Earlier this year, a WordPress XML-RPC exploit was used to launch distributed denial-of-service (DDoS) and brute force attacks against WordPress websites. As WordPress continues to grow in popularity and gain an increasing share of the market for website content management systems (CMS), such attacks have proliferated and pose an ongoing security risk that WordPress developers and website owners must address. Distributed Denial-of-Service Attacks In the case of DDoS attacks, the intent of attackers is to disrupt a website or service by flooding it with information and traffic. According to the U.S. Computer Emergency Readiness Team (US-CERT): “In a denial-of-service (DoS) attack, an attacker attempts to prevent legitimate users from accessing information or services. By targeting your computer and its network connection, or the computers and network of the sites you are trying to use, an attacker may be able to prevent you from accessing email, websites, online accounts (banking, etc.), or other services that rely on the affected computer.” Typically, larger scale DDoS attacks involve the use of multiple computer systems, websites, and servers that have been compromised and can be controlled remotely by the attackers. These networks are known as botnets and can include hundreds or even thousands of compromised systems. However, a simpler denial-of-service attack (DoS) can be launched from a single computer and potentially disrupt a website or service with only a small-scale effort. In either case, WordPress sites can be compromised and used for this purpose, and, in one of the largest cases earlier this year, more than 162,000 WordPress sites were used in just a single DDoS attack. Brute Force Attacks In brute force attacks, the intent is to gain access to a website or service rather than disrupt it. Typically, attackers use various methods to automate the submission of login and authentication requests in an attempt to defeat a site or service’s security and gain access to user accounts, the administrative account, and ultimately the underlying server and architecture. According to the Open Web Application Security Project (OWASP): “A brute force attack can manifest itself in many different ways, but primarily consists in an attacker configuring predetermined values, making requests to a server using those values, and then analyzing the response. For the sake of efficiency, an attacker may use a dictionary attack (with or without mutations) or a traditional brute-force attack (with given classes of characters e.g.: alphanumeric, special, case (in)sensitive). Considering a given method, number of tries, efficiency of the system which conducts the attack, and estimated efficiency of the system which is attacked the attacker is able to calculate approximately how long it will take to submit all chosen predetermined values.” In WordPress brute force attacks, attackers can potentially identify a user’s password and use it to access the user’s account on the WordPress site and on other sites where the user may have the same ID and password. If the WordPress site contains any personal information, payment details for e-commerce, or other sensitive data tied to the user’s account, then attackers may be able to steal it. Worst of all, if attackers can gain access to the administrative account for a WordPress site, then they may be able to compromise, shut down, or delete the entire website, deploy malicious code, or steal or delete entire databases of sensitive information, including user logins and passwords. WordPress Vulnerability: Pingback and XML-RPC DDoS and brute force attacks against WordPress sites have involved a WordPress pingback exploit and the general vulnerability of WordPress XML-RPC. WordPress uses the XML-RPC interface to allow users to post to their site using many popular Weblog Clients. This functionality can be extended by WordPress plugins, and WordPress offers its own API and supports the Blogger API, metaWeblog API, Movable Type API, and Pingback API. Unfortunately, this same functionality provides exploits that attackers can use to launch attacks, starting with the pingback exploit. Pingback is a linkback method that WordPress site owners and authors can use to request notification when someone links to their posts or pages. When pingback is enabled and an author or administrator of a WordPress site posts content that links to another site, an XML-RPC request is sent to the other site, which automatically sends a pingback to the original site to verify that there is a live, incoming link. Once this is confirmed, the pingback is recorded. According to Daniel Cid, founder and CTO of Securi Inc., a website anti-virus and anti-malware firm, “Any WordPress site with Pingback enabled (which is on by default) can be used in DDOS attacks against other sites.” Using a simple command and an XML-RPC request, an attacker can exploit pingback and potentially use thousands of otherwise legitimate and seemingly harmless WordPress sites to launch a DDoS attack. As reported in a blog post by Cid earlier this year, attackers have now begun using further XML-RPC vulnerabilities and the XML-RPC wp.getUsersBlogs function to conduct large-scale brute force attacks against WordPress sites. Due to the many calls in WordPress XML-RPC that require a username and