Today is Black Friday in the U.S. a retail holiday where numerous, extravagant deals are revealed to a ravenous public. In the brick and mortar universe, this can become a free-for-all when shoppers will camp out for days in front of a store just to get in on the first deals. In the cyber universe the same greatly increase traffic can be seen and this also makes it hunting season for hackers and extortionists attempting to get a cut. On the Internet, the easiest and lowest form of disruption is the distributed denial of service (DDoS) attack and we’ve seen it employed throughout the year by for various reasons to take down websites. To get a better understanding of what e-retailers can expect now on Black Friday and the upcoming Cyber Monday, SiliconANGLE reached out to Nexusguard (Nexusguard Limited), DDoS protection experts, and spoke with their Chief Scientist Terrence Gareau. “Risk from cyberattack is a trend repeating every year,” says Gareau. “No doubt retailers all experience an uptick in attacks [during Black Friday]. Attackers are definitely taking advantage of the uptick and e-tailers need to put in more resources to boost their websites’ security.” This year DDoS attacks hit record highs, according to the State of the Internet report from Akamai for Q2 2015. The number of attacks grew by 132 percent compared to the same time in 2014 and 12 attacks occurred that exceeded 1,000 gigabits per second (Gbps). Nexusguard’s own overwatch on DDoS showed that during 2015 Q3 attack numbers rose by 53 percent over Q2, higher than any quarter over the past two years. E-commerce at more risk than ever from DDoS attacks Most DDoS attacks that make it to the news are being done my Internet mayhem groups looking for fame and attention. The most recent example is the attack committed by Lizard Squad on Christmas Day, December 26, 2014 against the Xbox LIVE and PlayStation networks that knocked the gaming services offline for millions of customers However, Gareau says that not all DDoS attacks come from people seeking attention—some are seeded with greed and extortion. Especially when it comes to the lesser-known attacks that services and e-retailers suffer around this time of year. When asked if competitors might use DDoS to knock out or weaken sales from other e-retailers, Nexusguard’s chief scientist would only say that it does appear that competitors do attack each other this time of year. That said, more danger appears to be coming from extortion rackets this time of year than from greedy competitors. The usual strategy is to hit an outlet with a DDoS attack (a short one) and then send an e-mail requesting some sort of ransom payment or the attack comes back. A few more blasts might come along to get the target’s attention. “Hackers are aware that the holidays are a prime time for online retailers. Therefore, they would do anything to break through any defenses,” says Gareau. This time of year criminals know that stores and e-retailers are looking to make as much money as possible off traffic. As well, increased traffic makes servers even more vulnerable to DDoS because it means they’re already working at capacity. Attackers see this as low-hanging fruit because first it’s easier and second an e-retailer will lose a great deal of money for even ten minutes of time offline during the sales rush. “One of the most sophisticated attacks focused on the login prompt,” Gareau adds, when asked for an example of how hackers attempt to knock sites offline. “In fact, on Thanksgiving and Christmas last year, we saw a hacker craft specific requests to the login form, preventing visitors from logging on.” Cold advice about DDoS extortion: “…don’t f**ing pay ‘em.” “We expect to see an increase in fraud and extortion, directly linked to DDoS as seen over the last few years,” Gareau says. When it comes to handling the potential of (or ongoing) DDoS attacks, Gareau suggests getting a proper team on board, he works for such a team at Nexusguard after all, but he also has an opinion on extortion and it’s a very simple one: “…And don’t f**ing pay ‘em,” he adds. This year has a perfect example of why paying DDoS extortion is a losing bet. In early November Switzerland-based ProtonMail, a provider of end-to-end encrypted e-mail, was struck by a powerful DDoS attack and the attackers demanded a ransom of $6,000 to relent. (The amount requested was 15 bitcoins, which at the time came out to approximately $5,850.) ProtonMail paid the ransom but then paid the price: the ProtonMail website and service were washed away by a DDoS attack anyway. Paying extortion to make a DDoS attacker go away does not necessarily make them go away. Just like any other criminal enterprise, knowing that a payment will come is a good way to make sure they will come back. Worse, it will fund the criminals to build out or increase their total power, which means they can go after other targets more frequently. In many cases that ransom requested by the criminals behind the DDoS could be paid to an anti-DDoS outfit and used to lessen the impact of the attack. The result is that the criminals get nothing but time wasted firing off their attack tools. Source: http://siliconangle.com/blog/2015/11/27/its-black-friday-do-you-know-who-is-ddosing-your-servers-and-how-to-stop-them/
Read more here:
It’s Black Friday: Do you know who is DDoSing your servers? And how to stop them


