Keeping your data secure is more important than ever, but it seems like there’s a new wide-scale data breach every other week. In this article, David Mytton discusses what developers can do to prepare for what’s fast becoming inevitable. Cyber security isn’t something that can be ignored anymore or treated as a luxury concern: recent cyber attacks in the UK have shown that no one is immune. The stats are worrying – in 2016, two thirds of large businesses had a cyber attack or breach, according to Government research. Accenture paints a bleaker picture suggesting that two thirds of companies globally face these attacks weekly, or even daily. According to the Government’s 2016 cyber security breaches survey, only a third of firms have cyber security policies in place and only 10% have an emergency plan. Given management isn’t handling the threat proactively, developers and operations specialists are increasingly having to take the initiative on matters of cybersecurity. This article covers some essential priorities developers should be aware of if they want their company to be prepared for attack. Know your plan There’s no predicting when a cyber attack might come, whether it be in the form of a DDoS, a virus, malware or phishing. It’s therefore important to be constantly vigilant, and prepared for incidents when they do occur. Senior leadership in your company should be proactive when laying out a plan in the event of an attack or other breach, however this might not always be the case. No matter what your position is within your company, there are preemptive actions you can take on a regular basis to ensure that you’re adequately prepared. If you’re in an Ops team, make sure you’re encouraging your team to test your backups regularly. There’s little use having backups if you’re unable to actually restore from them, as GitLab learned to their detriment earlier in the year. Use simulations and practice runs to ensure that everyone on your team knows what they’re doing, and have a checklist in place for yourself and your colleagues to make sure that nothing gets missed. For example, a DDoS attack may begin with a monitoring alert to let you know your application is slow. Your checklist would start with the initial diagnostics to pinpoint the cause, but as soon as you discover it is a DDoS attack then the security response plan should take over. If you happen to be on-call, make sure you’ve got all the tools you need to act promptly to handle the issue. This might involve letting your more senior colleagues know about the issue, as well as requesting appropriate assistance from your security vendors. Communication is always one of the deciding factors in whether a crisis can be contained effectively. As a developer or operations specialist, it’s important to be vocal with your managers about any lack of clarity in your plan, and ensure that there are clear lines of communication and responsibility so that, when the worst does occur, you and your colleagues feel clear to jump into action quickly. Remember your limits It might sound obvious, but it’s worth remembering: in a cyber attack or catastrophic incident, there is only so much you yourself can do. Too many developers and operations staff fall prey to a culture of being ‘superheroes’, encouraged (often through beer and pizza) to stay as late as they can and work as long as possible on fixes to particular issues. The truth is, humans make mistakes. Amazon’s recent AWS S3 outage is a good example: swathes of the internet were taken offline due to one typo. If you’re on-call while a cyber attack occurs there’s no denying you’re likely to work long hours at odd times of the day, and this can put a real strain on you, both mentally and physically. This strain can make it much harder for you to actually concentrate on what you’re doing, and no amount of careful contingency planning can compensate for that. At Server Density we’re keenly aware that employee health and well being is critical to maintaining business infrastructure, especially in the event of a crisis. That’s why we support movements like HumanOps, which promote a wider awareness of the importance of employee health, from the importance of taking regular breaks to ergonomic keyboards. All too often people working in IT forget that the most business-critical hardware they look after isn’t servers or routers, it’s the health and well being of the people on the front lines looking after these systems. Cyber attacks are stressful on everyone working in an organisation, and the IT teams take the brunt of the strain. However, with careful planning, clear lines of delegation and an appreciation of the importance of looking after each other’s health, developers and operations specialists should be able to weather the storm effectively and recover business assets effectively. Source: https://jaxenter.com/can-prepare-cyber-attack-133447.html
Read More:
How can you prepare for a cyber attack?


