You’ve seen the splashy headlines about web services getting taken down by DDoS, or Distributed-Denial-of-Service Attacks, but have you ever worried about these attacks taking down your firm’s site? As recently as October 2016, internet traffic company Dyn was the victim of several DDoS attacks, which shut down websites and services across the East Coast. With the increasingly popularity of Internet of Things devices, which includes any everyday device that’s now connected to the web, these DDoS attacks are increasing in frequency. Hackers create armies of these devices, which are infected with malware, that will attack any given service. The attack works by having multiple devices flood the bandwidth of a service or website with so much traffic that the service is no longer available to normal users. Neustar, a global DDoS protection and cybersecurity firm, releases a yearly study about the impacts of DDoS attacks on businesses. Neustar’s first quarter 2017 report, found that the number of attacks doubled between 2017 and 2016. DDoS attacks are only getting larger, the report states, and the 1,010 respondents collectively experienced a minimum revenue risk from the attacks in excess of $2.2 billion during the previous 12 months. On Thursday, during the Arizona Technology Council 2017 Cybersecurity Summit, Mark Goldenberg, security solutions architect at CenturyLink, presented six steps regarding the possibility of a DDoS attack. In 2012, during the Occupy Wall Street movement, many financial institutions were victims of DDoS attacks, Goldenberg said. The attacks prompted the Federal Financial Institutions Examination Council to release these six steps. Goldenberg said these steps can apply to any firm in regards to a DDoS attack. Step 1: Assess information security risk Goldenberg said that a company should understand its online assets by maintaining an ongoing program to assess information security risk. Take time to review which publicly-based Internet assets are critical to your business that could be affected by a DDoS attack, he said. Some firms have services on a website that can be down for a period of time, but there are other parts of the website that are absolutely vital to your firm’s day-to-day operations, Goldenberg said. Understanding what’s vital and what isn’t will help your business make the right decisions in the event of an attack, he said. Step 2: Monitor Internet traffic to your site(s) in order to detect attacks Talk to your team about what sort of visibility your firm has, whether it’s sources of internet traffic or what types of internet traffic parts of your site is getting, Goldenberg said. Knowing your site’s analytics will let you and your team know where to look in the event of a cyberattack, which in turn will let your team know what kind of resources to bring to the table, Goldenberg said. Step 3: Be ready and notify Make sure your team has an incident response plan, which includes alerting service providers, especially internet providers, Goldenberg said. If your firm has multiple internet providers, Goldneberg said it’s important to know how to coordinate between the providers in the event of a DDoS attack. Your internet provider(s) won’t do anything independent of you, Goldenberg said. And be ready to know when and how to notify your customers when you’re under attack. “A communication plan is key,” Goldenberg said. Step 4: Ensure sufficient staffing for the duration of the DDoS attack When your firm is undergoing a DDoS attack, it’s important to have both your security and network team at the table working together. Make sure, though, that your security team is on the alert for potential breaches. “The perpetrators of the attack understand that when they launch an attack, it’s a priority issue for you to get your network back available,” Goldenberg said. If your security team isn’t on the lookout for breaches at the same time, your data could be compromised during the attack. Step 5: Share that information After your attack, you may want to share the information about it to fellow businesses within your industry. Goldenberg said the Arizona Technology Council is the perfect example of a group to share this information with. “If one peer is hit with a DDoS attack today, it could mean that you’re going to be next,” Goldenberg said. Step 6: Evaluate gaps in your response and adjust After the attack, it’s time to come together to find out what kind of gaps your firm may still have and to learn from it, Goldenberg said. “What you do today has to be reviewed with the team on a regular basis and kept up to date. If you’re able to withstand a low level attack today, regroup with the team, understand where your strengths are, where your weaknesses are, so you can plan for the larger attack down the road.” Source: http://azbigmedia.com/ab/6-steps-preparing-ddos-attack
Read More:
6 steps to reduce your risk of a DDoS attack


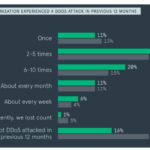 Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
Neustar says that the enterprise is finding it more difficult than ever to stem the financial cost of DDoS campaigns. DDoS campaigns are on the rise and the enterprise can now expect a bill of at least $2.5 million every time they become a victim. The mere threat of a distributed denial-of-service (DDoS) attack can cause businesses to sweat, and in some cases, cybercriminals earn big moneyjust by threatening a company with a future attack unless they pay protection fees. However, while some threat actors may just pretend, others use DDoS attacks to disrupt businesses by flooding a domain with illegitimate traffic. This kind of attack may also be used make a political statement or as a means of censorship. Whatever the reason, DDoS attack rates are increasing and businesses are being forced to pay out for damage control and repair, as they are losing more revenue through online service disruption than ever before. According to web analytics firm Neustar’s latest DDoS attack trends report, in addition to a survey conducted by Neustar and Harris Interactive of over 1,000 executives from enterprise firms, while the first quarter of the year is generally considered “pre-season” for these attacks, the company is already seeing “significant increases in average attack size and variety of attack vectors.” To date this year, 849 out of 1,010 enterprise companies — 84 percent — included in the research have experienced at least one DDoS attack in the last 12 months, up from 73 percent in 2016. In total, 86 percent of these businesses were struck with multiple DDoS attacks over the past 12 months, of which 63 percent said the loss of revenue at peak times caused by DDoS disruption can sometimes reach beyond $100,000 an hour. This is a significant increase from 50 percent of companies which said so much revenue was at stake in 2016, but to make matters worse, 43 percent of respondents admitted the financial loss per hour is closer to $250,000. Neustar says that the respondents to the survey have collectively lost over $2.2 billion dollars during the past 12 months, which is a minimum of $2.5 million each on average across 849 organizations. According to Neustar’s internal security data, 45 percent of DDoS attacks were of an attack strength of over 10 Gbps per second, and 15 percent of attacks reached at least 50 Gbps which is almost double the rate reported in 2016. Threat actors are utilizing a number of new techniques to disrupt businesses, including Generic Routing Encapsulation (GRE) based flood attacks and Connectionless Lightweight Directory Access Protocol (CLDAP) reflection techniques. The matter is made worse by the increased use of Internet of Things (IoT) connected devices in the enterprise, which when left unsecured, can act as pathways to penetrate business network defenses as well as become slave nodes themselves which are included in the DDoS traffic stream. Mitigating DDoS attacks is not just a challenge for businesses, but public figures and speakers, too. Back in 2016, prominent security researcher Brian Krebs found himself to be the target of a massive DDoS attack — powered by the Mirai botnet — which was close to disrupting service to his website. Web provider Akamai was able to fend off the attack, but due to the size and cost, was unable to protect him again. As a result, Google’s Project Shield, a free DDoS protection service, offered to shelter the websiteagainst future attacks. Alongside the report’s release, Neustar has revealed plans to increase the firm’s global DDoS mitigation service capacity to 3 Tbps and hopes to extend this capacity to 10 Tbps by early 2018. Source: http://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/