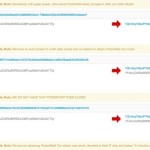 Cyber-crime syndicates are moving in, pushing script kiddies out of the picture, expect more large-scale attacks After the success of DDoSing outfits like DD4BC and Armada Collective, an unknown copycat that’s using the Armada Collective name but asking for astronomical payments has appeared. A report from Recorded Future, a real-time threat intelligence protection company, shows that DDoS-for-Bitcoin extortion schemes are here to stay, with more and more attacks being launched solely for this reason. DD4BC have launched a new type of extortion scheme This trend can be tracked down to an Akamai report released over the summer that documented the actions of a hacking group known as DD4BC (DDoS 4 Bitcoin). This group launched DDoS attacks on companies around the world, requesting small payments in Bitcoin for each target. The group’s scheme was a simple one. They would send threatening emails to business owners, saying they would launch powerful DDoS attacks if a ransom was not paid in due time to a specific Bitcoin wallet. To prove their point, a small 15-minute DDoS was launched to showcase their capabilities. DD4BC’s scheme proved to be extremely lucrative and allowed them to rack up Bitcoin over the past year in over 140 DDoS attacks. The group was active since late 2014 and suddenly stopped its activity after the Akamai report was released, probably to avoid getting caught by law enforcement authorities alerted to their scheme. Enter Armada Collective Soon after, the first DD4BC copycat arose, in the form of the Armada Collective hackers, carrying out DDoS attacks on small businesses in Switzerland. They then expanded to email providers, and their name became known around the world in the famous ProtonMail incident. The incident is very well documented in one of our previous stories , but we’ll give you a small summary. Basically, Armada Collective followed the DD4BC regular tactics, sending an email and launching a small 10-15 Gbps DDoS attack on ProtonMail. Armada Collective returning ransom to ProtonMail As soon as the attack ended, ProtonMail revealed what happened, and more serious attacks took place, with ProtonMail paying the ransom in the end. Armada Collective denied any involvement and even went as far as to return the ProtonMail ransom, putting the blame on a state-sponsored actor with capabilities that far exceeded its own. Enter the unknown copycat But something else happened recently that made the Recorded Future team stop and ponder about the bigger picture, and that’s the DDoS-for-Bitcoin attacks on three major Greek banks . With DD4BC and Armada Collective always launching small-scale attacks and requesting modest ransoms (the equivalent of a few thousand dollars), this new group attacking Greek banks does not fit the bill. While the attacks of DD4BC and Armada Collective seem to be the work of script kiddies, the ones that brought down ProtonMail and the three major Greek banks were massive in scale. Coupled with the fact that this new group also requests ransoms in the order of millions of dollars, there are clear signs that they are a copycat that’s trying to remain hidden by passing as Armada Collective (as stated in the email sent to the Greek banks). With the number of DDoS-for-Bitcoin attacks on the rise, this type of cyber-threat is about to evolve from the work of script kiddies to the normal MO of larger cyber-criminal syndicates.
Cyber-crime syndicates are moving in, pushing script kiddies out of the picture, expect more large-scale attacks After the success of DDoSing outfits like DD4BC and Armada Collective, an unknown copycat that’s using the Armada Collective name but asking for astronomical payments has appeared. A report from Recorded Future, a real-time threat intelligence protection company, shows that DDoS-for-Bitcoin extortion schemes are here to stay, with more and more attacks being launched solely for this reason. DD4BC have launched a new type of extortion scheme This trend can be tracked down to an Akamai report released over the summer that documented the actions of a hacking group known as DD4BC (DDoS 4 Bitcoin). This group launched DDoS attacks on companies around the world, requesting small payments in Bitcoin for each target. The group’s scheme was a simple one. They would send threatening emails to business owners, saying they would launch powerful DDoS attacks if a ransom was not paid in due time to a specific Bitcoin wallet. To prove their point, a small 15-minute DDoS was launched to showcase their capabilities. DD4BC’s scheme proved to be extremely lucrative and allowed them to rack up Bitcoin over the past year in over 140 DDoS attacks. The group was active since late 2014 and suddenly stopped its activity after the Akamai report was released, probably to avoid getting caught by law enforcement authorities alerted to their scheme. Enter Armada Collective Soon after, the first DD4BC copycat arose, in the form of the Armada Collective hackers, carrying out DDoS attacks on small businesses in Switzerland. They then expanded to email providers, and their name became known around the world in the famous ProtonMail incident. The incident is very well documented in one of our previous stories , but we’ll give you a small summary. Basically, Armada Collective followed the DD4BC regular tactics, sending an email and launching a small 10-15 Gbps DDoS attack on ProtonMail. Armada Collective returning ransom to ProtonMail As soon as the attack ended, ProtonMail revealed what happened, and more serious attacks took place, with ProtonMail paying the ransom in the end. Armada Collective denied any involvement and even went as far as to return the ProtonMail ransom, putting the blame on a state-sponsored actor with capabilities that far exceeded its own. Enter the unknown copycat But something else happened recently that made the Recorded Future team stop and ponder about the bigger picture, and that’s the DDoS-for-Bitcoin attacks on three major Greek banks . With DD4BC and Armada Collective always launching small-scale attacks and requesting modest ransoms (the equivalent of a few thousand dollars), this new group attacking Greek banks does not fit the bill. While the attacks of DD4BC and Armada Collective seem to be the work of script kiddies, the ones that brought down ProtonMail and the three major Greek banks were massive in scale. Coupled with the fact that this new group also requests ransoms in the order of millions of dollars, there are clear signs that they are a copycat that’s trying to remain hidden by passing as Armada Collective (as stated in the email sent to the Greek banks). With the number of DDoS-for-Bitcoin attacks on the rise, this type of cyber-threat is about to evolve from the work of script kiddies to the normal MO of larger cyber-criminal syndicates.