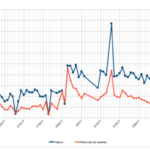 The Hajime malware is competing with the Mirai malware to enslave some IoT devices Mirai — a notorious malware that’s been enslaving IoT devices — has competition. A rival piece of programming has been infecting some of the same easy-to-hack internet-of-things products, with a resiliency that surpasses Mirai, according to security researchers. “You can almost call it Mirai on steroids,” said Marshal Webb, CTO at BackConnect, a provider of services to protect against distributed denial-of-service (DDoS) attacks. Security researchers have dubbed the rival IoT malware Hajime, and since it was discovered more than six months ago, it’s been spreading unabated and creating a botnet. Webb estimates it’s infected about 100,000 devices across the globe. These botnets, or networks of enslaved computers, can be problematic. They’re often used to launch massive DDoS attacks that can take down websites or even disrupt the internet’s infrastructure. That’s how the Mirai malware grabbed headlines last October. A DDoS attackfrom a Mirai-created botnet targeted DNS provider Dyn, which shut down and slowed internet traffic across the U.S. Hajime was first discovered in the same month, when security researchers at Rapidity Networks were on the lookout for Mirai activity. What they found instead was something similar, but also more tenacious. Like Mirai, Hajime also scans the internet for poorly secured IoT devices like cameras, DVRs, and routers. It compromises them by trying different username and password combinations and then transferring a malicious program. However, Hajime doesn’t take orders from a command-and-control serverlike Mirai-infected devices do. Instead, it communicates over a peer-to-peernetwork built off protocols used in BitTorrent, resulting in a botnet that’s more decentralized — and harder to stop. “Hajime is much, much more advanced than Mirai,” Webb said. “It has a more effective way to do command and control.” Broadband providers have been chipping away at Mirai-created botnets, by blocking internet traffic to the command servers they communicate with. In the meantime, Hajime has continued to grow 24/7, enslaving some of the same devices. Its peer-to-peer nature means many of the infected devices can relay files or instructions to rest of the botnet, making it more resilient against any blocking efforts. Hajime infection attempts (blue) vs Mirai infection attempts (red), according to a honeypot from security researcher Vesselin Bontchev. Who’s behind Hajime? Security researchers aren’t sure. Strangely, they haven’t observed the Hajime botnet launching any DDoS attacks — which is good news. A botnet of Hajime’s scope is probably capable of launching a massive one similar to what Mirai has done. “There’s been no attribution. Nobody has claimed it,” said Pascal Geenens, a security researcher at security vendor Radware. However, Hajime does continue to search the internet for vulnerable devices. Geenens’ own honeypot, a system that tracks botnet activity, has been inundated with infection attempts from Hajime-controlled devices, he said. So the ultimate purpose of this botnet remains unknown. But one scenario is it’ll be used for cybercrime to launch DDoS attacks for extortion purposes or to engage in financial fraud. “It’s a big threat forming,” Geenens said. “At some point, it can be used for something dangerous.” It’s also possible Hajime might be a research project. Or in a possible twist, maybe it’s a vigilante security expert out to disrupt Mirai. So far, Hajime appears to be more widespread than Mirai, said Vesselin Bontchev, a security expert at Bulgaria’s National Laboratory of Computer Virology. However, there’s another key difference between the two malware. Hajime has been found infecting a smaller pool of IoT devices using ARM chip architecture. That contrasts from Mirai, which saw its source code publicly released in late September. Since then, copycat hackers have taken the code and upgraded the malware. Vesselin has found Mirai strains infecting IoT products that use ARM, MIPS, x86, and six other platforms. That means the clash between the two malware doesn’t completely overlap. Nevertheless, Hajime has stifled some of Mirai’s expansion. “There’s definitely an ongoing territorial conflict,” said Allison Nixon, director of security research at Flashpoint. To stop the malware, security researchers say it’s best to tackle the problem at its root, by patching the vulnerable IoT devices. But that will take time and, in other cases, it might not even be possible. Some IoT vendors have released security patches for their products to prevent malware infections, but many others have not, Nixon said. That means Hajime and Mirai will probably stick around for a long time, unless those devices are retired. “It will keep going,” Nixon said. “Even if there’s a power outage, [the malware] will just be back and re-infect the devices. It’s never going to stop.” Source: http://www.itworld.com/article/3190181/security/iot-malware-clashes-in-a-botnet-territory-battle.html