password, attackers can use a method like wp.getUsersBlogs to test or guess as many passwords as possible and gain access to WordPress administrator accounts or other user accounts. XML-RPC provides a faster method to conduct brute force attacks than using the /wp-login.php to make login attempts, and using XML-RPC is harder to detect. How to Secure Your WordPress Site Against DDoS Attacks WordPress 3.9.2 included a fix that reduces the impact of some DDoS attacks, but, if pingback and XML-RPC are still enabled, they can be exploited. To protect your WordPress website against DDoS attacks, disable pingback and consider disabling XML-RPC entirely, especially if you do not need it or you want to ensure the strongest possible security for your site. WordPress offers instructions for how to globally disable pingback on your site, and two convenient plugins are also available to disable pingback and XML-RPC generally: https://wordpress.org/plugins/disable-xml-rpc-pingback/ https://wordpress.org/plugins/prevent-xmlrpc/ How to Secure Your WordPress Site Against Brute Force Attacks Disabling XML-RPC will remove the possibility of attackers using it to launch brute force attacks, but it does not address the vulnerabilities and risks of brute force attacks against /wp-login.php, and it does not solve the more serious problem of using passwords for user authentication in WordPress. Passwords create arguably the single greatest vulnerability in website and data security. They can be stolen or compromised through a variety of methods, such as brute force hacking, phishing, and malware, and they provide one of the primary incentives for attacks. As long as attackers are able to guess passwords through brute force or steal them in transit or from servers, they can potentially gain access to administrator or user accounts, compromise WordPress sites, and steal data or use them to launch further attacks. Moreover, the storage of passwords or other credentials, even in encrypted form, provides a huge incentive for attackers to target specific WordPress sites and the servers that host them. As Bill Gates declared at a security conference in 2004, passwords “just don’t meet the challenge for anything you really want to secure.” This realization has become more widespread in recent years, especially in the wake of high-profile cyberattacks against retailers like Target and Home Depot or financial institutions and online banking systems. As Google’s manager of information security, Heather Adkins, has put it: “Passwords are dead,” and “the game is over” for relying on passwords as the chief method to secure users and their data. According to WordPress founder Matthew Mullenweg, WordPress site administrators need to implement two-factor authentication in order to protect their sites from brute force attacks and other password vulnerabilities. However, as we explored in our previous blog article, “Choosing the Best and Safest Two-factor Authentication Method”, most solutions for two-factor authentication continue to use passwords as part of the login process, and this perpetuates the underlying problem of passwords. The best way to secure your WordPress site from brute force attacks is to remove passwords and other sensitive credentials from the login process and replace them with simple, mobile authentication that uses public key cryptography. With this approach, there are no passwords or credentials to guess, so brute force attacks are rendered obsolete, and there are no passwords or credentials entered or transmitted during the login process or stored on a server, so phishing and malware are also rendered obsolete. This eliminates the incentive and opportunity for attacks because there is physically nothing that attackers can potentially guess or steal in order to gain access to sites or accounts. As a minimum step toward the strongest possible security, WordPress administrators should enable this next-generation authentication method to protect access to their admin accounts. But the same level of security can be extended to all user accounts for a WordPress site, including self-enrollment that eliminates any need for the admin to set up two-factor authentication for other WordPress users. Source: https://www.secsign.com/wordpress-security-prevent-brute-force-ddos-attacks/
More here:
WordPress Security: Prevent Brute Force and DDoS Attacks

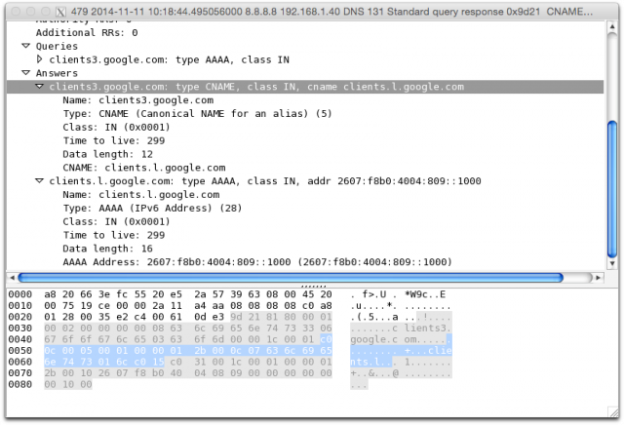
 A new form of Domain Name Service-based distributed denial of service (DDoS) attacks that emerged in October, attacks that can significantly boost the volume of data flung at a targeted server. The method builds upon the well-worn DNS reflection attack method used frequently in past DDoS attacks, exploiting part of the DNS record returned by domain queries to increase the amount of data sent to the target—by stuffing it full of information from President Barack Obama’s press office. DNS reflection attacks (also known as DNS amplification attacks) use forged requests to a DNS server for the Internet Protocol address and other information about a specific host and domain name. For example, a response from Google’s DNS server typically returns something like this—a simple response with the canonical name (CNAME) of the DNS address sent in the request and an IPv4 or IPv6 address for that name: DNS requests