The attacks were aimed at two GitHub-hosted projects fighting Chinese censorship Software development platform GitHub said Sunday it was still experiencing intermittent outages from the largest cyberattack in its history but had halted most of the attack traffic. Starting on Thursday, GitHub was hit by distributed denial-of-service (DDoS) attacks that sent large volumes of Web traffic to the site, particularly toward two Chinese anti-censorship projects hosted there. Over the next few days, the attackers changed their DDoS tactics as GitHub defended the site, but as of Sunday, it appears the site was mostly working. A GitHub service called Gists, which lets people post bits of code, was still affected, it said. On Twitter, GitHub said it continued to adapt its defenses. The attacks appeared to focus specifically on two projects hosted on GitHub, according to a blogger who goes by the nickname of Anthr@X on a Chinese- and English-language computer security forum. One project mirrors the content of The New York Times for Chinese users, and the other is run by Greatfire.org, a group that monitors websites censored by the Chinese government and develops ways for Chinese users to access banned services. China exerts strict control over Internet access through its “Great Firewall,” a sophisticated ring of networking equipment and filtering software. The country blocks thousands of websites, including ones such as Facebook and Twitter and media outlets such as The Wall Street Journal, The New York Times and Bloomberg. Anthr@X wrote that it appeared advertising and tracking code used by many Chinese websites appeared to have been modified in order to attack the GitHub pages of the two software projects. The tracking code was written by Baidu, but it did not appear the search engine — the largest in China — had anything to do with it. Instead, Anthr@X wrote that some device on the border of China’s inner network was hijacking HTTP connections to websites within the country. The Baidu tracking code had been replaced with malicious JavaScript that would load the two GitHub pages every two seconds. In essence, it means the attackers had roped in regular Internet users into their attacks without them knowing. “In other words, even people outside China are being weaponized to target things the Chinese government does not like, for example, freedom of speech,” Anthr@X wrote. GitHub has not laid blame for the attacks, writing on Saturday that “based on reports we’ve received, we believe the intent of this attack is to convince us to remove a specific class of content.” The attackers used a wide variety of methods and tactics, including new techniques “that use the web browsers of unsuspecting, uninvolved people to flood github.com with high levels of traffic,” GitHub said. In late December, China cut off all access to Google’s Gmail service, after blocking Facebook’s Instagram app, and the phone messaging app Line. A month prior, it appeared many non-political sites supported by the U.S. content delivery network EdgeCast Network were blocked. EdgeCast may have been a casualty because its cloud services are often used to host mirror sites for ones that have been banned. Source: http://www.computerworld.com/article/2903318/github-recovering-from-massive-ddos-attacks.html
Originally posted here:
GitHub recovering from massive DDoS attacks

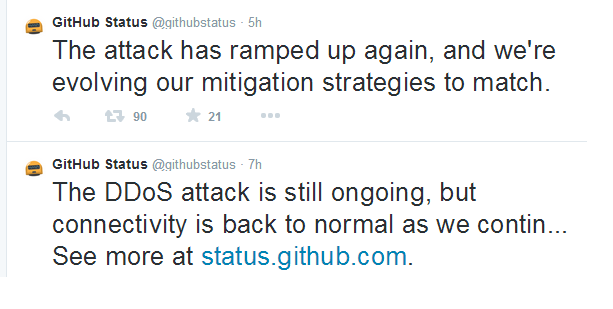
 San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/
San Francisco-based GitHub was taken out with a denial of service attack Wednesday. Scripts from the Beijing-based Baidu sent traffic coming to a page operated by GreatFire and a page with Chinese-translations of The New York Times. As is the focus of DDoS attacks, GitHub’s availability was knocked out as a result of the traffic caused. In morning tweets during the attack, GitHub informed followers that the attack was still going and getting worse, but that they were on top of dealing with it. As of two hours ago GitHub states that the DDoS attack is still being worked on. Meanwhile Baidu has said that it had nothing to do with the attack intentionally. The Chinese search engine titan also says that it is working security specialists to find out the cause of things. The company made certain to state that its security hadn’t been compromised during the attack on GitHub. Speculation in tech and security circles say that the attack was a means of strengthening China’s methods of web censorship by taking out sites that could allow for users to get around it. Baidu was simply used as a means of amplifying the attack due to how sizable it is and the amount of traffic it can produce. Source: http://kabirnews.com/github-still-battling-ddos-attack/8495/