The Hajime malware is competing with the Mirai malware to enslave some IoT devices Mirai — a notorious malware that’s been enslaving IoT devices — has competition. A rival piece of programming has been infecting some of the same easy-to-hack internet-of-things products, with a resiliency that surpasses Mirai, according to security researchers. “You can almost call it Mirai on steroids,” said Marshal Webb, CTO at BackConnect, a provider of services to protect against distributed denial-of-service (DDoS) attacks. Security researchers have dubbed the rival IoT malware Hajime, and since it was discovered more than six months ago, it’s been spreading unabated and creating a botnet. Webb estimates it’s infected about 100,000 devices across the globe. These botnets, or networks of enslaved computers, can be problematic. They’re often used to launch massive DDoS attacks that can take down websites or even disrupt the internet’s infrastructure. That’s how the Mirai malware grabbed headlines last October. A DDoS attackfrom a Mirai-created botnet targeted DNS provider Dyn, which shut down and slowed internet traffic across the U.S. Hajime was first discovered in the same month, when security researchers at Rapidity Networks were on the lookout for Mirai activity. What they found instead was something similar, but also more tenacious. Like Mirai, Hajime also scans the internet for poorly secured IoT devices like cameras, DVRs, and routers. It compromises them by trying different username and password combinations and then transferring a malicious program. However, Hajime doesn’t take orders from a command-and-control serverlike Mirai-infected devices do. Instead, it communicates over a peer-to-peernetwork built off protocols used in BitTorrent, resulting in a botnet that’s more decentralized — and harder to stop. “Hajime is much, much more advanced than Mirai,” Webb said. “It has a more effective way to do command and control.” Broadband providers have been chipping away at Mirai-created botnets, by blocking internet traffic to the command servers they communicate with. In the meantime, Hajime has continued to grow 24/7, enslaving some of the same devices. Its peer-to-peer nature means many of the infected devices can relay files or instructions to rest of the botnet, making it more resilient against any blocking efforts. Hajime infection attempts (blue) vs Mirai infection attempts (red), according to a honeypot from security researcher Vesselin Bontchev. Who’s behind Hajime? Security researchers aren’t sure. Strangely, they haven’t observed the Hajime botnet launching any DDoS attacks — which is good news. A botnet of Hajime’s scope is probably capable of launching a massive one similar to what Mirai has done. “There’s been no attribution. Nobody has claimed it,” said Pascal Geenens, a security researcher at security vendor Radware. However, Hajime does continue to search the internet for vulnerable devices. Geenens’ own honeypot, a system that tracks botnet activity, has been inundated with infection attempts from Hajime-controlled devices, he said. So the ultimate purpose of this botnet remains unknown. But one scenario is it’ll be used for cybercrime to launch DDoS attacks for extortion purposes or to engage in financial fraud. “It’s a big threat forming,” Geenens said. “At some point, it can be used for something dangerous.” It’s also possible Hajime might be a research project. Or in a possible twist, maybe it’s a vigilante security expert out to disrupt Mirai. So far, Hajime appears to be more widespread than Mirai, said Vesselin Bontchev, a security expert at Bulgaria’s National Laboratory of Computer Virology. However, there’s another key difference between the two malware. Hajime has been found infecting a smaller pool of IoT devices using ARM chip architecture. That contrasts from Mirai, which saw its source code publicly released in late September. Since then, copycat hackers have taken the code and upgraded the malware. Vesselin has found Mirai strains infecting IoT products that use ARM, MIPS, x86, and six other platforms. That means the clash between the two malware doesn’t completely overlap. Nevertheless, Hajime has stifled some of Mirai’s expansion. “There’s definitely an ongoing territorial conflict,” said Allison Nixon, director of security research at Flashpoint. To stop the malware, security researchers say it’s best to tackle the problem at its root, by patching the vulnerable IoT devices. But that will take time and, in other cases, it might not even be possible. Some IoT vendors have released security patches for their products to prevent malware infections, but many others have not, Nixon said. That means Hajime and Mirai will probably stick around for a long time, unless those devices are retired. “It will keep going,” Nixon said. “Even if there’s a power outage, [the malware] will just be back and re-infect the devices. It’s never going to stop.” Source: http://www.itworld.com/article/3190181/security/iot-malware-clashes-in-a-botnet-territory-battle.html