 All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A
All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A
Read More:
A Massive Botnet of CCTV Cameras Involved in Ferocious DDoS Attacks

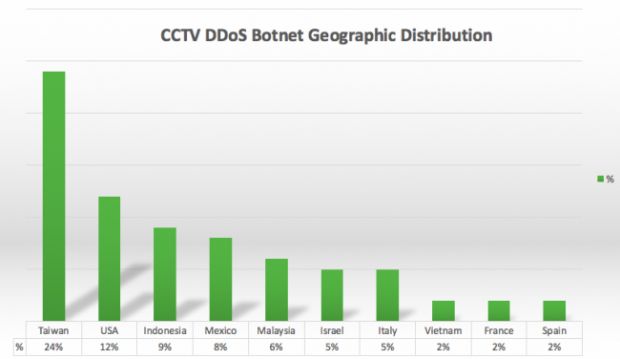
 All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A
All clues lead back to Chinese DVR vendor TVT A botnet of over 25,000 bots lies at the heart of recent DDoS attacks that are ferociously targeting business around the world. More exactly, we’re talking about massive Layer 7 DDoS attacks that are overwhelming Web servers, occupying their resources and eventually crashing websites. US-based security vendor Sucuri discovered this botnet, very active in the last few weeks, and they say it’s mainly composed of compromised CCTV systems from around the world. Their first meeting with the botnet came when a jewelry shop that was facing a prolonged DDoS attack opted to move their website behind Sucuri’s main product, its WAF (Web Application Firewall). Botnet can crank out attacks of 50,000 HTTP requests per second Sucuri thought they had this one covered, just as other cases where companies that move their sites behind their WAF block the attacks, and eventually the attacker moves on to other targets. Instead, they were in for a surprise. While the initial attack was a Layer 7 DDoS with over 35,000 HTTP requests per second hitting the server and occupying its memory with garbage traffic, as soon as the attackers saw the company upgrade their website, they quickly ramped up the attack to 50,000 requests. For Layer 7 attacks, this is an extraordinarily large number, enough to drive any server into the ground. But this wasn’t it. The attackers continued their assault at this high level for days. Botnet’s nature allowed attacks to carry out attacks at higher volumes Usually, DDoS attacks flutter as the bots come online or go offline. The fact that attackers sustained this high level meant their bots were always active, always online. Sucuri’s research into the incident discovered over 25,513 unique IP addresses from where the attacks came. Some of these were IPv6 addresses. The IPs were spread all over the world, and they weren’t originating from malware-infected PCs, but from CCTV systems. Taiwan accounted for a quarter of all compromised IPs, followed by the US, Indonesia, Mexico, and Malaysia. In total, the compromised CCTV systems were located in 105 countries. Top 10 locations of botnet’s IPs The unpatched TVT firmware comes back to haunt us all Of these IPs, 46 percent were assigned to CCTV systems running on the obscure and generic H.264 DVR brand. Other compromised systems were ProvisionISR, Qsee, QuesTek, TechnoMate, LCT CCTV, Capture CCTV, Elvox, Novus, or MagTec CCTV. Sucuri says that all these devices might be linked to Rotem Kerner’s investigation, which discovered a backdoor in the firmware of 70 different CCTV DVR vendors . These companies had bought unbranded DVRs from Chinese firm TVT. When informed of the firmware issues, TVT ignored the researcher, and the issues were never fixed, leading to crooks creating this huge botnet. This is not the first CCTV-based botnet used for DDoS attacks. Incapsula detected a similar botnet last October. The botnet they discovered was far smaller, made up of only 900 bots . Source: http://news.softpedia.com/news/a-massive-botnet-of-cctv-cameras-involved-in-ferocious-ddos-attacks-505722.shtml#ixzz4CsbxFc4A