased rush weren’t anxious gamers looking to place bets, but a DDoS attack designed to take the sites offline. The unusual activity hounding sites in Hong Kong was caught by Security Engineering and Response Team at Arbor Networks, a cyber security firm based in the U.S. A massive influx of traffic from China starting pouring into the territory on April 6, and carried out in blasts through April 13. During that time frame, Hong Kong was the top destination for targeted attacks, topping the U.S., which routinely receives the highest percentage of DDoS attacks. It’s uncommon for Hong Kong to attract such attention from a DDoS, or Distributed Denial of Service attack. The types of attacks use coordinated machines to direct an overwhelming amount of traffic at a single target. These attacks—often carried out by massive networks of compromised internet-connected devices coordinated as part of a botnet—can often force a service offline. DDoS attacks are difficult to mitigate because they cannot be stopped by simply blocking one source. Because the traffic comes from anywhere from dozens to thousands of individual locations, it can also prove next to impossible to distinguish legitimate traffic from attack traffic or determine the origin of the attack. That anomalous activity detected by Arbor Networks—during which Hong Kong received 28 and 39 percent of all attacks greater than 10 Gbps in size in the two respective weeks—caught the eye of Kirk Soluk, the manager of the company’s Threat Intelligence and Response team. According to Soluk’s analysis, the attack was likely an attempted extortion attack, designed to knock a target offline until they are willing to pay to make the attack stop. “Gambling sites and gaming sites that have a financial component are a particularly attractive target,” Soluk told International Business Times, “due to the money the sites stand to lose if they are not available.” Extortion attempts have been on the rise in recent years, in part because of the wider availability of tools used to perform such attacks and in part because businesses and individuals are more reliant on digital services—trusting digital systems with sensitive data and financial information. According to a recent report by Symantec, ransomware attacks, which attempt to extort money from individual users and businesses by encrypting their files and demanding payment to decrypt them, rose by 36 percent in 2016—and the average ransom cost increased by 266 percent from the previous year. DDoS attacks are often used to hit larger organizations rather than single users or small networks like ransomware, but it can have an impact on others beyond the intended target. Soluk warned that DDoS attacks could potentially compromise users of an attacked site and in some cases even put them at physical risk, like in a November 2016 attack in Finland that damaged the heating systems of residential properties in the dead of winter. “Fortunately, we haven’t seen a large-scale critical infrastructure outage directly attributed to a DDoS attack but it’s certainly not out of the realm of possibility,” Soluk said. “More notable are outages that result in financial losses for organizations whose Internet presence is taken offline as well as inconveniences for end users wishing to purchase goods or even play games.” There is collateral in any attack of such magnitude, and the bombardment of Hong Kong gaming sites was no exception. While those sites took the brunt of the traffic, a number of other sites also got hit, including two domains belonging to hospitals. Given that 29 total online gambling and gaming sites were hit in the same surge of traffic, it seems obvious those were the true targets. What is less clear is who carried out the attack. The vast majority of the traffic came from China, and in some cases such a direct stream directed at domains of one territory can be indicative of cyber warfare between states. DDoS attacks have become tools of war, and have been seen in attacks like the one launched against the former Soviet Republic of Estonia. Much of the nation was taken offline by a DDoS attack that hit government and private sector servers after Estonian government decided to move the Bronze Warrior, a Soviet World War II memorial, and angered Russian leadership. It’s also noteworthy that Hong Kong itself has been hit by DDoS attacks before. Those came in 2014 following a growing pro-democracy movement that was angered in part by China’s influence in the territory’s elections. Despite the history, and the onslaught of traffic driven from China, there isn’t much indication that the attack on Hong Kong gaming sites was in any way a politically motivated attack. “Geography has to be taken in proper context, particularly when considering the source of an attack,” Soluk explained. “It is easy for an attacker sitting anywhere in the world to launch a DDoS attack from anywhere else in world.” Because of the targets of the attack, Soluk concluded the hit on Hong Kong gaming sites was more likely to be financially motivated than part of an ongoing geopolitical battle between two territories. The attacks have ceased and the dust has cleared from the torrential traffic, but it’s not clear if that means the targets are in the clear. The attacks came out of nowhere, spiking with little indication and disappearing back into the ether. That type of uncertainty can’t be planned for, but Soluk said it can be mitigated to some degree with preparedness. He advised sites and online services to follow best current practices for architecting and protecting network infrastructure, including having trained staff that regularly conduct DDoS war games to test the system and utilizing an Intelligent DDoS Mitigation System (IDMS) to help counteract an attack. Source: http://www.ibtimes.com/ddos-attack-gaming-gambling-sites-hong-kong-believed-be-extortion-attempt-2535523
Read More:
DDoS Attack On Gaming, Gambling Sites In Hong Kong Believed To Be Extortion Attempt


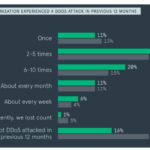 Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/