Anonymous vs ISIS Naturally, even cybersecurity news in this past week has centred around ISIS in the wake of the Paris attacks. The main headline has come from Anonymous, who have again but more formally waged ‘war’ on ISIS themselves. So far their efforts seem to have focused on communication; deleting thousands of Twitter accounts they believe are associated with the terrorist group. One notable aspect of how ISIS recruit supporters is through social media such as Twitter and Facebook, with an estimated 46,000 affiliated Twitter accounts. The move by Anonymous was announced immediately after ISIS dubbed the group ‘idiots’ and began circulating some useless cybersecurity advice to its followers via messaging app Telegram. Anonymous’s efforts, dubbed #OpParis are likely to irritate the group and possibly damage their recruitment opportunities. Australian attorney general warns terrorism means privacy will suffer Australian Attorney General George Brandis has said that Australians should expect ‘greater impediments to personal privacy’ in the wake of the Paris attacks. Measures have already become more strict under his tenure, with legislation passed to collect call records, IP addresses, location and billing information but it remains to be seen what further changes might be made. He also said during the interview by Nine Network that the situation with ISIS was tantamount to war. UK warns terrorists are targeting hospitals, power stations and air traffic control In an address at GCHQ (Government Communication Headquarters, a branch of British intelligence), chancellor George Osborne warned that terrorists will also be making efforts to target national infrastructure in order to carry out attacks. He also said that the government intend to double cybersecurity spending over the next five years. While we know such attacks are possible, we are yet to see terrorist groups like ISIS leverage this type of capability. NTP being made more secure to avoid DDoS exploits A new beta version of the Network Time Protocol (NTPsec) has been released, in efforts to avoid exploitation in DDoS attacks. Currently only available for open source use and feedback, the protocols codebase has been greatly streamlined; reduced from 30,000 lines of code to just 884. One of the project’s lead developers Eric S Raymond said: ‘The most important change you can’t see is that the code has been very seriously security-hardened, not only by plugging all publicly disclosed holes but by internal preventive measures to close off entire classes of vulnerabilities.’ Hackers offer 200,000 Comcast user passwords for sale Hackers have offered 200,000 Comcast user passwords for sale on the dark web, leading to a mass password reset from the company. What’s interesting in this case is that this was not a breach, but the result of users being duped into revealing their passwords themselves. Fortunately, Comcast’s own security officer discovered the passwords up for sale and initiated the mass reset before any accounts were known to be exploited. A reminder to be more careful with our password management! Vodafone reveal breach as further arrests made in TalkTalk case In the wake of the large TalkTalk breach and as a third man was arrested in the case, Vodafone announced their own breach. Affecting just 1827 users, who have all since been informed, Vodafone have not revealed how the attack was carried out. The number of customers affected by the TalkTalk breach has now been revised; originally given as 4 million, the number is now down to 1.2 million. In addition to usernames, emails and passwords 21,000 of these included bank account details and 28,000 credit card details. Source: https://www.acunetix.com/blog/articles/in-the-headlines-anonymous-vs-isis-australian-attorney-general-ntp-and-ddos-exploits/
Follow this link:
Anonymous vs ISIS, Australian attorney general, NTP and DDoS exploits


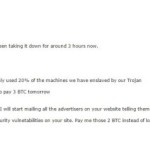 Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml
Two sister blogs, Hacked (Security & Tech) and CryptoCoinsNews, have decided to go the Mel Gibson route (“Ransom” movie reference for the uncool kids) and put out a bounty on DDoS attackers instead of paying the money they were asking for. It all started earlier this morning, when both sites saw a serious DDoS attack being carried out against their server infrastructure. Three hours after the attack began, the two received emails from a man named Jon. The attacker claimed to own a botnet that he intended to use for DDoS attacks. He said that currently he was using only 20% of the botnet’s capabilities against the two sites. Jon was asking for a 2 Bitcoin ransom, which would become 3 Bitcoin by tomorrow if unpaid. Instead of giving in and being intimidated by the attacker, the two sites ramped up their DDoS mitigation and decided to put out a 5 Bitcoin ransom on the attacker, which is about $1,600 or €1,500 in today’s exchange rate. Turning the table on DDoS extortionists “If you can help us identify the extortionists in a way that leads to a successful police report, you will receive five bitcoins, with gratitude,” says Samburaj Das of CCN and Hacked. The bloggers are looking for data like real names, addresses, and attacks carried out on other sites that would allow investigators to track their DDoS campaign. Details should be sent to crypto@cryptocoinsnews.com. Only last month something similar happened to ProtonMail, a crypto email service. The site was under a massive DDoS attack, which also expanded to its ISP. Due to peer pressure from other affected services, ProtonMail paid the ransom , but the attacks never stopped, with other groups also taking aim at their infrastructure. Many people skewered ProtonMail’s owners for paying the attackers, saying it was a bad idea and did nothing but encourage such types of groups to carry on with their DDoS-for-Bitcoin extortion campaigns . We’ll just have to wait and see how Hacked/CCN’s countermove goes through. Source: http://news.softpedia.com/news/bloggers-put-bounty-on-ddos-extortionists-496586.shtml