are usually sent using the User Datagram Protocol (UDP), which is “connectionless.” It doesn’t require that a connection be negotiated between the requester and the server before data is sent to make sure it’s going to the right place. By forging the return address on the DNS request sent to make it look like it came from the target, an attacker can get a significant boost in the size of a DDoS attack because the amount of data sent in response to the DNS request is significantly larger. But this new attack pumps up the size of the attack further by exploiting the TXT record for a domain—a free-form text entry for a domain name. TXT records are used to provide “time to live” (TTL) information for caching of webpages, configuring anti-spam policies for e-mail service, and verifying ownership of domains being configured for Google Apps and other enterprise services. It can also be used to provide information about other services associated with a domain name. A TXT record for a domain can be up to 255 characters—a significant boost over the relatively small size of the request sent for it. In October, Akamai’s security team noticed a trend in DNS reflection attacks using TXT record requests to the domain “guessinfosys.com” and other malicious domains. The contents for those were not exactly what you’d expect in such a record—they contained text pulled from news releases on WhiteHouse.gov: These attacks lasted for over five hours during each episode, resulting in malicious traffic of up to four gigabits per second hitting their targets. The contents of the TXT records were apparently being updated automatically, possibly scraping data from the WhiteHouse.gov site. DDoS attacks, like many “reflection” attacks, are preventable by DNS server operators by blocking external DNS requests. The attacks can sometimes be stopped at the edge of the network, but that usually requires having more bandwidth available than the size of the attack—something smaller sites without DDoS protection from a content delivery network such as Akamai or CloudFlare may have some difficulty doing. Source: http://arstechnica.com/security/2014/11/dont-blame-obama-but-ddos-attacks-are-now-using-his-press-releases/
A new form of Domain Name Service-based distributed denial of service (DDoS) attacks that emerged in October, attacks that can significantly boost the volume of data flung at a targeted server. The method builds upon the well-worn DNS reflection attack method used frequently in past DDoS attacks, exploiting part of the DNS record returned by domain queries to increase the amount of data sent to the target—by stuffing it full of information from President Barack Obama’s press office. DNS reflection attacks (also known as DNS amplification attacks) use forged requests to a DNS server for the Internet Protocol address and other information about a specific host and domain name. For example, a response from Google’s DNS server typically returns something like this—a simple response with the canonical name (CNAME) of the DNS address sent in the request and an IPv4 or IPv6 address for that name: DNS requests are usually sent using the User Datagram Protocol (UDP), which is “connectionless.” It doesn’t require that a connection be negotiated between the requester and the server before data is sent to make sure it’s going to the right place. By forging the return address on the DNS request sent to make it look like it came from the target, an attacker can get a significant boost in the size of a DDoS attack because the amount of data sent in response to the DNS request is significantly larger. But this new attack pumps up the size of the attack further by exploiting the TXT record for a domain—a free-form text entry for a domain name. TXT records are used to provide “time to live” (TTL) information for caching of webpages, configuring anti-spam policies for e-mail service, and verifying ownership of domains being configured for Google Apps and other enterprise services. It can also be used to provide information about other services associated with a domain name. A TXT record for a domain can be up to 255 characters—a significant boost over the relatively small size of the request sent for it. In October, Akamai’s security team noticed a trend in DNS reflection attacks using TXT record requests to the domain “guessinfosys.com” and other malicious domains. The contents for those were not exactly what you’d expect in such a record—they contained text pulled from news releases on WhiteHouse.gov: These attacks lasted for over five hours during each episode, resulting in malicious traffic of up to four gigabits per second hitting their targets. The contents of the TXT records were apparently being updated automatically, possibly scraping data from the WhiteHouse.gov site. DDoS attacks, like many “reflection” attacks, are preventable by DNS server operators by blocking external DNS requests. The attacks can sometimes be stopped at the edge of the network, but that usually requires having more bandwidth available than the size of the attack—something smaller sites without DDoS protection from a content delivery network such as Akamai or CloudFlare may have some difficulty doing. Source: http://arstechnica.com/security/2014/11/dont-blame-obama-but-ddos-attacks-are-now-using-his-press-releases/